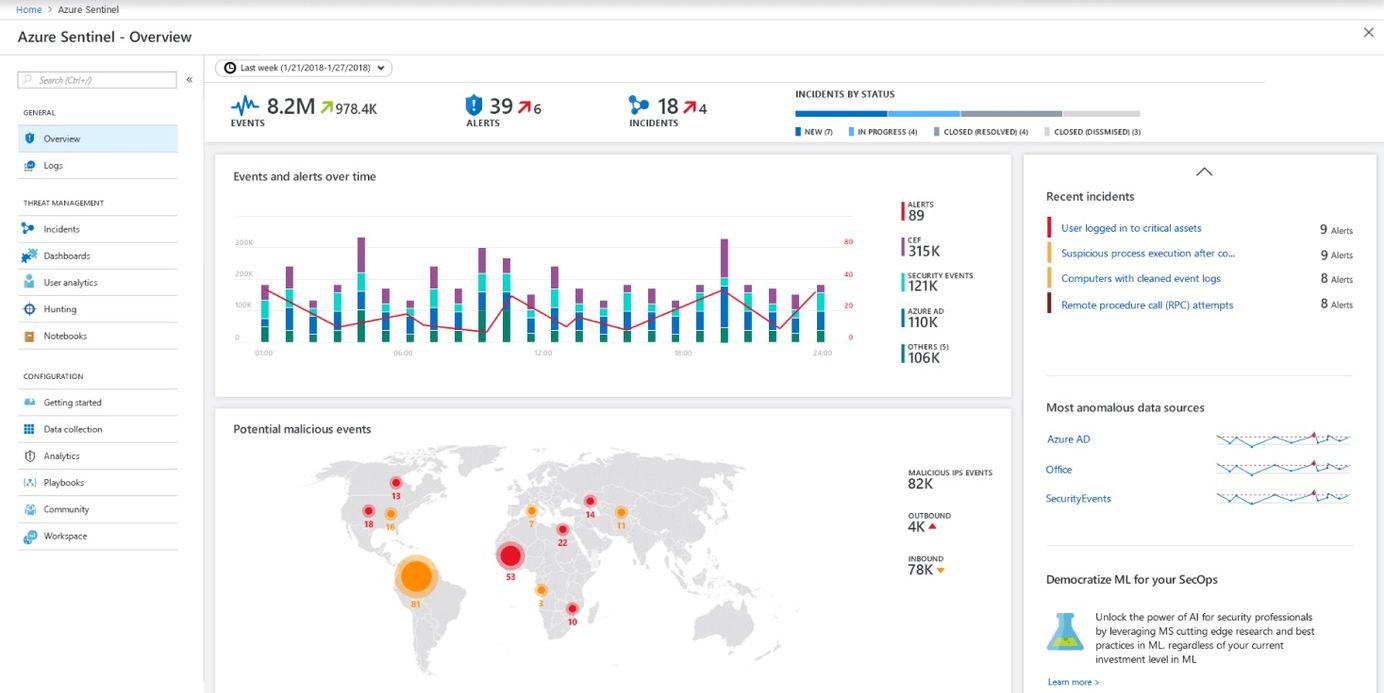
Monitoring Office 365 tenants with Azure Sentinel
Azure Sentinel is a product from Microsoft, offering a cloud-native SIEM service. Sentinel uses clever AI (Artificial Intelligence) to make your threat detection and responses faster and smarter.
A key feature with Azure Sentinel is that you can connect to other data sources. Microsoft has built-in support for ingesting data from a plethora of their own data sources, including:
- Azure AD
- Office 365
- Cloud App Security
- Azure Activity Log
- Azure AD Identity Protection
- Azure Information Protection (AIP)
- Azure Advanced Threat Protection (ATP)
- Azure Security Center
- DNS
- Microsoft Web Application Firewal (WAF)
- Windows Firewall
- Windows Security Events
- and more...
In this post I'll talk about how you can enable Azure Sentinel in your subscription, and then connect it to your Office 365 tenant - this way we can ingest all the juicy data from Office 365 into our Sentinel service for easier and smarter insights.
