Discover sensitive Key Vault operations with Microsoft Sentinel
Microsoft's Azure Key Vault Security workbook helps you structure the explorations of sensitive operations in your Azure Key Vaults. Using this workbook, we can cut the diagnostic and troubleshooting time down by a lot.
Microsoft's Azure Key Vault Security workbook helps you structure the explorations of sensitive operations in your Azure Key Vaults. Using this workbook, we can cut the diagnostic and troubleshooting time down by a lot.
This short post aims to showcase how we can learn more about our Azure Key Vault Security operations by automatically ingesting data into Microsoft Sentinel and then reviewing the ready-made workbook (template) from Microsoft.
Microsoft Sentinel holds many capabilities and empowers us to do more with less effort - this is one step in that direction.
Requirements
- Data source connectors: Azure Security Center, Azure Key Vault
- Data types: SecurityAlert, AzureDiagnostics
Exploring the Azure Key Vault Security workbook
When launching Microsoft Sentinel and navigating to Workbooks, we can search for templates that are ready-made for us to consume and modify according to our needs.
Search for "vault", and find the "Azure Key Vault Security" workbook by Microsoft.
Select "View template" to browse the data.
We'll see three main tabs:
- Azure Defender for Key Vault alerts.
- Analytics over Key Vault events.
- Key Vault monitoring.
From here, you can select the scope and time range, and then drill down into the area you're interested in.
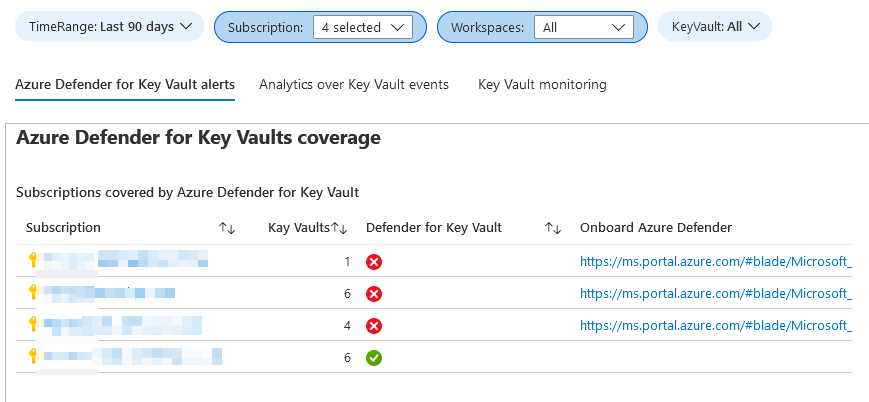
Azure Defender for Key Vault alerts
In the first tab, we see the subscriptions we have, how many vaults per subscription we have, and any warnings from Defender in these Key Vaults.
Scrolling down and selecting a subscription and vault, we can see any alerts on a timeline.
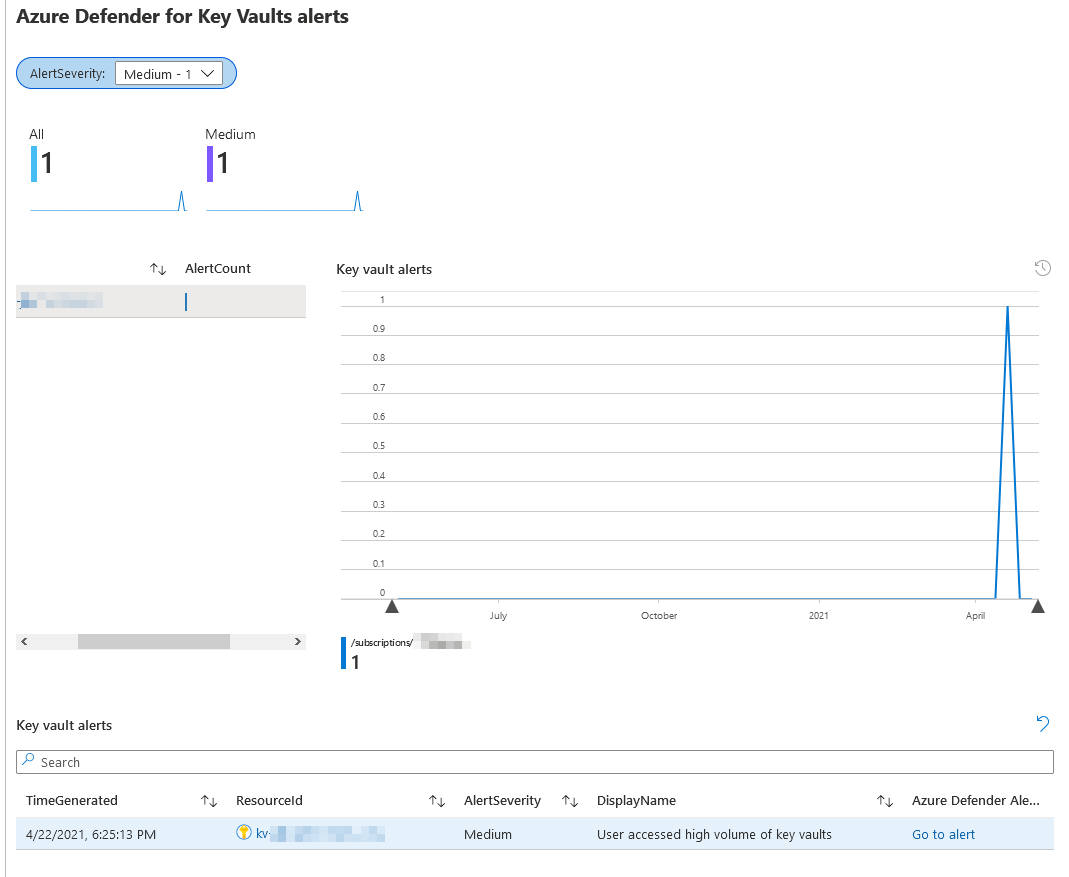
Selecting the specific alert, we can see related data to the entity, and resources involved.
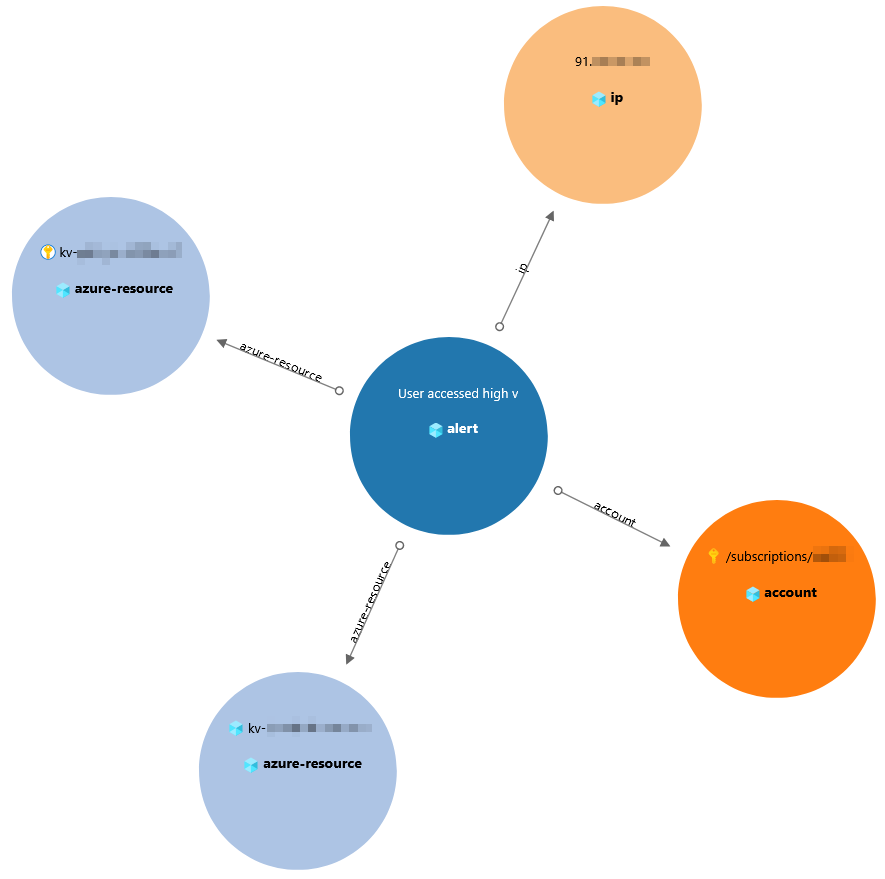
Analytics over Key Vault events
The second tab helps us get an overview of these things:
- Diagnostics settings.
