Security
Posts touching on Security in various angles lives in this category.

Frameworks to strategically improve your cybersecurity Paid Members Public
Learn about popular cybersecurity frameworks like NIST Cybersecurity Framework (CSF), CISAs Cross-Sector Cybersecurity Performance Goals (CPG), MITRE ATT&CK and D3FEND, Microsoft Cloud Adoption Framework's Secure methodology, and Microsoft's CISO Workshop Training.

Learnings from the NSA and CISA top 10 cybersecurity misconfigurations Paid Members Public
Learn more about the joint advisory by the NSA and CISA, highlighting the top 10 cybersecurity misconfigurations commonly found in large organizations' networks.

What is the Cybercrime Atlas? Paid Members Public
The Cybercrime Atlas is an initiative launched by the World Economic Forum to better understand and combat cybercrime globally. By mapping the cybercriminal ecosystem, it aims to disrupt cyber-criminal networks.

Redacting sensitive information with Application Insights in C# Paid Members Public
This article teaches you how to redact sensitive information in Application Insights when you send traces from your .NET applications.
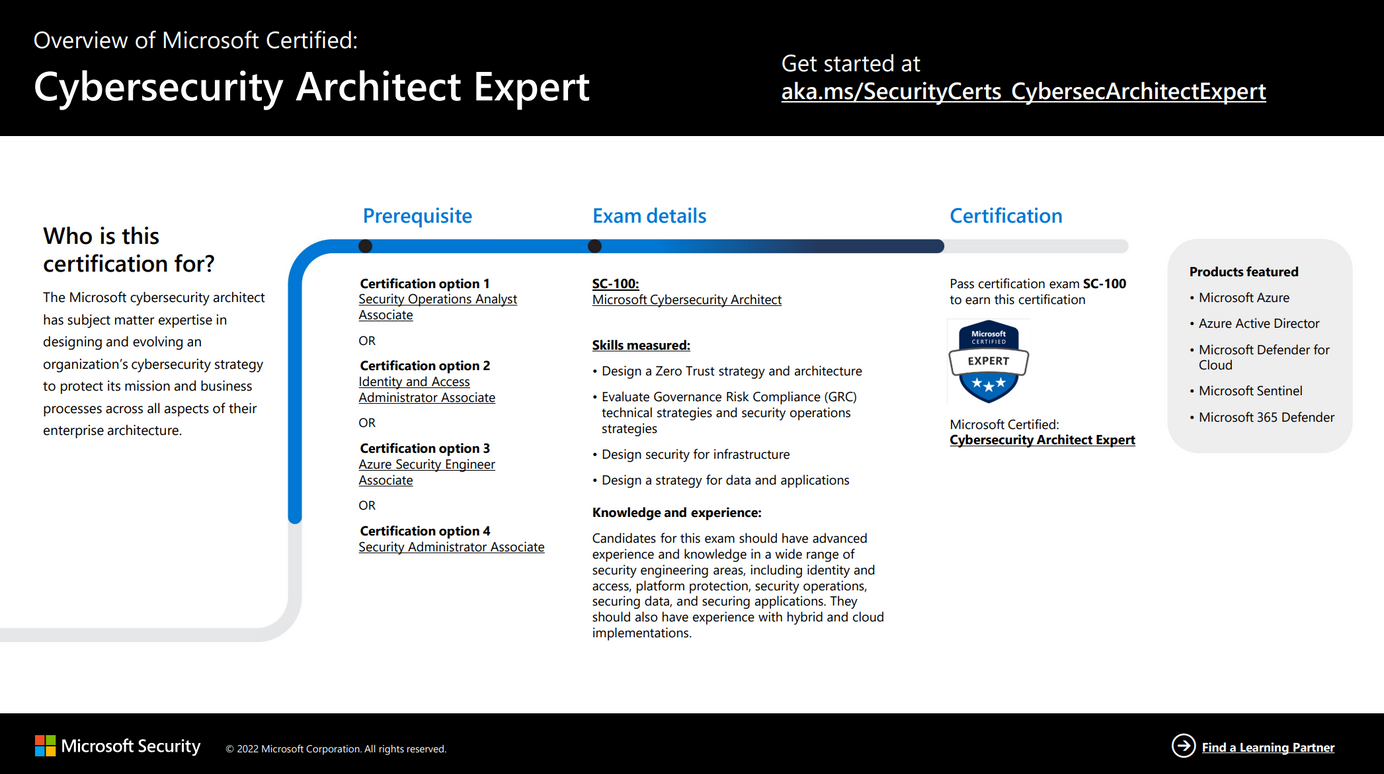
Exam Study Guide: SC-100 - Microsoft Cybersecurity Architect Expert Paid Members Public
I recently decided to sit the SC-100: Microsoft Cybersecurity Architect Expert exam which, if you pass, grants you the certification with the same title. I am happy to share that I passed the exam. In this post, I will share some details about the experience, and links and insights for

