Containers
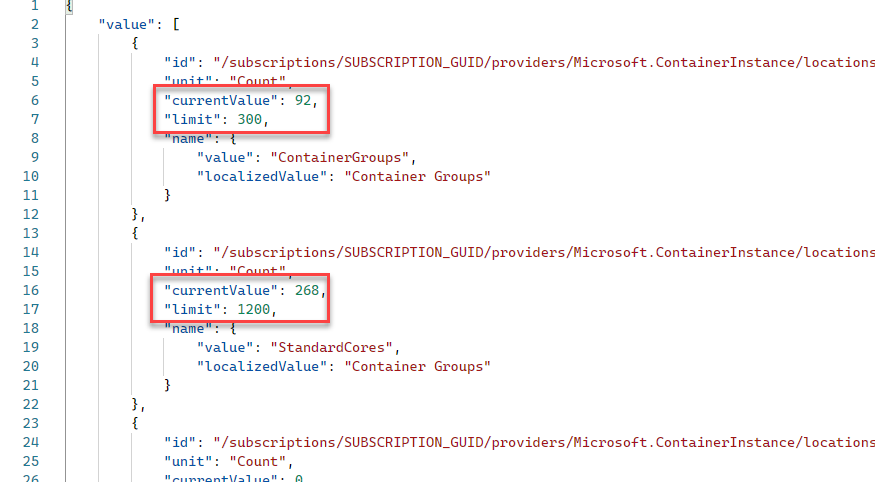
Get the Container Instances usage in an Azure subscription Paid Members Public
Using the Azure management APIs to list Azure Container Instance usage helps us understand how close to the limits we are!
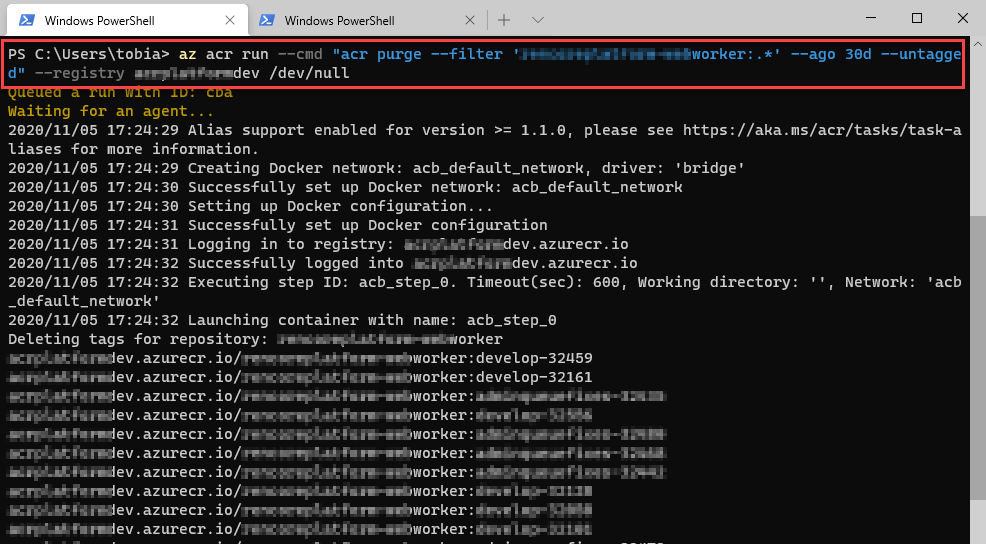
Purging container images from Azure Container Registry Paid Members Public
Keeping container registries clean and neat is not always an easy task. We have fairly agile release processes, and sometimes we release many images, several times per day across dev- and production environments. Microsoft recently introduced a neat way to automatically purge images based on filters, directly from the Azure
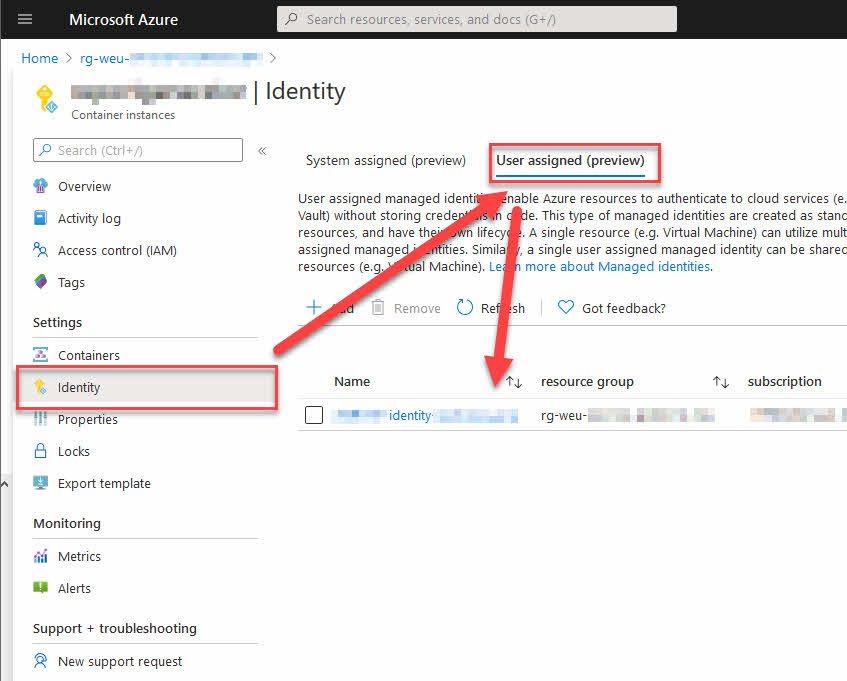
Programmatically create Azure Container Instances and connect a Managed Identity Paid Members Public
> "This feature is currently in preview. Previews are made available to you on the condition that you agree to the supplemental terms of use [https://azure.microsoft.com/support/legal/preview-supplemental-terms/]. Some aspects of this feature may change prior to general availability (GA). Currently, managed identities on Azure
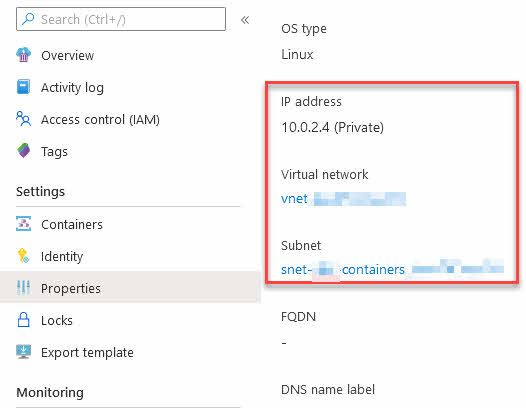
Programmatically create Azure Container Instances in an existing Virtual Network Paid Members Public
In recent years I've worked extensively with various approaches to create ACI's, also known as Azure Container Instances. I have these standard approaches for various scenarios: * Define a YAML file, and create ACI from the command line. * Define an ARM template and create ACI using a