- Anomalies (baseline and deviations).
- Event analysis.
- Mass Secret Retrieval.
- Operation Analysis.
Let's explore what these sections offer.
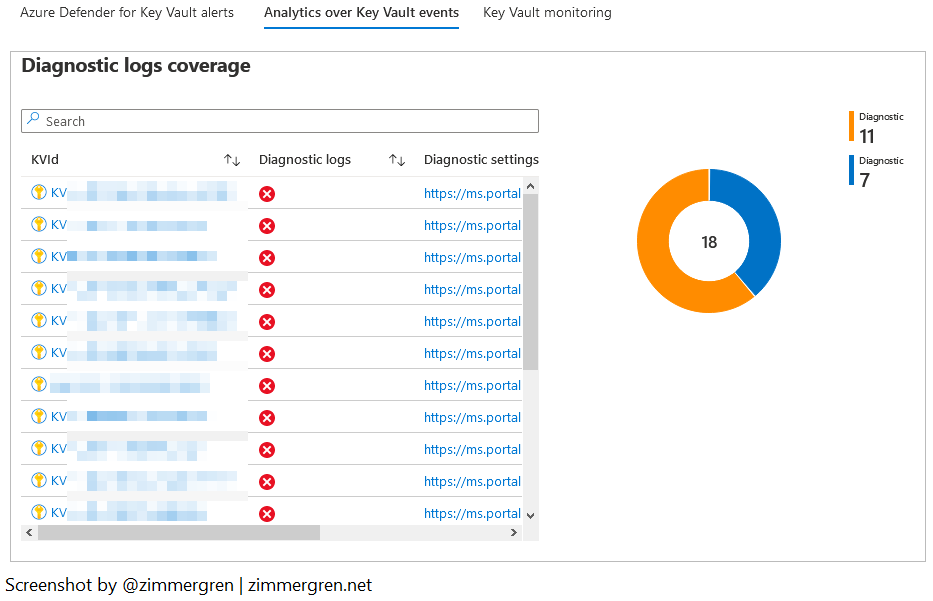
The diagnostic logs coverage is a way to visualize where we may need to strengthen our diagnostic logs. E.g., where it's not enabled for some reason. In the example subscriptions here, I have it enabled in some areas, and disabled in others, and we see the portion of vaults without coverage (11).
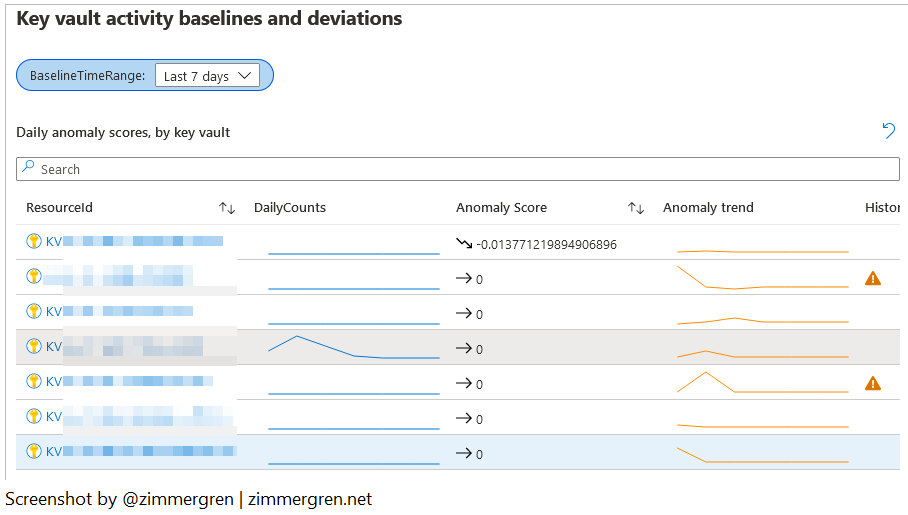
Next, we can see the anomalies, if any. These are events that are unusual or that have caused a flag to be raised. We can see the trend lines for the anomaly, and the daily counts. These can be helpful for identifying patterns of when anomalies happen.
