Top 3 favorite capabilities in Microsoft Defender for Cloud
Working with Microsoft Defender for Cloud is amazing. We can get a lot of insights and guidance on our journey to improve our security and compliance posture.
Table of Contents
Microsoft Defender for Cloud is a fantastic product.
We get comprehensive threat management, improved security posture of our infrastructure, and can harden the configuration of our resources. Additionally, we can measure how we compare to industry-standard benchmarks and regulatory compliance frameworks to ensure we're on the right track.
Recently, I was in a discussion where someone new to Azure asked why they would want to invest time in learning the Microsoft Defender for Cloud capabilities and where they should start.
With this short post, I want to bring some attention to some of my favorite capabilities of the Microsoft Defender for Cloud service that I regularly use.
This list is not extensive and there are many more capabilities under the covers of Defender for Cloud. But, here goes my tips from some of the key functionality I use on a daily basis, operating distributed cloud production workloads.
Number 1: Azure Security Benchmark
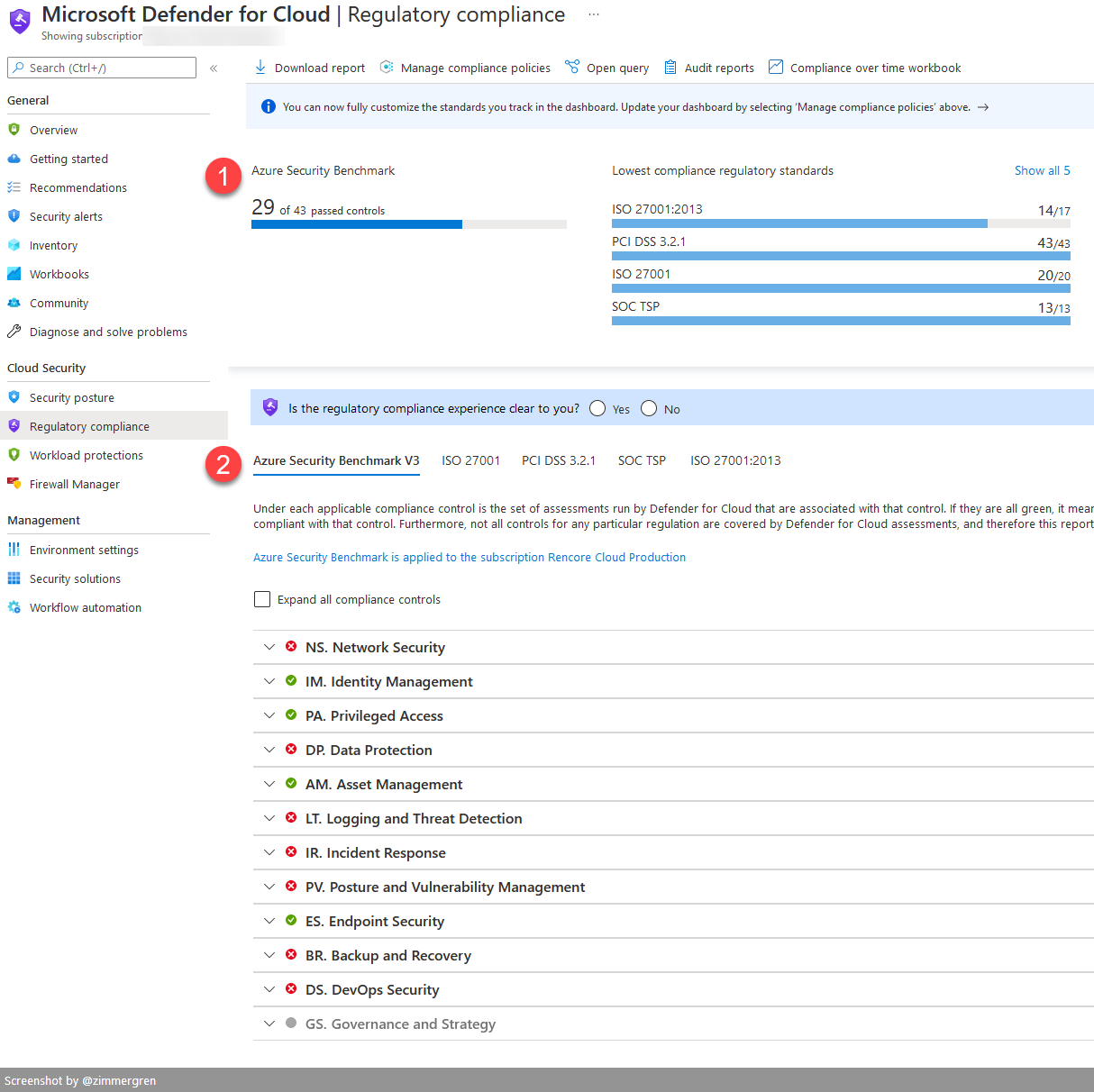
In Microsoft Defender for Cloud Regulatory Compliance Dashboard, you can monitor the Azure Security Benchmark v3. The benchmark is a set of best practices and security recommendations that span all services in Azure.
Using the Azure Security Benchmark is remarkably insightful and keeps us on our toes to help ensure we have a well-designed security posture. Analysis of our Azure real-estate happens automatically through Microsoft Defender for Cloud, and we can review the results and take action from the Regulatory Compliance dashboard.