Update June 2020:
According to updated documentation from Microsoft, you can no longer add additional tenants.
If you had previously connected multiple tenants to Azure Sentinel, using an older version of the Office 365 connector which supported this, you will be able to view and modify which logs you collect from each tenant. You will not be able to add additional tenants, but you can remove previously added tenants.
- https://docs.microsoft.com/en-us/azure/sentinel/connect-office-365#enable-the-office-365-log-connector
Update September 2020:
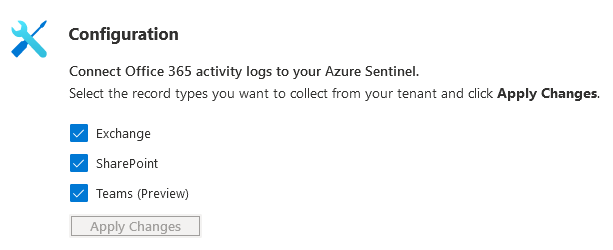
According to updated information from Microsoft, we can now also connect Microsoft Teams under the Office 365 connector. See the picture below.
Configure Azure Sentinel
To start using Azure Sentinel and ingest logs from other data sources we'll need to set up a new workspace. Let's do that now.
In my subscriptions I've found that either using the Search box, or just going the traditional route like this works well "All Services - Azure Sentinel" - I also starred it so it'll appear in my left navigation:
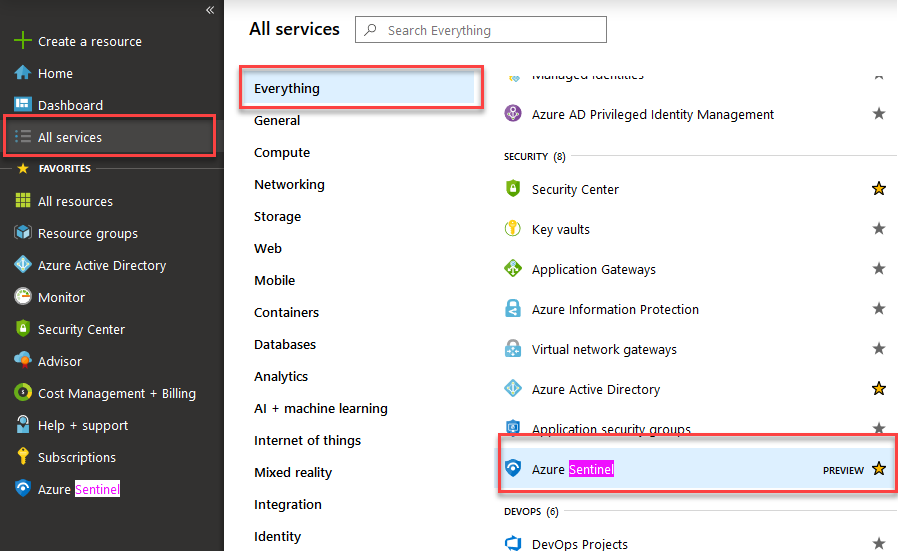
Once you've clicked on Azure Sentinel, you can go ahead and create a new LAW (Log Analytics Workspace). Sentinel does not work with default workspaces from Azure Security Center, which is why they're not listed here.
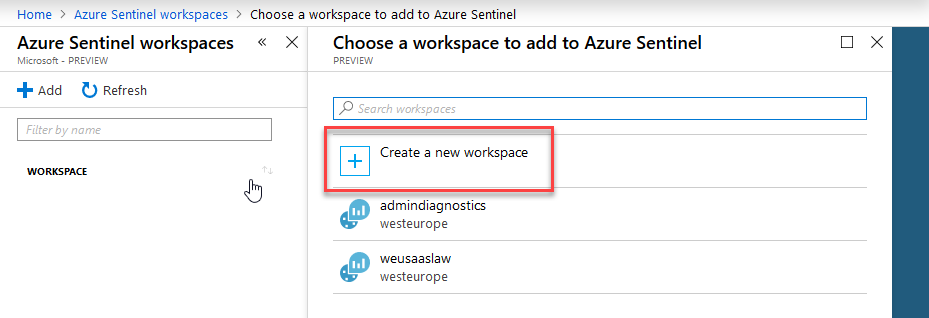
Make the decisions about your naming, resource group and location in the following dialog and click OK. Once this is validated, you can click "Add Azure Sentinel" which will add Sentinel to this new workspace we just created.