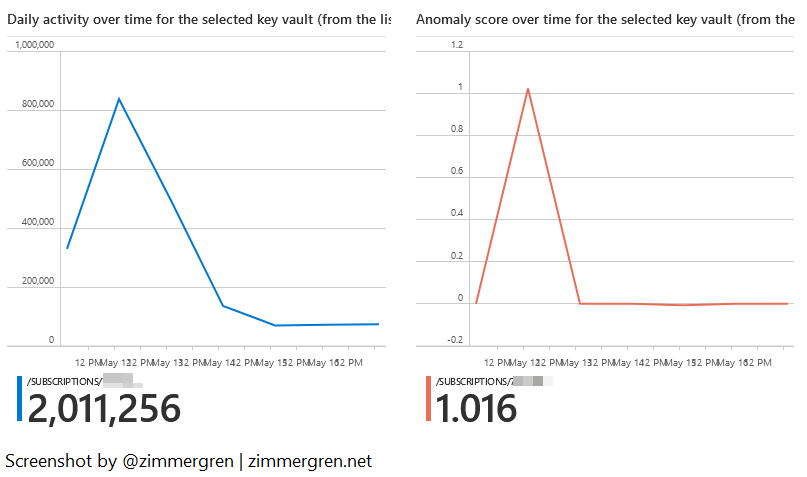
We can compare the daily activities over time with the anomalies. From the rendering here, I can correlate that anomalies happen more when there's more activity in the vault.
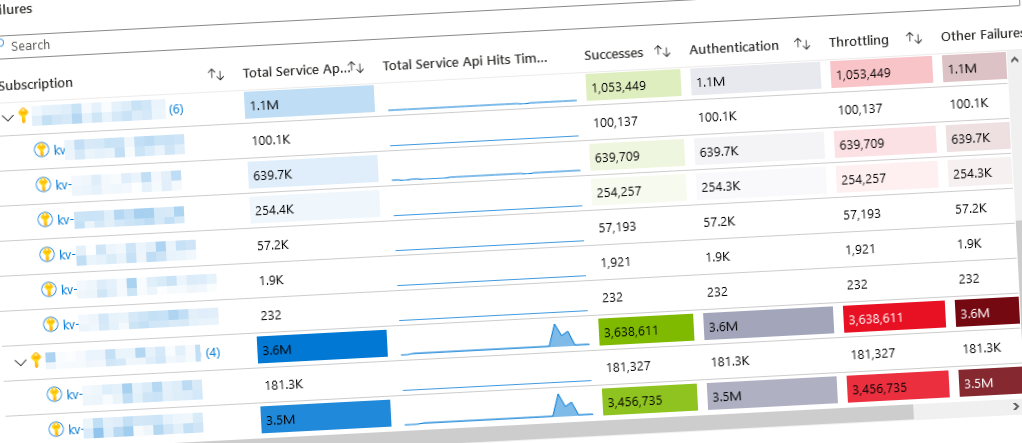
Further reviewing the data in the next section, we can get to some interesting graphs and numbers. This section holds the Event analysis and can be filtered by All events, or Failed events, and then grouped by vault name, IP, identity, or operation.
I use this view to understand how my different vaults are being impacted when we have load spikes. Not all vaults are serving the same traffic. Hence the information and analysis will vary a lot depending on the vaults here; However, you could easily compare the specific vaults you want by modifying the filter of what workspaces to collect information from and pick specific vaults for the data only.