See below:
- The number of passed controls across the available checks.
- Go to the Azure Security Benchmark tab to see what controls succeed and fail, and expand to take further action.
We can drill down into more granular controls and take action.
- A failing control.
- Sometimes we get the option for a Quick fix. When the solution is simple, for example, enabling Microsoft Defender for Storage for the subscription, the Quick Fix can be significant. But, beware of the costs!
- Next to every control, there is an indication that shows whose responsibility this is—MS for Microsoft, C for Customer.
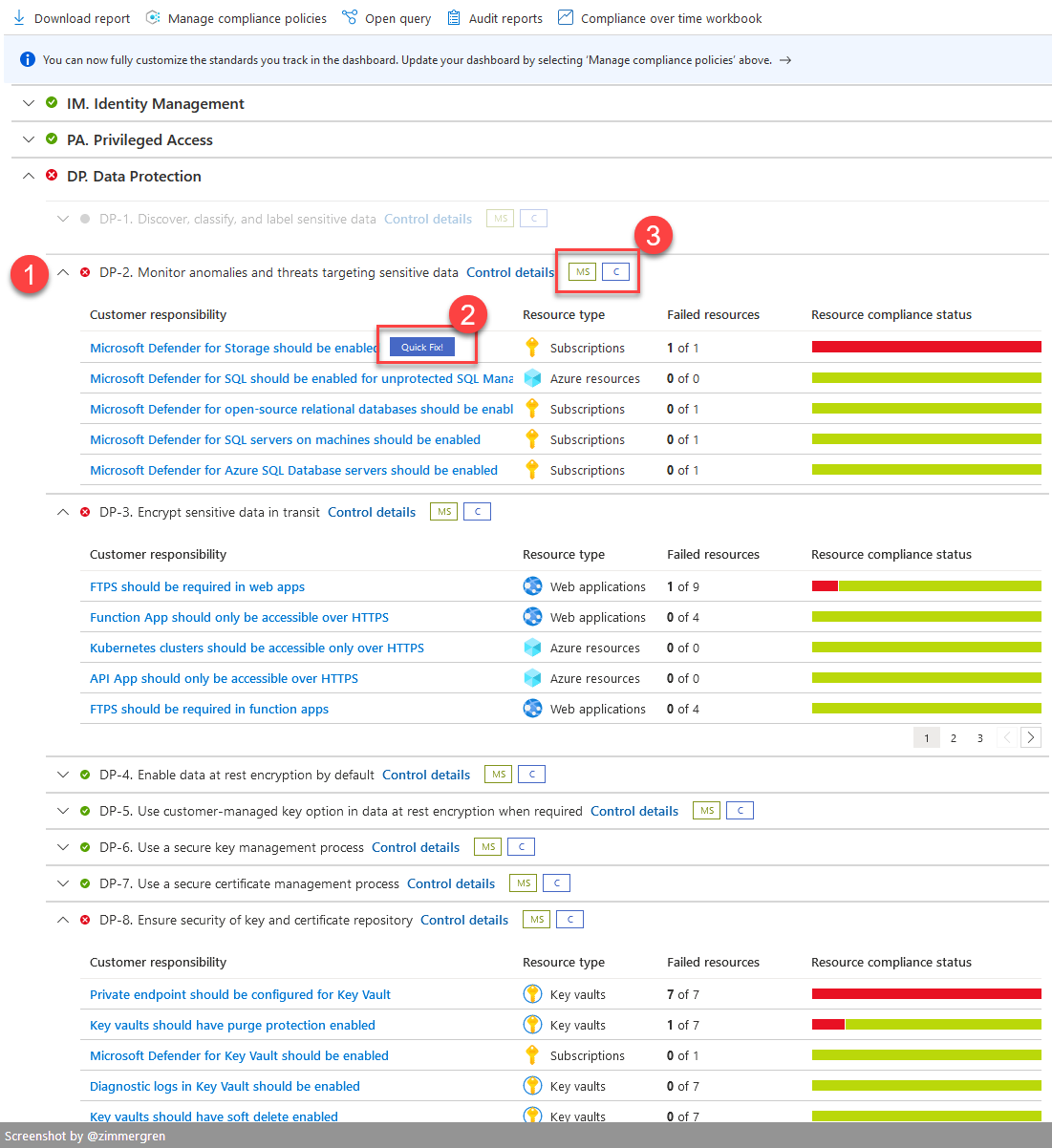
Working through these recommendations helps tremendously increase our security posture, and it also pushes our infrastructure toward compliance with several regulatory standards.