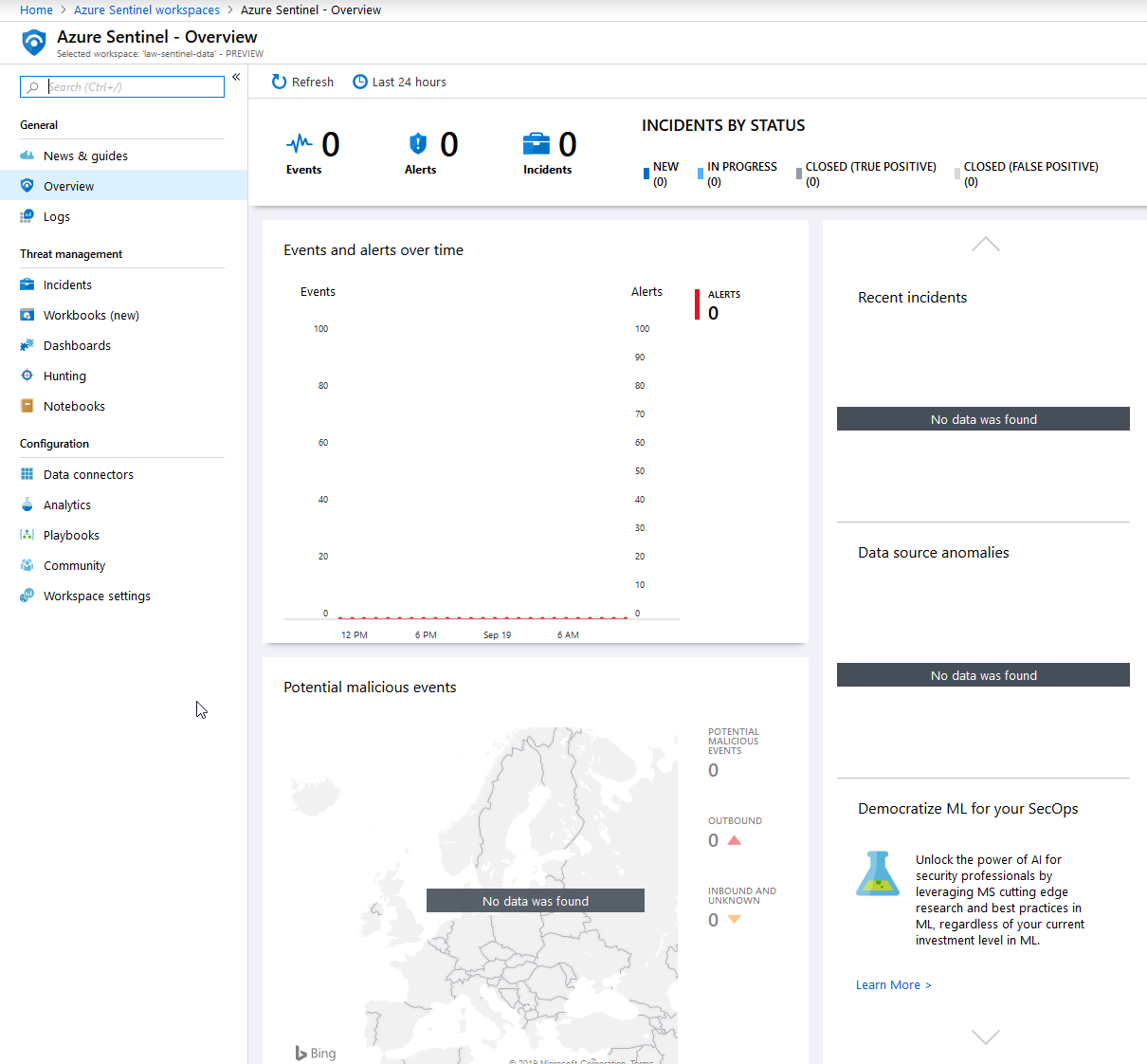
The empty dashboard looks like this, and have a great UI for us to get started:
At this point, we have Azure Sentinel up and runnig and connected to our new LAW (Log Analytics Workspace). Next up: Connect the Office 365 logs.