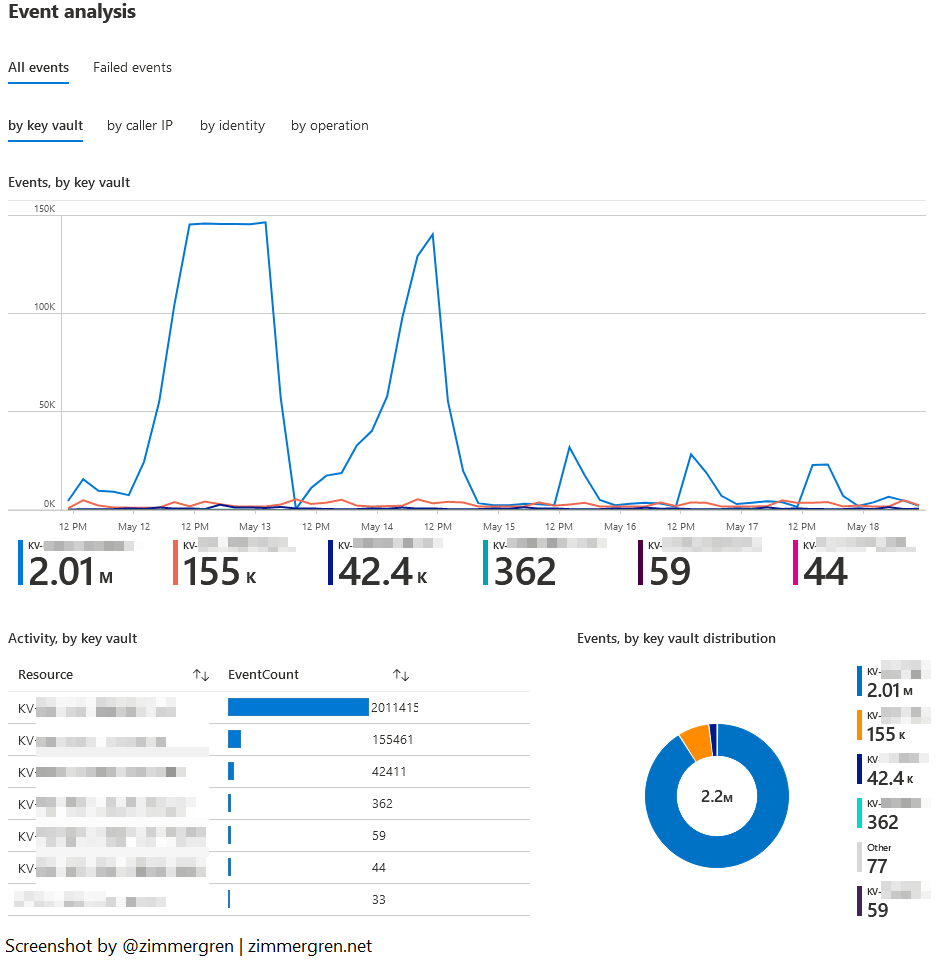
Moving further down this workbook, we find another interesting aspect: Mass Secret Retrieval.
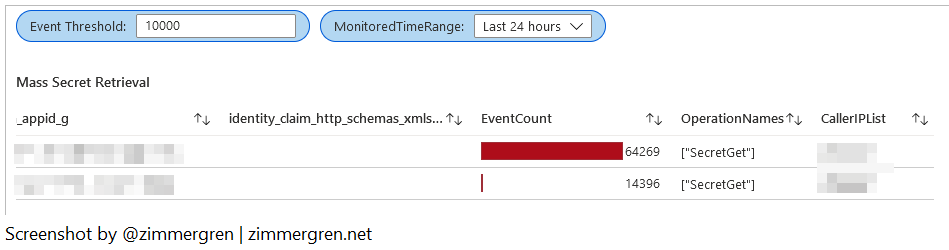
While some apps are designed for regular secret retrieval, some vaults may be designed to hold more long-term and less read-intensive information like backup encryption keys. When looking into the Mass Secret retrieval, we can determine whether we notice something out of the ordinary.
In my situation, I filtered on the vaults where more than 10,000 secrets have been retrieved in the last 24 hours. The application design allows for intense secret retrieval based on the distributed cloud workloads I use, so there is nothing out of the ordinary for the results I see in this particular case.
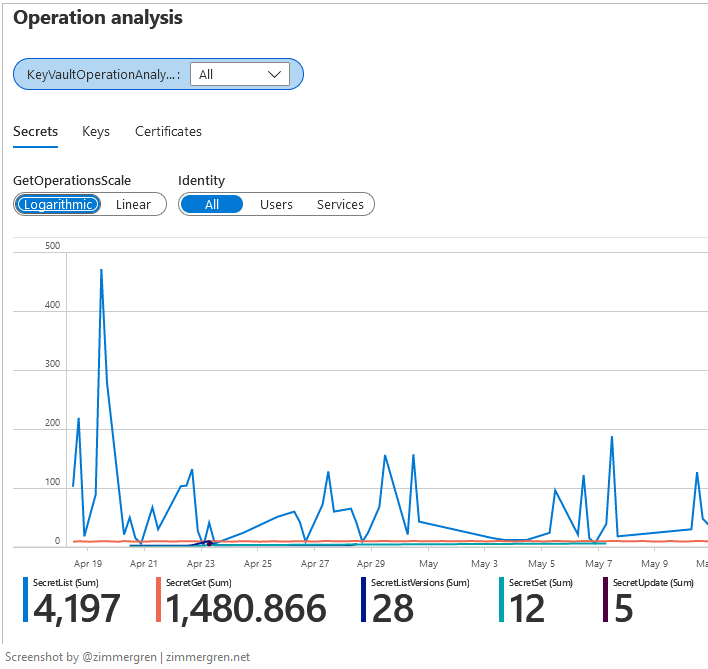
Finally, the Operation analysis section helps us understand what operations have been executed - not just that secrets have been retrieved, or a key vault has been throttled; We also get to see the distribution of the operations and how the compare.