Additional security control frameworks
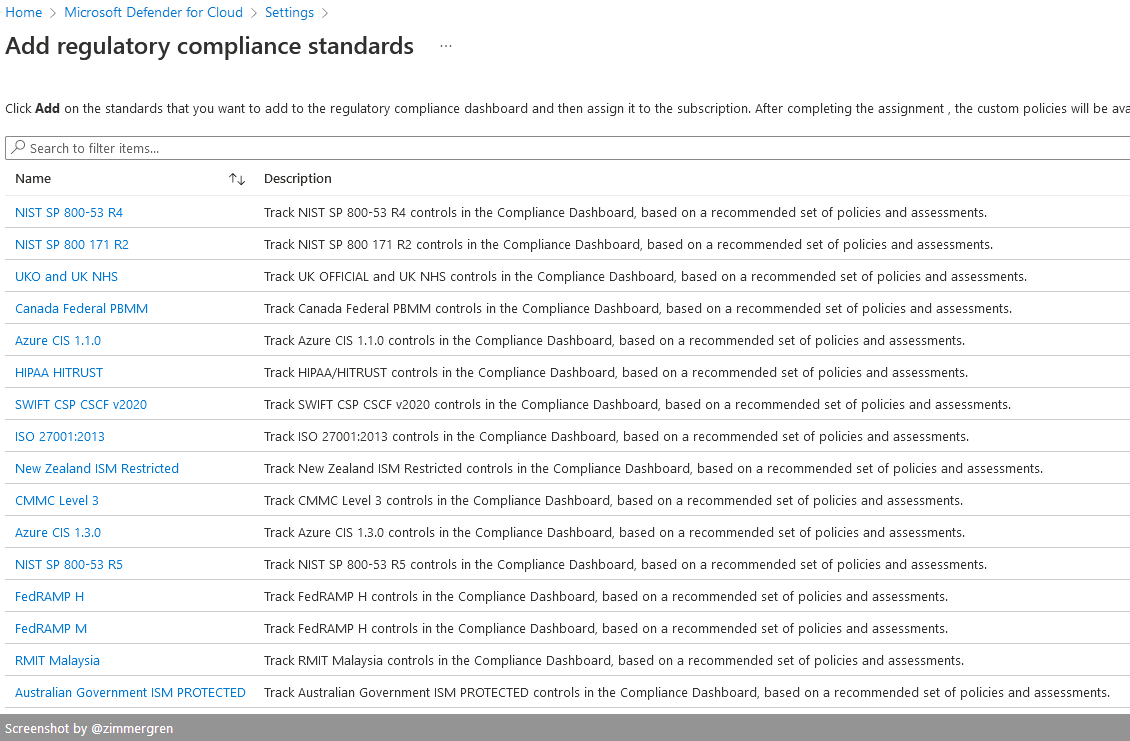
Similar to the Azure Security Benchmark, there are regulatory compliance controls for several other frameworks, including ISO 27001, PCI DSS 3.2.1, SOC TSP, NIST, HIPAA, FedRAMP, etc.
To find the list, and add them to your dashboard, navigate to:
- Microsoft Defender for Cloud - Environment Settings - Select a scope - Click "Add more standards"
I truly appreciate the insights and recommendations from Microsoft Defender for Cloud regarding my compliance and security status across my cloud estate.
The Azure Security Benchmark, and regulatory compliance in general, is one of my go-to areas for this product. Remember, security and compliance are continuous efforts, not one-off or point-in-time tasks.
Number 2: Workbooks
I have three angles for workbooks with Microsoft Defender for Cloud.
- Built-in Workbooks.
- Community Workbooks.
- Your custom Workbooks.
Generally, a workbook is something that provide us a way to bring in data from multiple data sources from across your Azure estate, and then combine this into a more interactive experience.
For more information and a great overview of workbooks, check out the information in the Azure Monitor docs; very applicable for when designing your interactive workbooks.
- Azure Monitor Workbook (Microsoft Docs)
Built-in Workbooks
Microsoft Defender for Cloud comes with a set of built-in workbooks. These are great for quickly getting insights and taking action on things in your cloud estate.
Don't forget that you can also modify any of these workbooks and save your own version. This is greatly beneficial if you want to tailor the system to your exact needs - something I definitely recommend.
Here's some of the built-in workbooks that I work with. They are fairly simple, but they give me the insights and data I need to continue our Compliance and Security journey.