Thoughts on Bring Your Own Key, or BYOK, to Azure Container Registry Paid Members Public
In this article, I am exploring the capabilities of Bring Your Own Key with the Azure Container Registry. A way for you to get better control of the full Key Lifecycle Management process, should you need to. I am detailing a few of my thoughts that come up around different

How Tokens and Scope Maps for Azure Container Registry introduces great repository-level access restrictions Paid Members Public
I have previously written about various Container-topics [https://zimmergren.net/tag/containers/] on this site. Recently, I also published a post about "Best Practices for security in Azure Container Registry [https://zimmergren.net/top-10-best-practices-for-security-in-acr-azure-container-registry/] ." In this post, I want to bring awareness to how we can make use
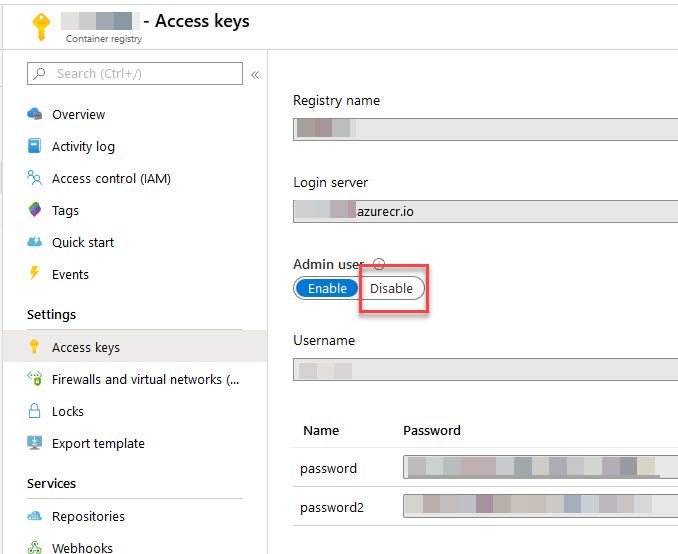
Best Practices for security in Azure Container Registry Paid Members Public
Best Practices for security in Azure Container Registries is a list of real-world experiences in strengthening your security posture.
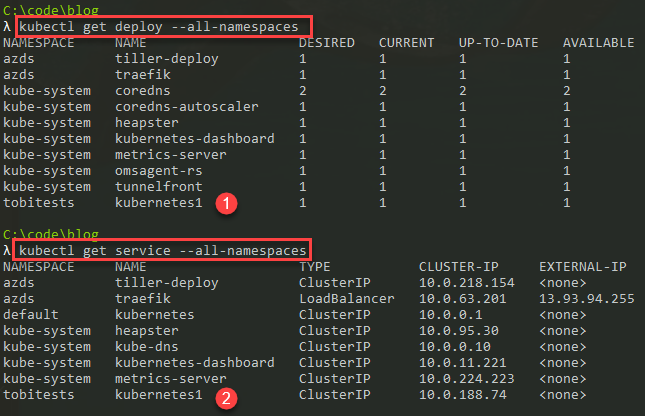
Developing using Azure Dev Spaces with Azure Kubernetes Services Paid Members Public
Explore Azure Dev Spaces for AKS, to easily do development work, and hit F5 to update in Kubernetes in your dev space. Quicker, easier and more reliable iterations will win the day.





Recent comments