
Establish your organizational compliance readiness
Table of Contents
Wading through organizational change can be a challenge. Critical aspects of some of the challenges I've faced lately are security and compliance, and how to stay on top of sensible practices that can be applied across your organization.
While there are great built-in capabilities and tools provided by Microsoft - especially for the technical side - there are usually requirements from customers to not only prove your technical security posture, but also your organizational regulatory compliance.
In this post, I talk about some aspects of compliance and security for organizations, from a non-technical angle. Instead of the tools, we'll look at the frameworks and processes that can help us get started and establish how ready we are for cloud compliance. I will list some of the resources that's been a great help on our organizational compliance journey.
Before diving into for example a specific certification like the SOC2 or ISO27001 , it can make sense to see how your organization measure up across multiple compliance standards. It should also enable you to more easily understand what work is involved to achieve one or the other standard. This is why I want to share details about these helpful tools and framework, as opposed to how to achieve one specific compliance standard only.
Use security and compliance frameworks.
Whether you're going to the cloud, or you're already there and are looking to increase the readiness of your security processes, the following section can prove useful.
We'll take a look at:
- Cloud Security Alliance (CSA)
- Cloud Controls Matrix (CCM).
- Consensus Assessment Initiative Questionnaire (CAIQ).
- Security, Trust, Assurance and Risk (STAR).
- National Institute of Standards and Technology - Risk Management Framework (NIST RMF).
- Cloud Adoption Frameworks
Cloud Security Alliance
The CSA, or Cloud Security Alliance, is an organization that helps raise the awareness of best practices for cloud computing. When operating solutions in the cloud, particularly SaaS offerings, I get many requests from customers about filling out forms about data security, information security, and how and why someone would trust how we handle their data.
The CSA offers tools and resources when you're looking to prepare your organization, assess your cloud readiness, and validate your security posture.
I'm highlighting some of the crucial tools and resources from CSA that are valuable for your overall organizational security and compliance.
Cloud Controls Matrix - CCM
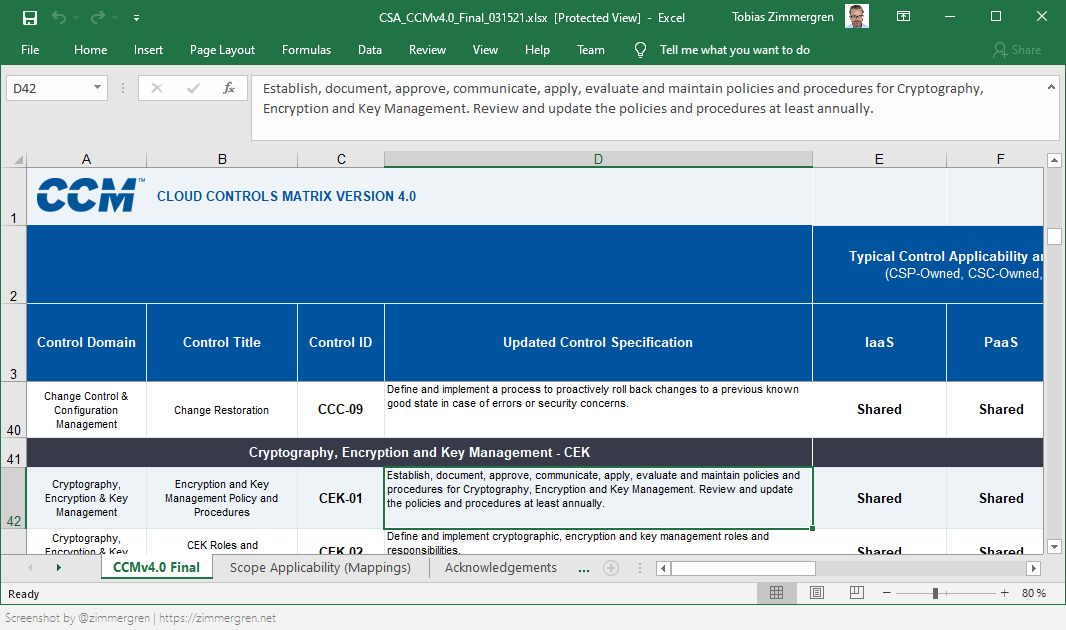
The Cloud Controls Matrix is a cybersecurity control framework for your cloud workloads. If you are operating cloud environments and have a say in security, I would recommend you familiarize yourself with the CCM.