Connect Office 365 logs to Azure Sentinel
From the new dashboard, you can easily find and connect Office 365 like this:
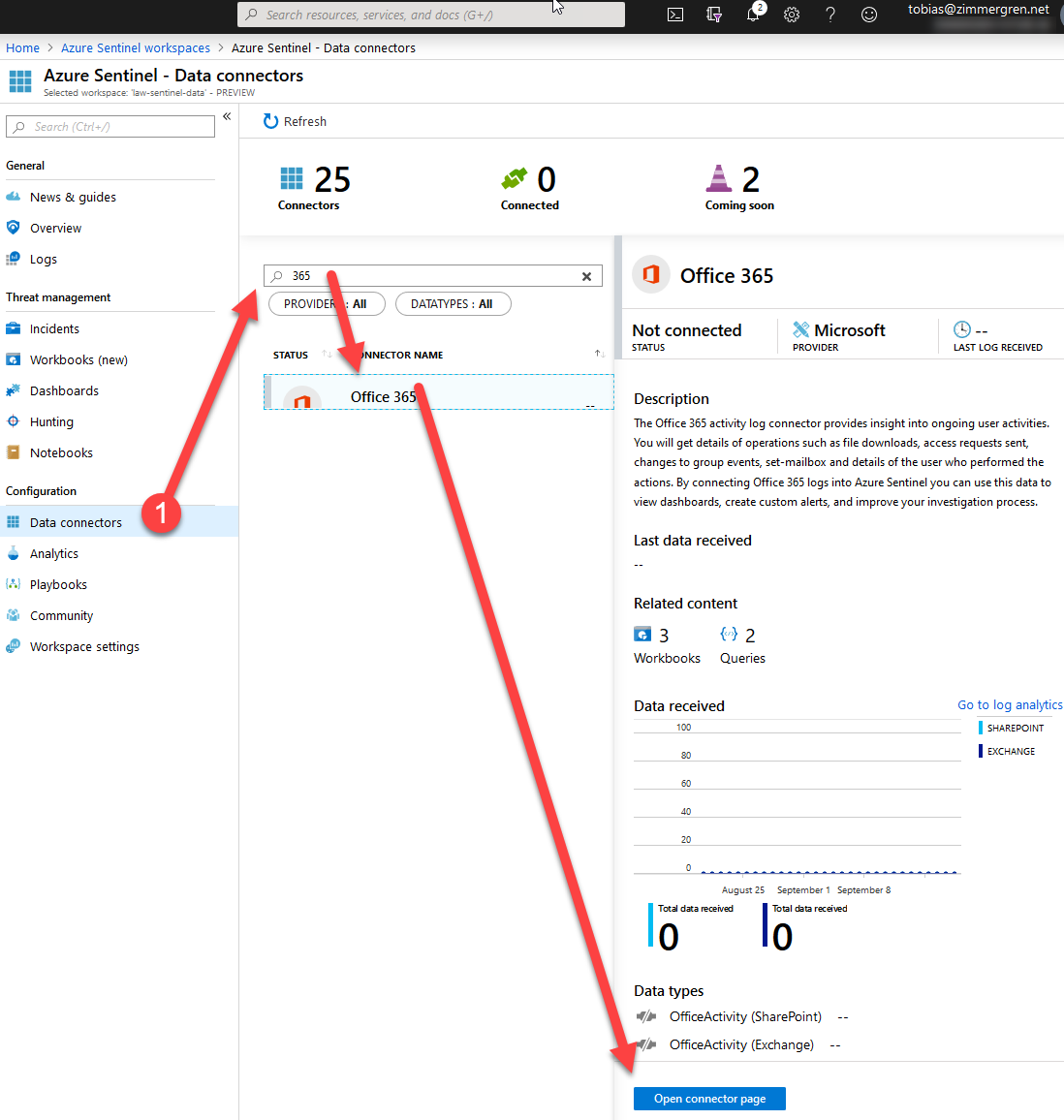
- Data Connectors
- Search for "365" (or any other type of connector)
- Click "Open connector page"
Next up, we can configure the connector and we'll need to install the solution by clicking "Install solution" first, and after that we can start adding our tenants.