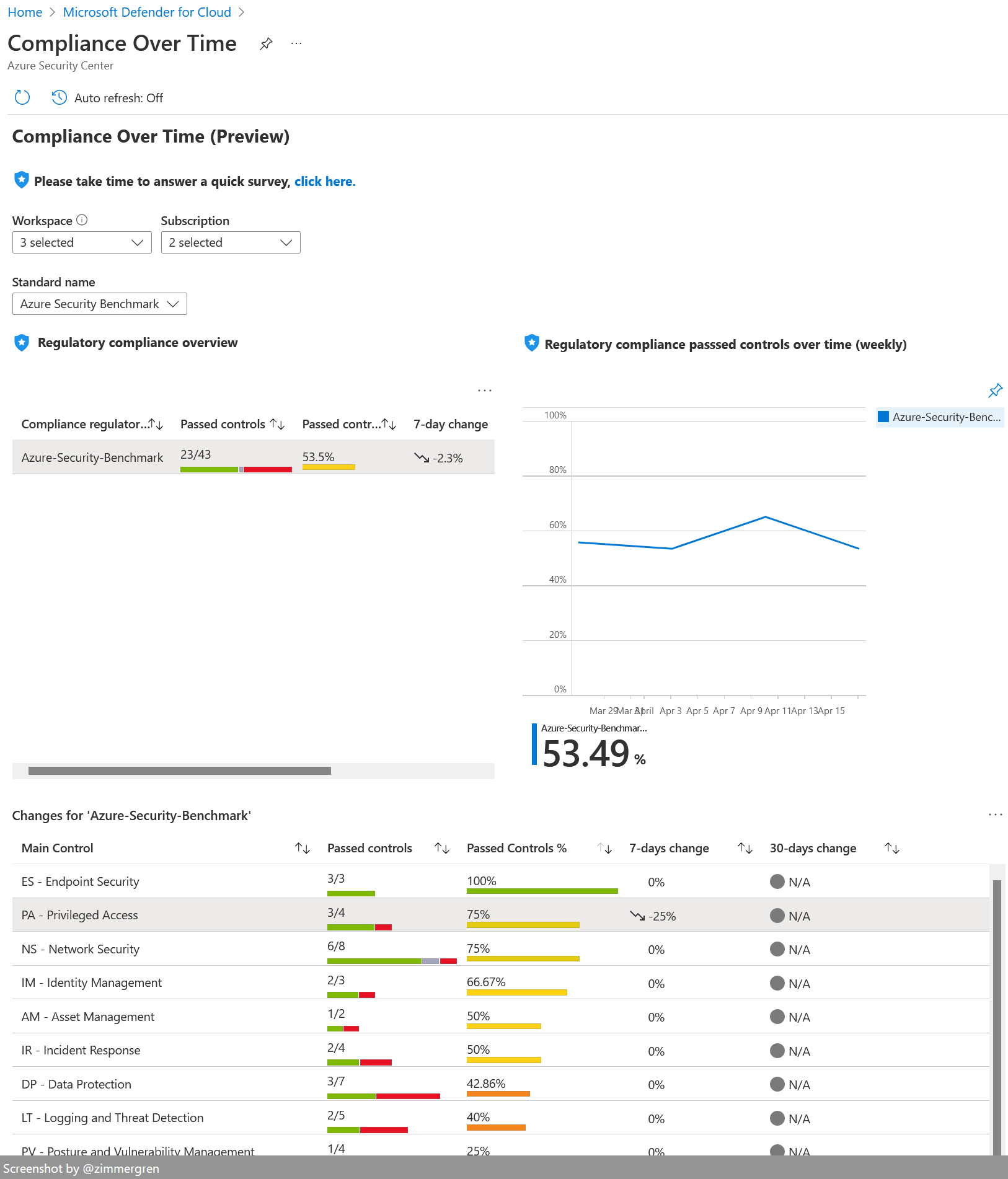
Workbook: Compliance Over Time
This is a great way to see how your compliance has changed over time. You can, of course, use it to see the most recent relevant information - but to me, the power here is to see whether you're improving your compliance posture or not.
In the example, I've selected a few subscriptions that have quite some room for improvement, to show what the workbook can look like.
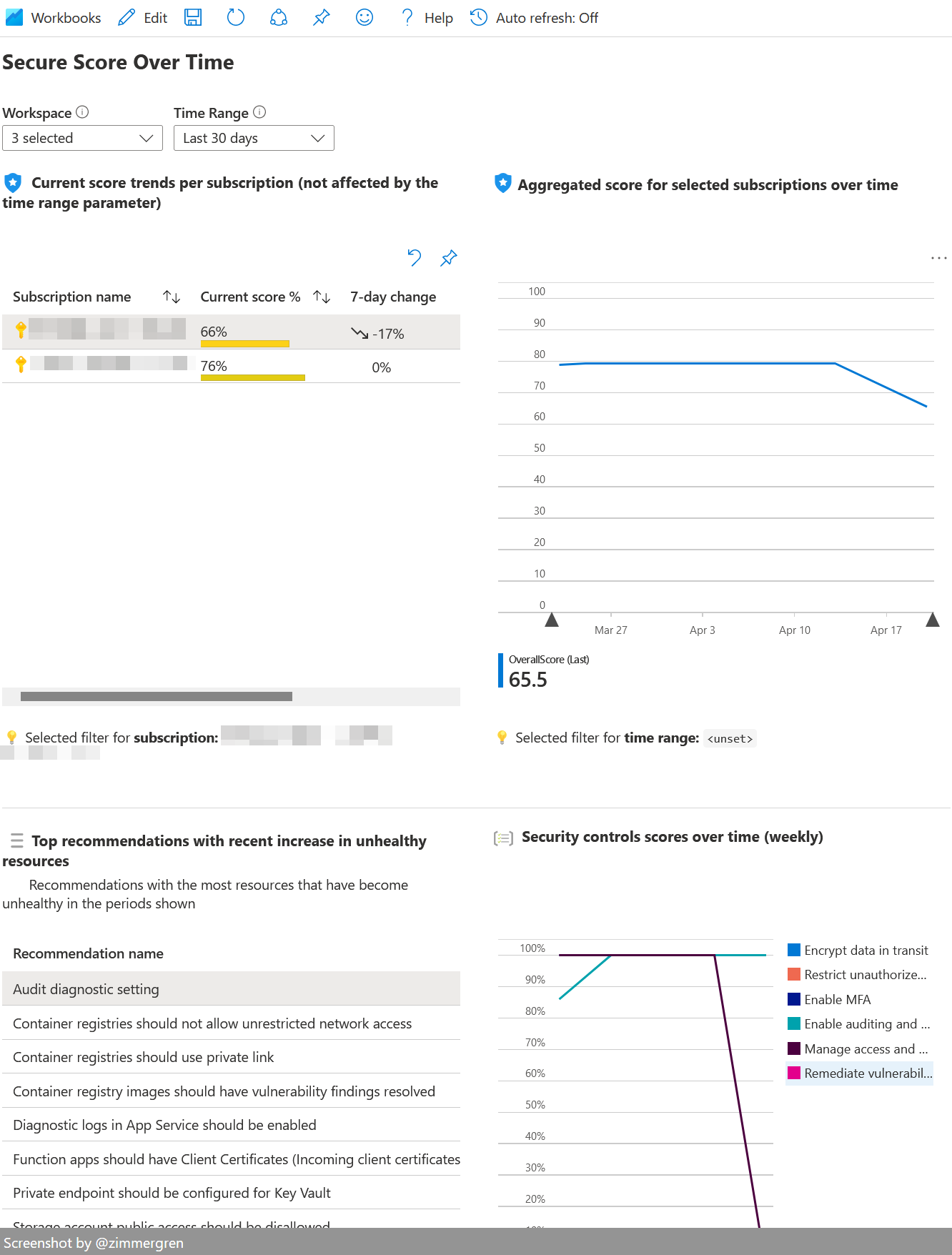
Workbook: Secure Score over time
This is another interesting workbook to track the change in our Secure score over time. I previously wrote about tracking your Secure Score over time in Azure.