Why would you spend time learning about the CSA?
- Suppose you access customer systems and data in any way. You will sooner or later be requested to show evidence of information security standards compliance or fill in questionnaires to answer specific questions about your company, the internal processes, and how you secure data and infrastructure in your cloud solutions.
- The CCM maps to many industry standards and regulatory control frameworks. Understanding how your organization measures up on these 197 controls will help you make decisions for the security practices in your organization.
Read more:
- Cloud Controls Matrix v4 - by Cloud Security Alliance
Consensus Assessment Initiative Questionnaire (CAIQ)
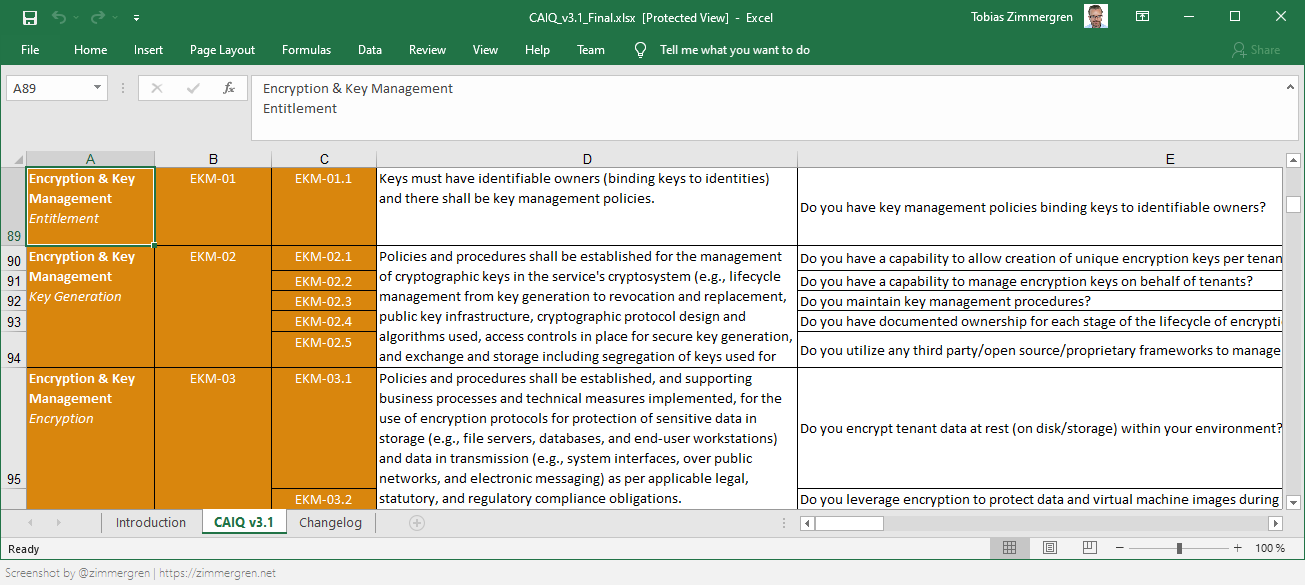
The CAIQ, or Consensus Assessment Initiative Questionnaire, is something I have received countless times from customers.
Usually, one receives this questionnaire so customers can assess the organization's capability to handle information security across not only the tech stack but your processes, too.
Read more:
- Consensus Assessment Initiative Questionnaire (CAIQ) (Cloud Security Alliance)
Security, Trust, Assurance and Risk (STAR)
The STAR registry is a public registry that documents the security and privacy controls provided by some of the popular cloud computing offerings.