Please note that you'll need to be "Global Admin" or "Security Admin" on the workspace's tenant in Azure!
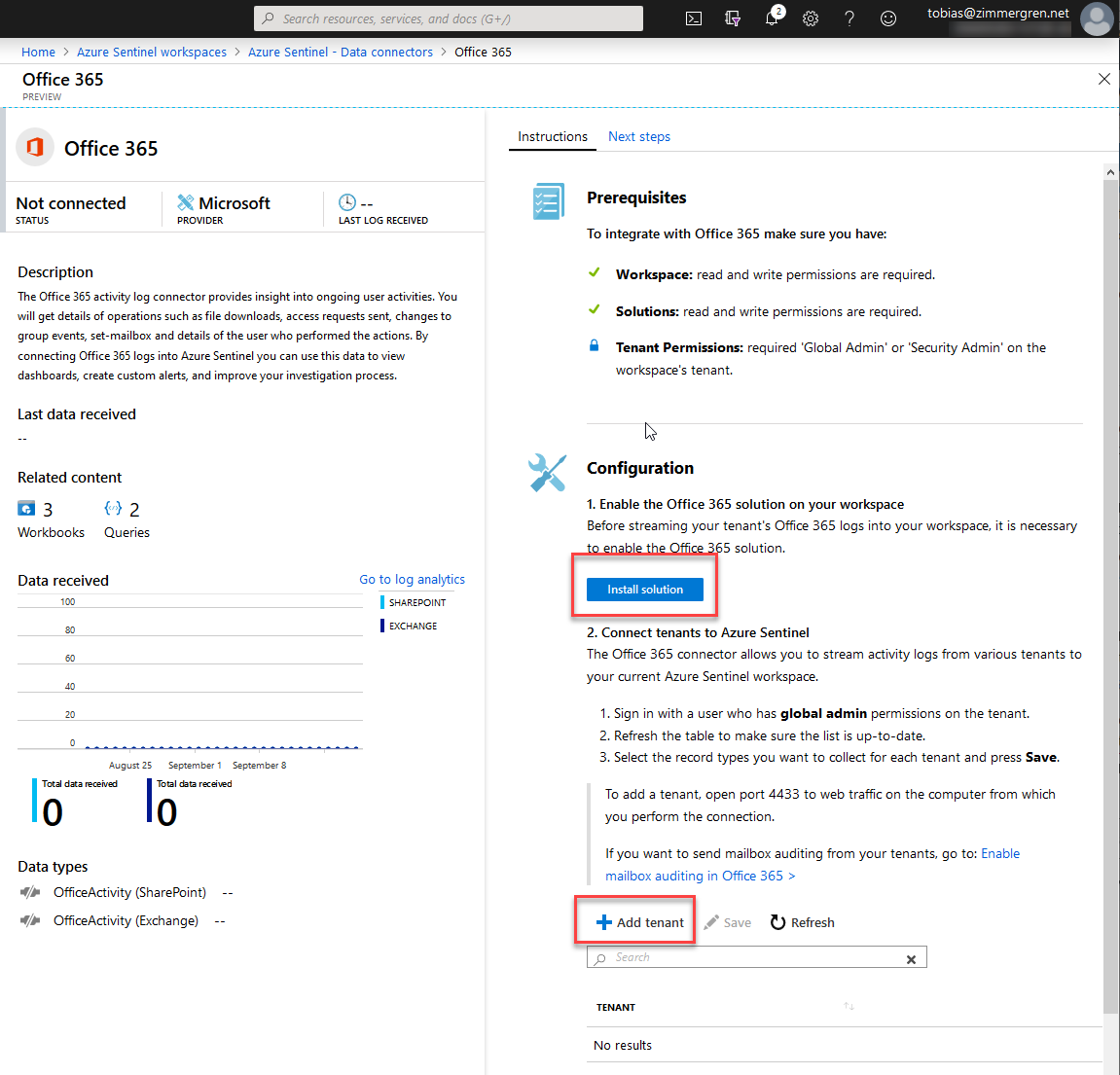
Clicking "Install solution" is super quick and gives you a notification saying everything is fine and dandy:
Add Tenant
Now that the Azure Sentinel workspace is prepped, and the data connector for Office 365 is installed and enabled, we can add our tenant(s).