Read my previous post on this topic:
- Track your Secure Score over time in Azure (Zimmergren.net)
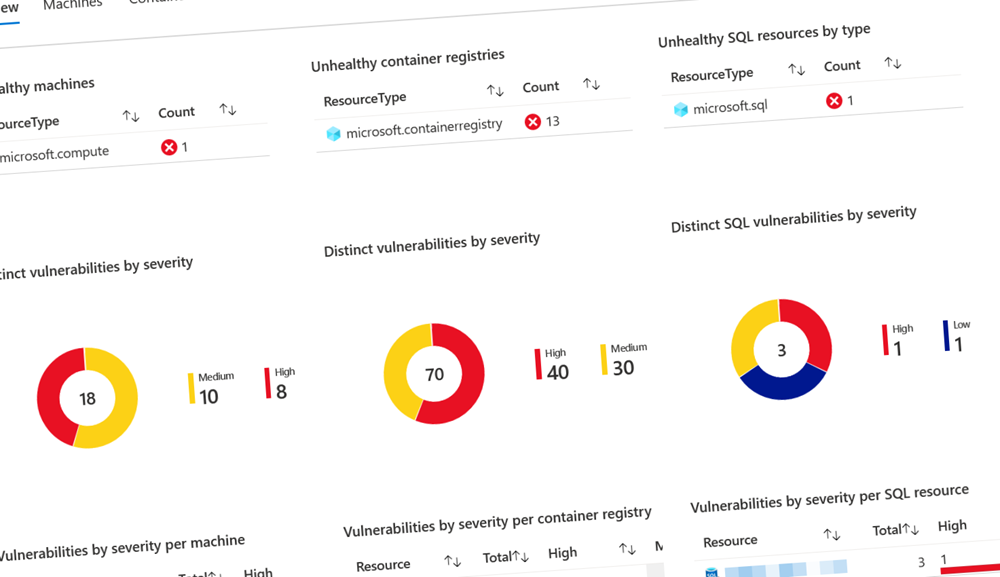
Workbook: Vulnerabilities
Reviewing active vulnerabilities from a single place can be insightful. With this workbook, while it's pretty simple in its nature, we can overview the existing vulnerabilities found across our cloud estate in our environments.
In my example, I've picked some of the less important subscriptions and demo environments to showcase what it can look like when you've got some work ahead.