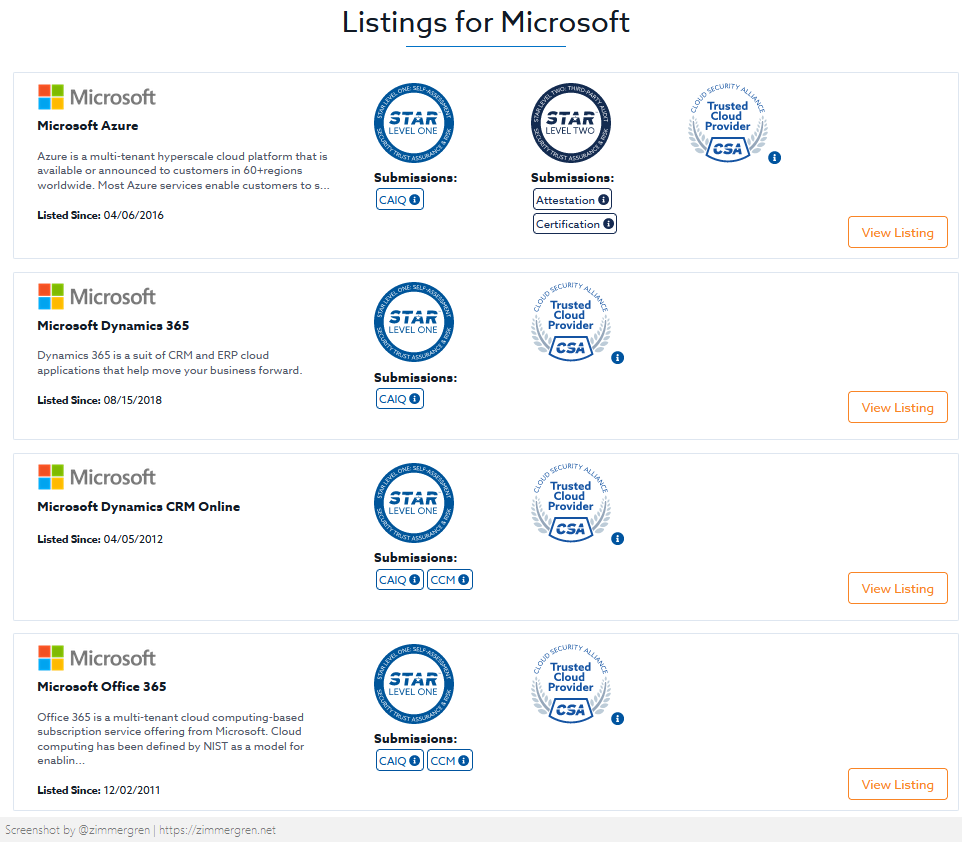
With STAR, you can increase the transparancy around your security controls that you have in place for your solutions and organization. Using the CCM and CAIQ as a baseline, you can pursue a STAR Level 1 and strengthen the security posture, improve your trust and increase transparency.
STAR Level 1: Self-assessment.

A Level 1 self-assessment isn't audited by any third-party, it is a great step in the right direction for establishing trust and transparency. Providing your customers with answers to the questions in the CAIQ can help you a long way, even if they are not audited by an accredited third-party auditor.
There are two types of self-assessments we can do with STAR.
- Security Self-Assessment
- GDPR Self-Assessment
Read more:
STAR Level 2: Third-Party Audit

While the Level 1 self-assessment isn't controlled by any third party, the Level 2 requires third-party audits.
Read more:
- Security, Trust, Assurance and Risk (STAR) (Cloud Security Alliance)
- STAR Submission Guide Level 1 (Cloud Security Alliance)
National Institute of Standards and Technology - Risk Management Framework (NIST RMF)
You may already be familiar with NIST. However, I want to highlight the NIST RMF - the Risk Management Framework.

As quoted from their website:
The Risk Management Framework provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. The risk-based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. Managing organizational risk is paramount to effective information security and privacy programs; the RMF approach can be applied to new and legacy systems, any type of system or technology (e.g., IoT, control systems), and within any type of organization regardless of size or sector.
- https://csrc.nist.gov/projects/risk-management/about-rmf
You can use the RMF to help with risk assessments internally. A good first step can be to review applicable controls: https://csrc.nist.gov/Projects/risk-management/sp800-53-controls/release-search#!/controls?version=5.1
Read more:
Additional related NIST resources:
CAF - Cloud Adoption Frameworks
Many cloud vendors provide excellent documentation and content around how to get your organization ready for the cloud. If you are already in the cloud, many resources have a different focus.