Recommended books about Azure security! Paid Members Public
Recently, I got the question to share a list of books I read on Azure security. While I find most of my material online, in Microsoft Docs, Microsoft Learn, and community blogs, there are some relevant books to look at if you're aiming to strengthen your security knowledge
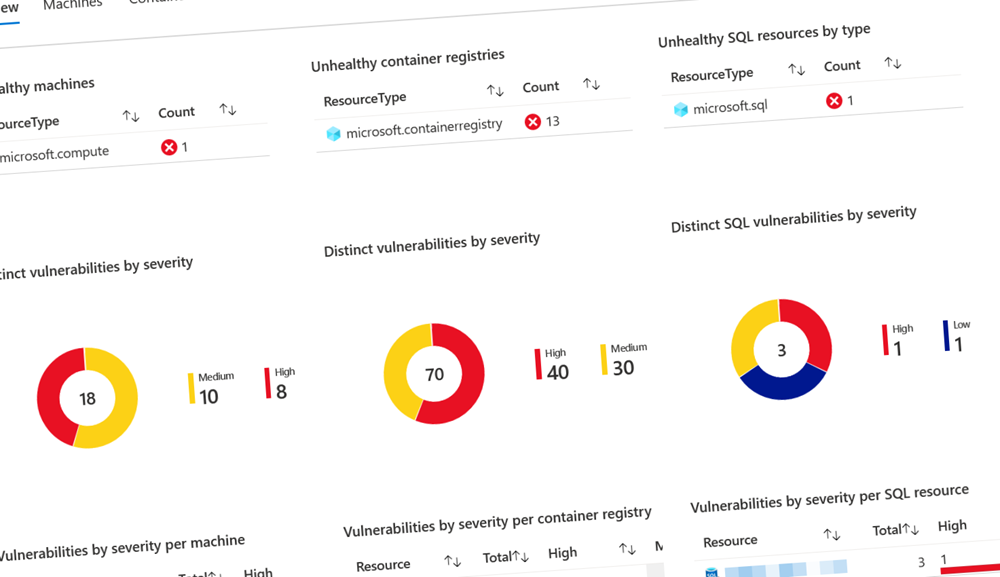
Top 3 favorite capabilities in Microsoft Defender for Cloud Paid Members Public
Working with Microsoft Defender for Cloud is amazing. We can get a lot of insights and guidance on our journey to improve our security and compliance posture.
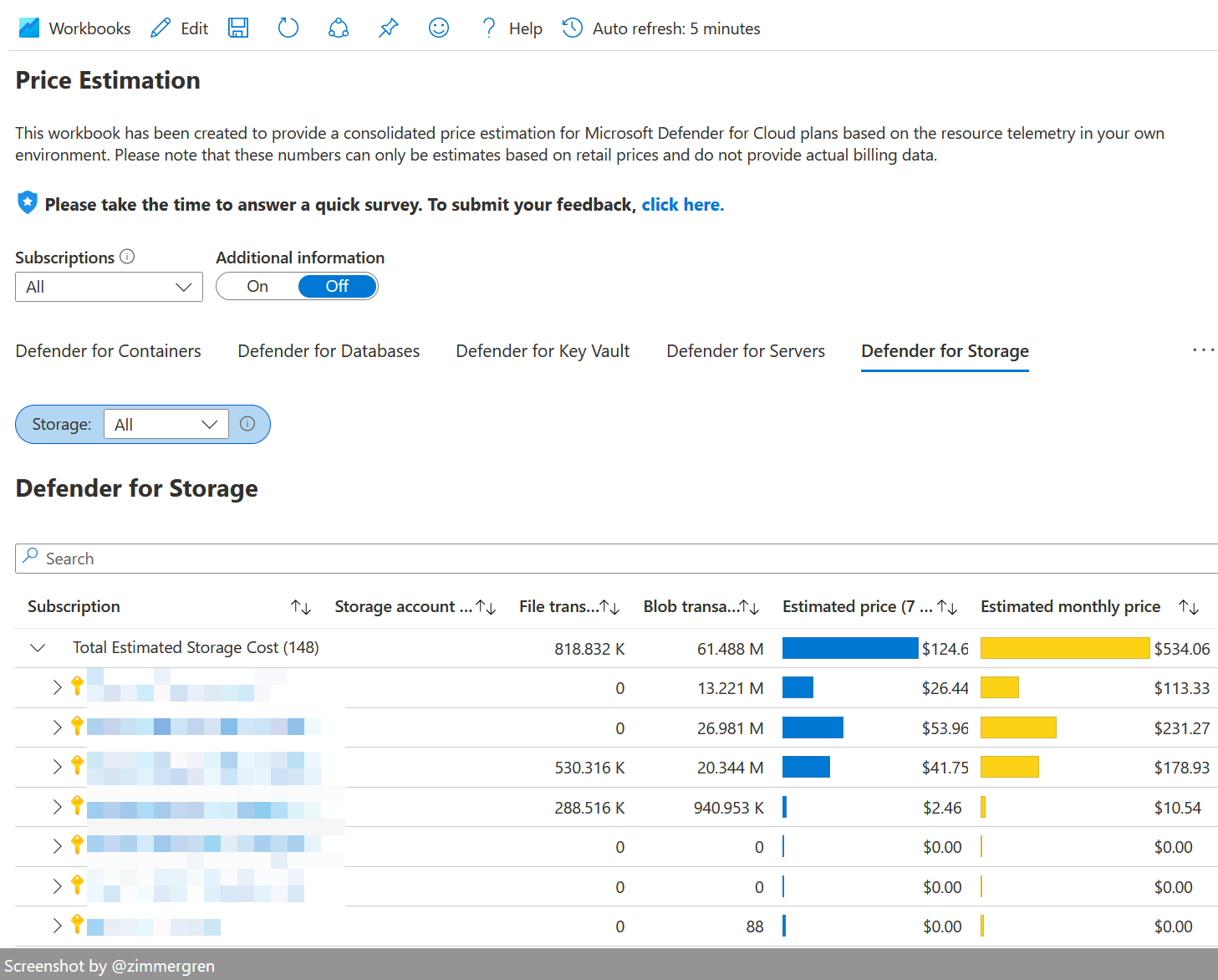
Estimating the real cost of Microsoft Defender for Cloud Paid Members Public
It can be tricky to understand the cost of Microsoft Defender for Cloud. Here's a way to simplify the process using the built-in workbooks. In this post, we'll dive into the challenge of understanding the true cost of Microsoft Defender for Cloud.





Recent comments