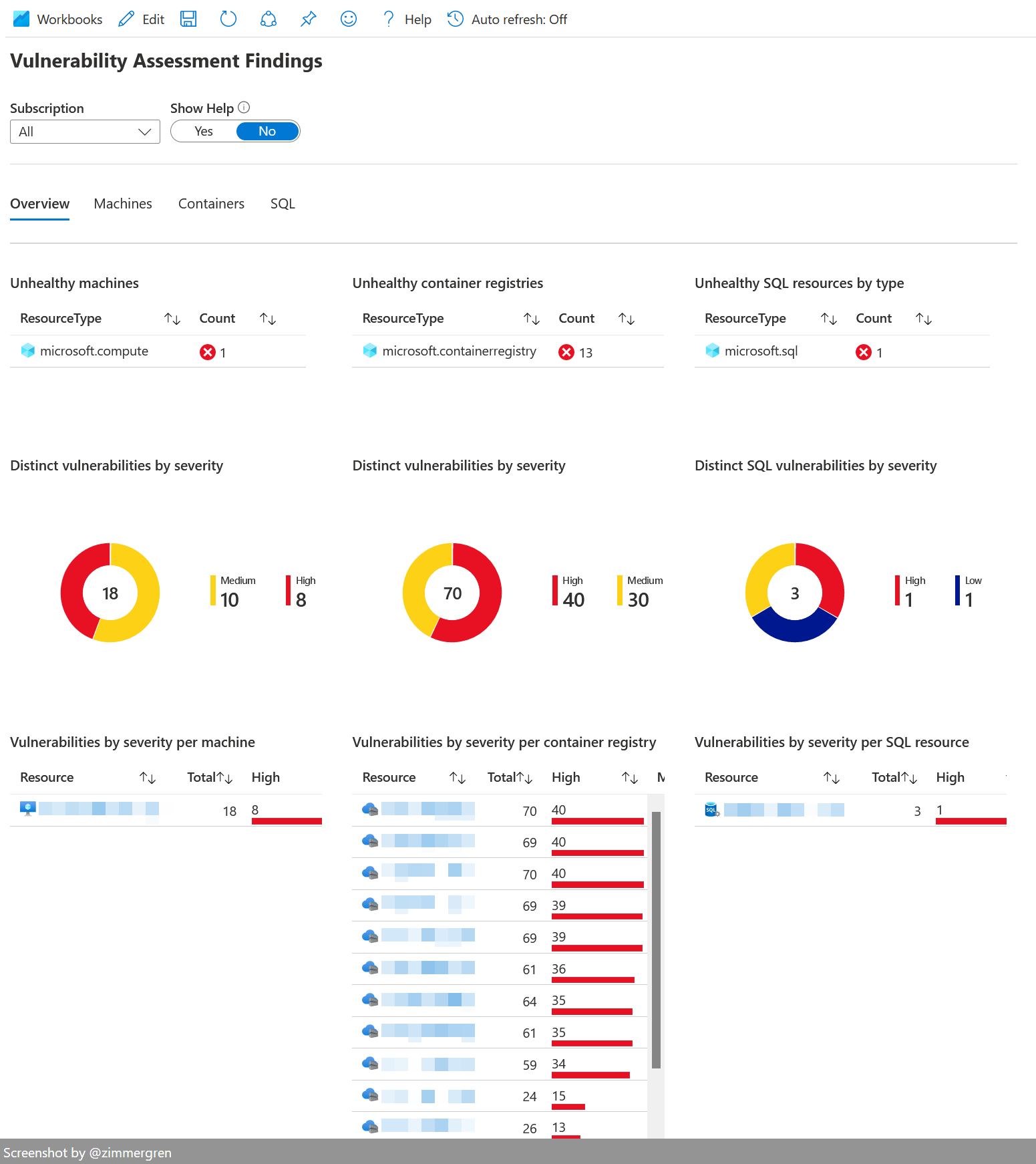
We can see that there are a number of container registries that require some attention. I selected these because I know there are some legacy images in my old Azure Container Registries.
When you've mitigated some of the issues, for example in Container Instances, you should roll the fixes out and then I would recommend purging any old images that are no longer required.
See more about purging container images here:
- Purging container images from Azure Container Registry (Zimmergren.net)
Community Workbooks
To further our knowledge of how workbooks are designed, we can use some community workbooks. I strongly recommend looking at these, as they can help you understand how to query and design your workbooks to get you the data and insights you need.
I've learned plenty of my workbook skills from the community workbooks. There are some genuinely clever people out there.
My first tip here is to view this link, and then be amazed.
- Azure/Microsoft-Defender-for-Cloud (GitHub)
Looking at the initial list of worbooks here, you will understand that there's a lot to learn here, and plenty of resources to derive our workbooks from.
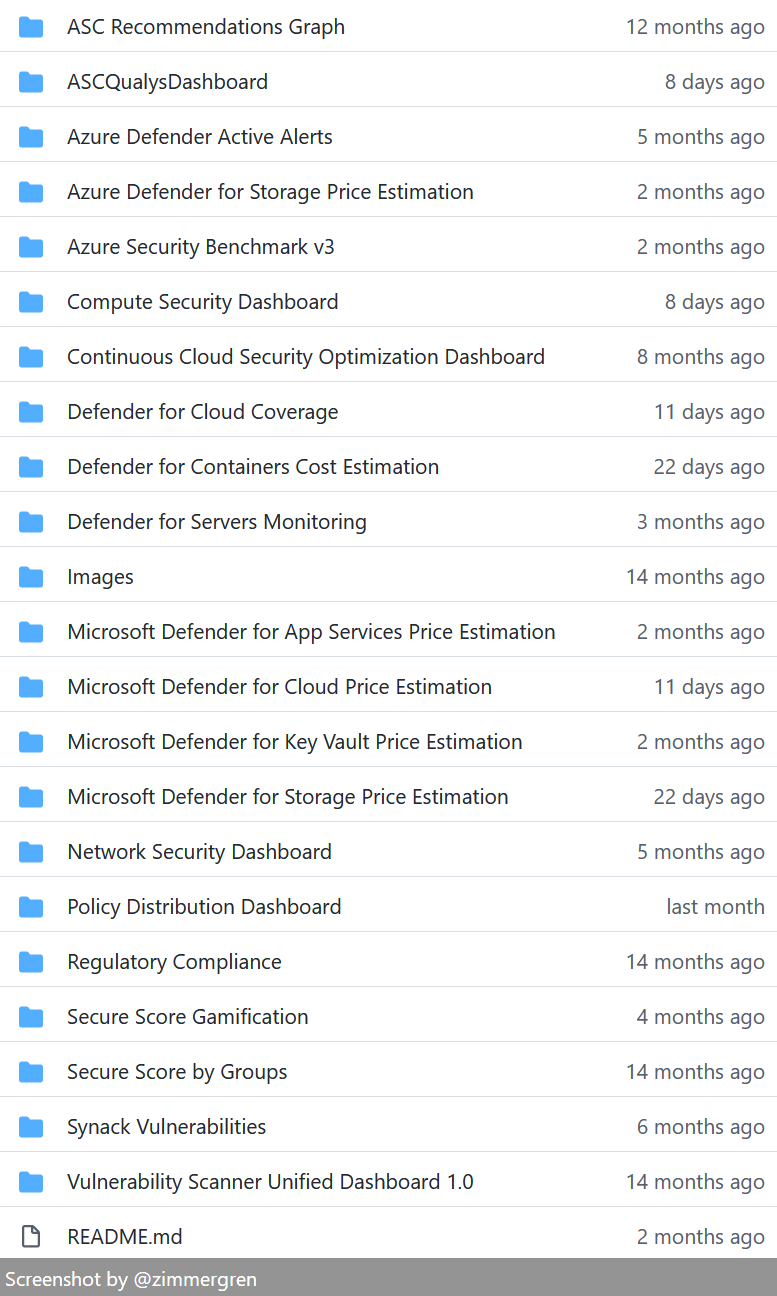
If you want to take your workbook skills one step further, check out the Azure Monitor workbooks on GitHub. This is truly an amazing set of workbooks that are easily integrated into our everyday operations.