It's important to understand that you can switch between Logaritmic and Linear scale in the graph. This will give you completely different visuals, and one or the other might make more sense in your scenarios when you need to find patterns and understand usage.
Here's the Logarithmic scale:
Compare the same data, but in the Linear graph. For me, the linear graph made it possible to understand how the patterns of secret retrieval happens, and I can gain more insights into my operations quickly this way.
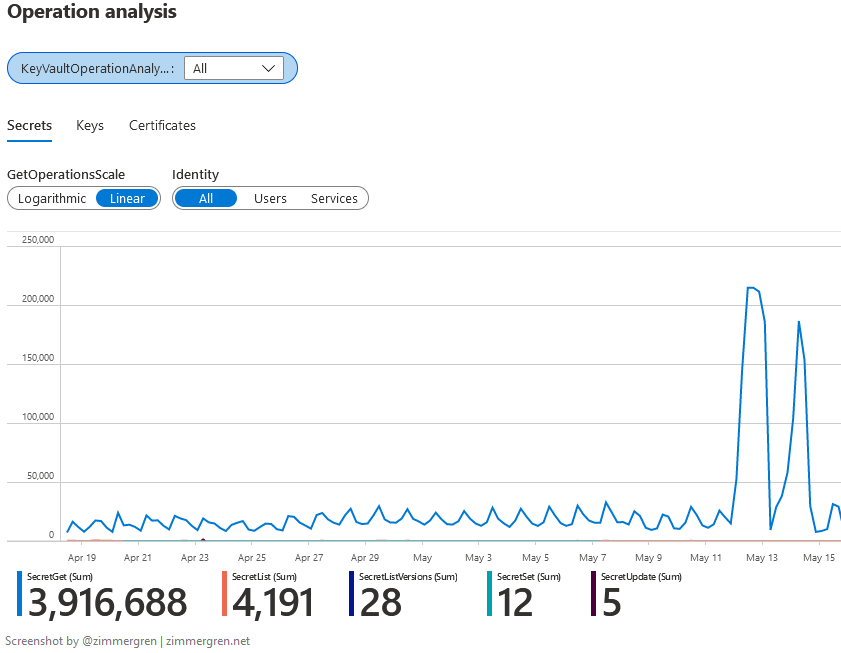
With the linear graph, I can see that the main pattern of retrieval. This correlates with how my distributed global applications work. However, we can also identify that there was a spike recently, and now we know where to start looking for more details around that.
In my particular case, the spike is caused by known factors to us, and are expected. But I still wanted to showcase these capabilities from the Microsoft Sentinel workbook by Microsoft for Key Vault security.
Key Vault Monitoring
The third and final tab of this workbook contains Key Vault monitoring insights. These insights are useful when you want to understand the health across all your vaults in all your subscriptions, for example.