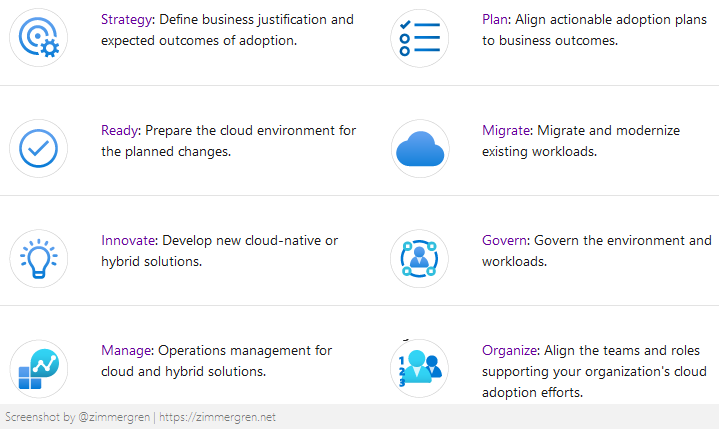
Using the Cloud Adoption Framework is great to build and implement necessary business and technology strategies and understanding best practices.
Since we are talking about security and compliance specifically, the portion of the CAF that mentions security is the most exciting aspect today.
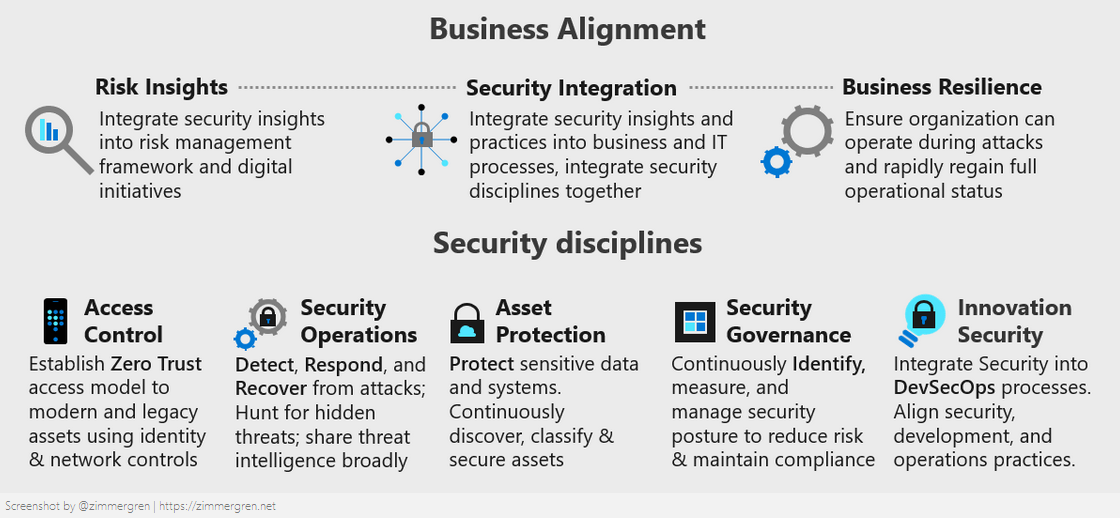
Cloud security is a continuous effort cross-team in your organization. With the Cloud Adoption Framework, you get a framework to lean on when tackling this journey's practical aspects: planning and implementation.
While defining the security and compliance strategy is one thing, it has to be executed by someone in the organization. Cloud architects are usually a good candidate for tackling the challenge of taking these designs into tangible solutions in practice.
Read more about Microsoft related CAF resources:
- Microsoft Cloud Adoption Framework for Azure (Microsoft Docs)
- Security in the Microsoft Cloud Adoption Framework for Azure (Microsoft Docs)
Read more about other cloud vendors' CAF resources:
- AWS Cloud Adoption Framework (Amazon.com)
- Google Cloud Adoption Framework (Google.com)
Summary
This was a brief scratch on the surface to get introduced to some of the more well-known frameworks and tools we can use to work with compliance in the cloud.
Depending on the size of an organization, the journey can be span anywhere from a few weeks to several years - but know that you are never really finished. Where ever you are in your organizational compliance journey, it can always be a benefit to measure the current state with the CAIQ and CCM, which helps us better understand where we are, and shows transparency and insights to our customers.
Working into the future, I am utilizing specific tools and processes to target specific compliance frameworks; with this focus, its also easier to distinguish the bigger areas of work from the low hanging fruits. In the end, we want to ensure an ongoing security, privacy, and compliance commitment cross-team in our organizations.
Enjoy your journey, and don't forget to involve all stakeholders early.








Recent comments