Click "Add tenant" and sign in with the account you'd like to authenticate with, to any given tenant you'd like to add. It will bring up a consent dialog to accept the permissions from the Sentinel conector:
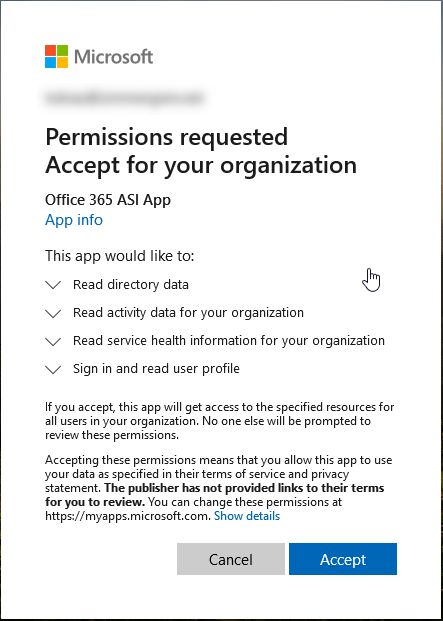
Once you've consented, you'll be presented with this very pretty (not) dialog. I'm sure this will improve soon:
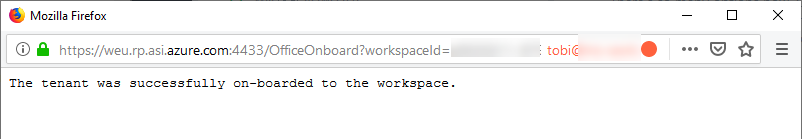
You'll see it when you hit the Refresh button, and it'll allow you to select which types of logs you'd like to ingest:
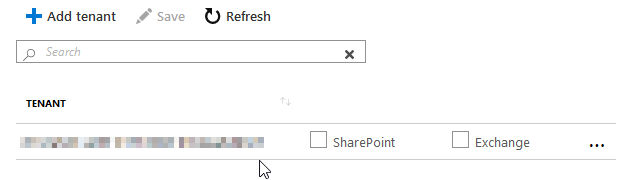
Tick the Exchange and SharePoint boxes, as per your requirements, and then click "Save".
At this point, we've connected the tenant - now we can go and digest the data in log analytics with the link in the connector:
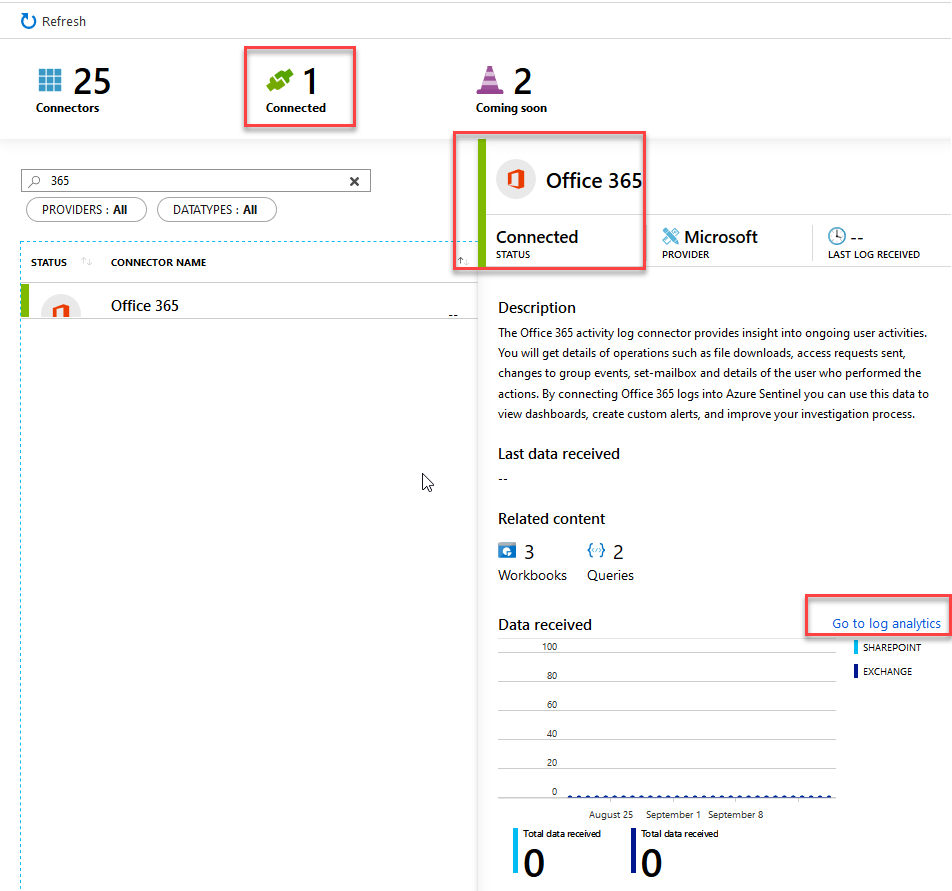
Review the dashboard and overview
Going back to my Azure Sentinel dashboard, I can see an overview of what's been happening. Since I just connected and nothing has happened yet, it's fairly empty. The more data sources you connect and want to ingest here, the more clever insights you'll benefit from.
Installing the Office 365 Dashboard in Azure Sentinel
With pre-defined Dashboards you can easily get started with seeing the most important data to your organization. You can easily customize what's appearing in the dashboards, but it's nice to get a running start.