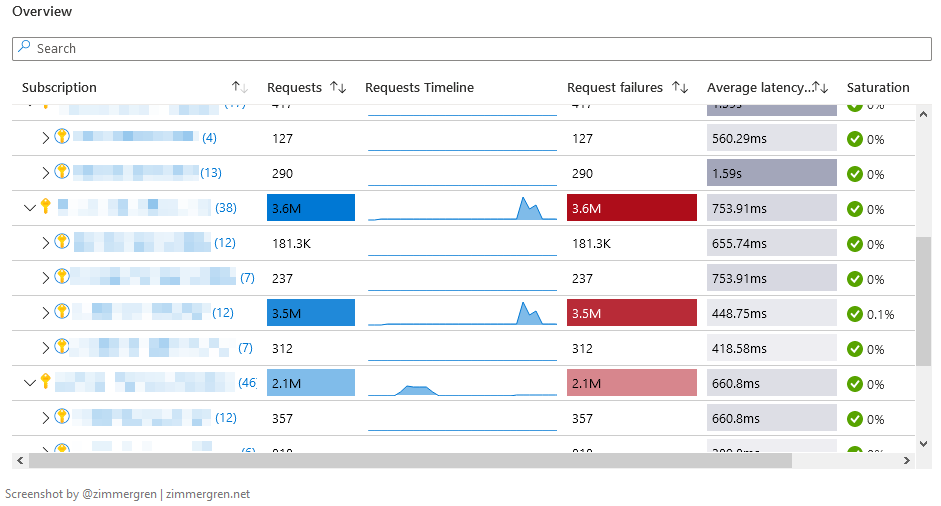
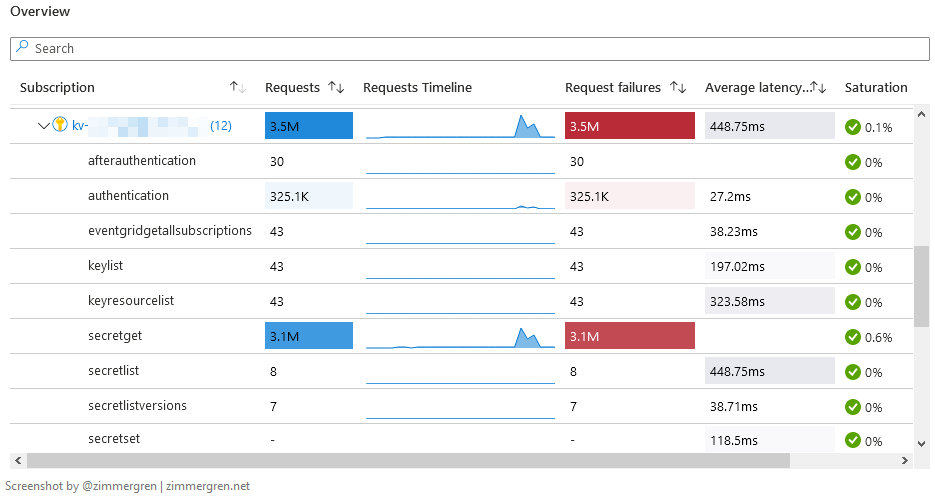
We can expand each Key Vault in the tree-view and see more insights for the operations that were performed in the given time frame.
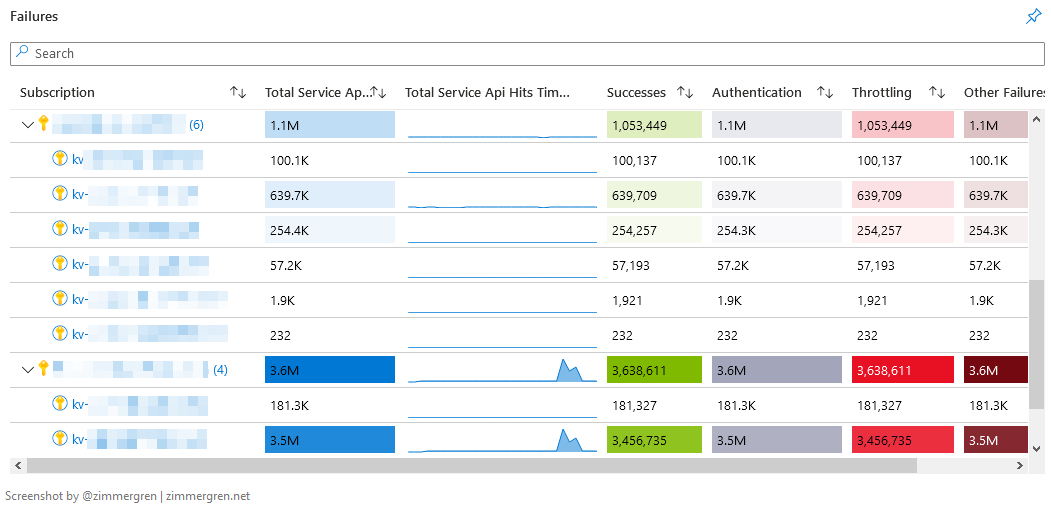
Finally, the workbook provides some insights into successes versus failures.
Summary
Thank you for reading all the way until the end. I hope this sheds some light on the capabilities of Microsoft Sentinel and the built-in workbooks that are offered by Microsoft.
I have discussed related topics at great lengths with customers, people in the community, and business peers. I hope you can benefit from this post in some way and can start exploring your Key Vault data using Microsoft Sentinel!






Recent comments