I will leave you with exploring all the workbooks. Let me know in a year from now when you've had a chance to review them all 😂
Custom Workbooks
Whether it's an enhancement or modification to existing workbooks or a complete build-up from scratch doesn't matter. We can customize our workbooks almost endlessly is a strong point in Azure.
I have built several custom workbooks to support my workloads. Some workbooks are derived from the existing work of others. However, most are created from the necessity of our internal requirements for monitoring and insights.
Here are some ideas for you, based on what I've designed for my daily internal operations management. I've got a "main" workbook that highlights the most important things I want to surface during daily operations standup, etc.
- Expiring App Service Certificates. Read more about that in my other post, Quickly discover any expiring certificates for Azure App Services.
- New Exceptions. Shows only exceptions that didn't previously happen, and that are now happening in the selected time period.
- Containers. Show me all running Azure Container Instances across all subscriptions, including their current health and relevant status and information.
- Custom Telemetry. When your application sends custom logs and telemetry, you may sometimes want to keep tabs on specific signals coming in. In my workbook, I keep track of the most critical and interesting signals to ensure we're on top of our monitoring and operations game.
- Security signals. Surface specific security-related signals that we don't easily see unless we perform several queries. Here, they're automatically rolled up for me.
The use cases for custom workbooks can be made endlessly long. For me, it's all about serving the purpose of securing daily operations and healthy cloud infrastructure.
Number 3: Recommendations
Perhaps the most common tactic with Microsoft Defender for Cloud is to head over to the Recommendations section and take a look at what we should improve next.
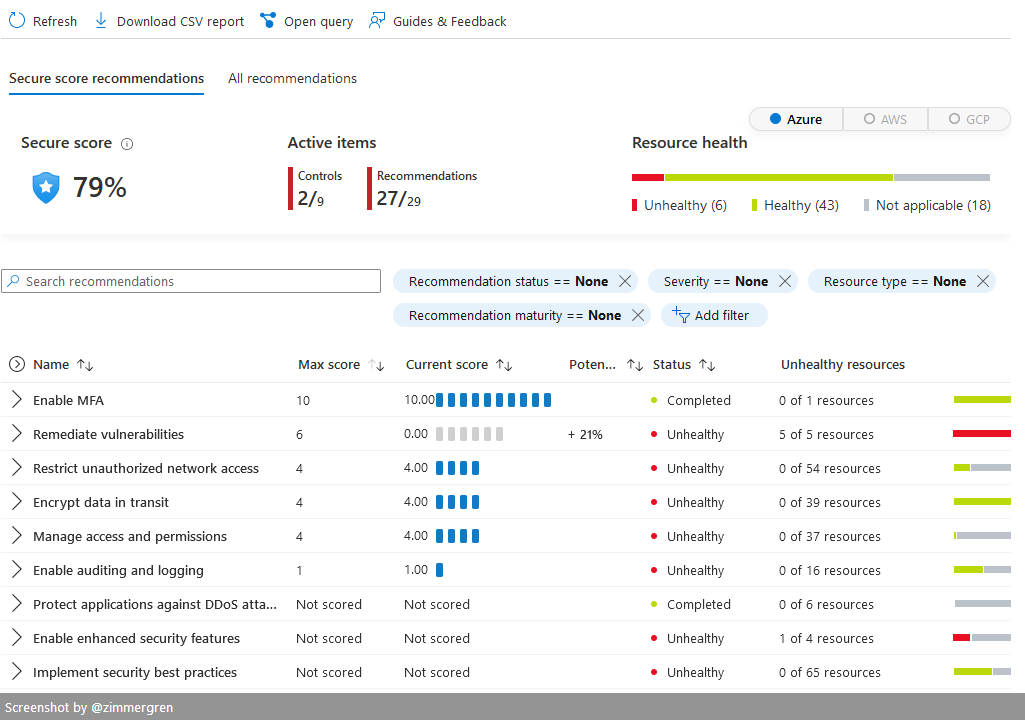
I like this because it's easily filterable, and we can get a quick overview of our secure score and unhealthy resources.