Go to "Dashboards" and find "Office 365", then click "Install":
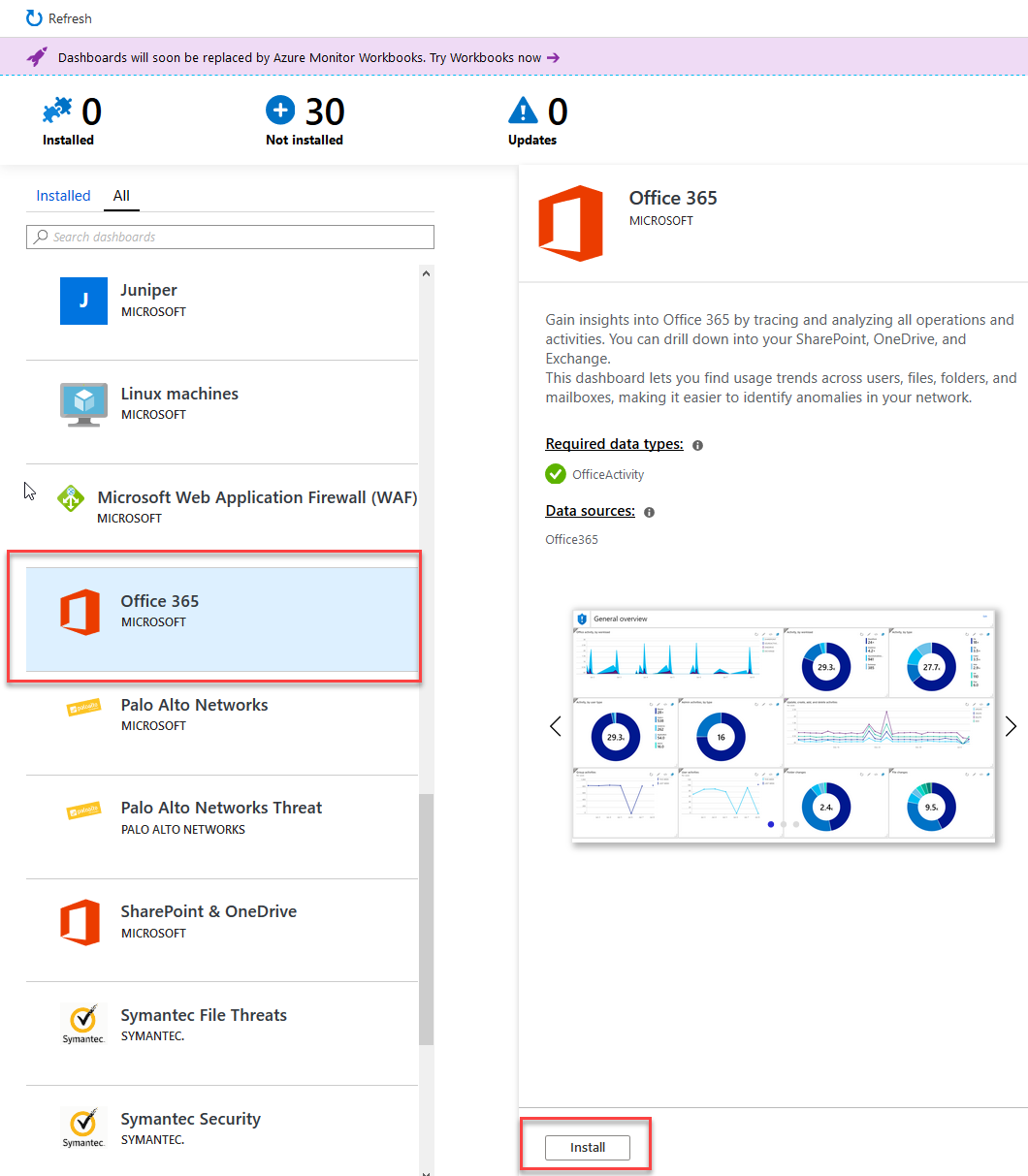
This built-in template for the Office 365 Dashboard contains vies for:
- Office activity by Workload
- Activities, grouped in various ways for easy digestion
- Group activities
- User activities
- Admin activities
- Create/Read/Update/Delete (CRUD) activities
- Folder changes
- File changes
- Top 10 activities for SharePoint & OneDrive
- Files downloaded (by extension)
- Files uploaded (by extension)
- Top 10 sites in SharePoint
- Mailbox logins
- External access activities
- Mailbox activities by user type
- And much more.
That's just a small portion of what's available right out of the box with the Azure Sentinel and Office 365 data connector integrations. This is some extremely beneficial data and insights for anyone responsible for technical operations and cloud governance, including handling your overall security posture.
Analytics - Rules and Rule Templates
Under the "Analytics" section, you can configure new Rule Templates to match criterias that are important for your organization, as well as use existing rules and activate them across your data.
I'll leave it to your to determine what rules you can and should implement for your organization, but it's a good thing to know about this feature.
Azure Sentinel Pricing
The pricing details of Azure Sentinel was made available with the launch of General Availability (GA), on September 24th 2019.
There's two available models:
- Capacity Reservation - Fixed fee and predictable cost.
- Pay-as-you-Go - Pay for the data ingested and data retention, which is based on Azure Log Analytics.
See the links below for additional insights into the costs.
Summary & Links
That's all there's to it. Now you can configure more data sources, check out the playbooks, analytics, and browse through logs and a lot more.
Sentinel will hep you increase your general Security Posture in your Azure services, and any services you connect through the data sources. Having this single place of security-related data ingestion is amazingly helpful.
Here's some good related reading from Microsoft:
- Azure Sentinel Overview (Microsoft Azure)
- Azure Sentinel Pricing (Microsoft Azure)
- Office 365 Data Connector for Azure Sentinel (Microsoft Docs)
From the Microsoft Tech Community:
- Azure Sentinel Agent: Collecting telemetry from on-prem and IaaS server
- Collecting Azure PaaS services logs in Azure Sentinel
From other parts of the community:
Thanks for reading, I hope you've enjoyed this piece! Please leave a comment.






Recent comments