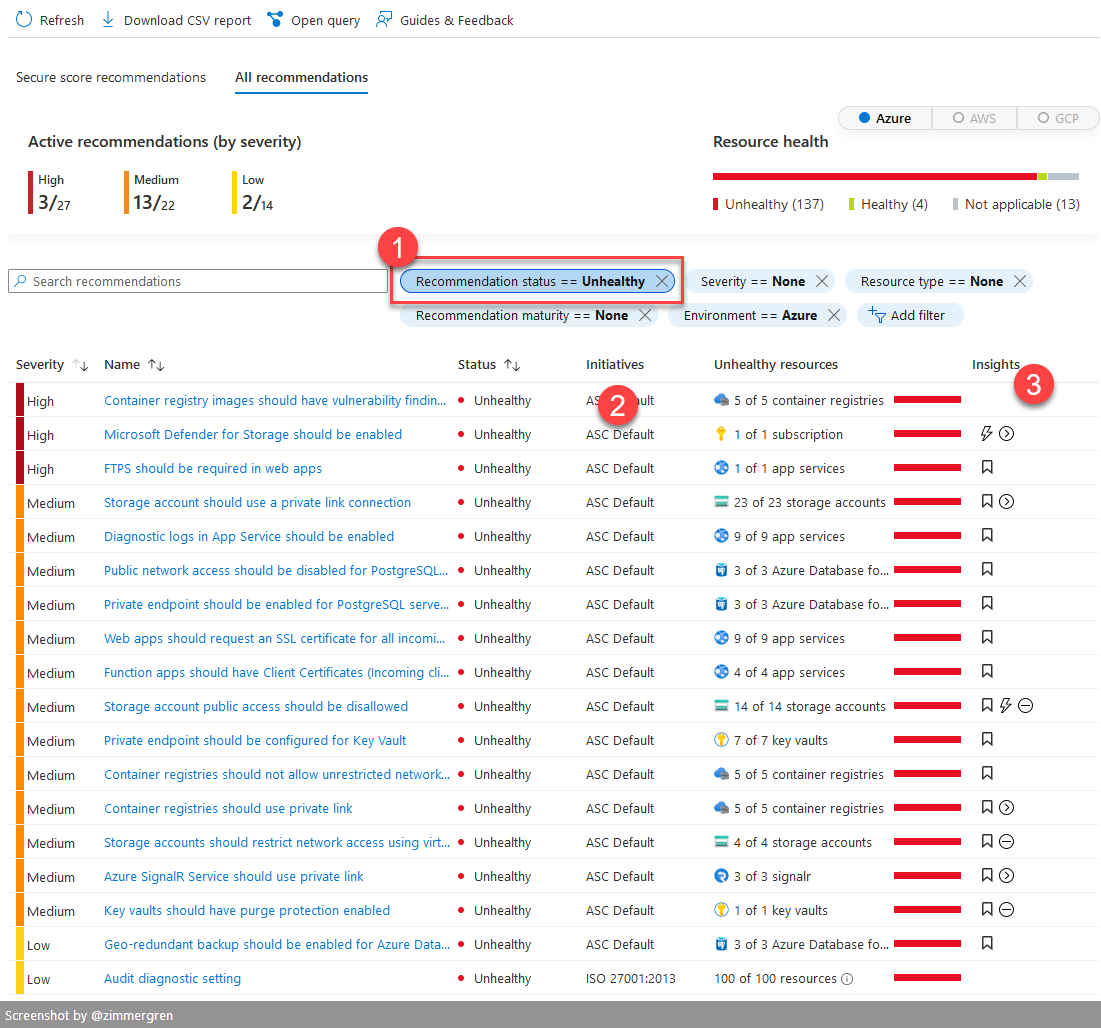
Below, I have filtered the list from a subset of subscriptions to only show unhealthy recommendations (1). We can see from what initiative the recommendation originates (2), and see an overview of the insights (3).
In the below screenshot, I've selected a range of subscriptions that are less critical but have some room for improvement, to showcase what it could look like.
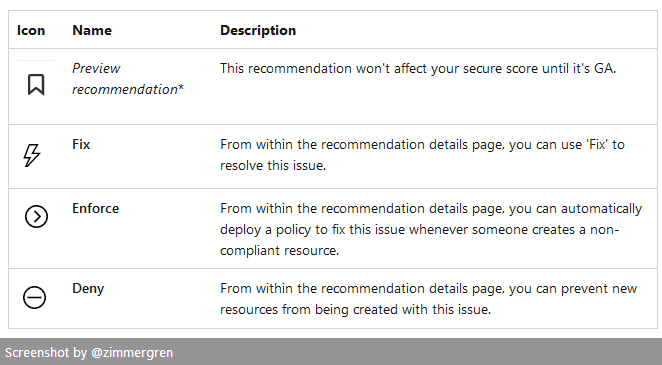
To better understand what the insights column means, here's a legend from Microsoft Docs.
Selecting any of the recommendations will give you more details about how to remediate the issues, and sometimes offer the "Fix" to automatically take care of the configuration for you.
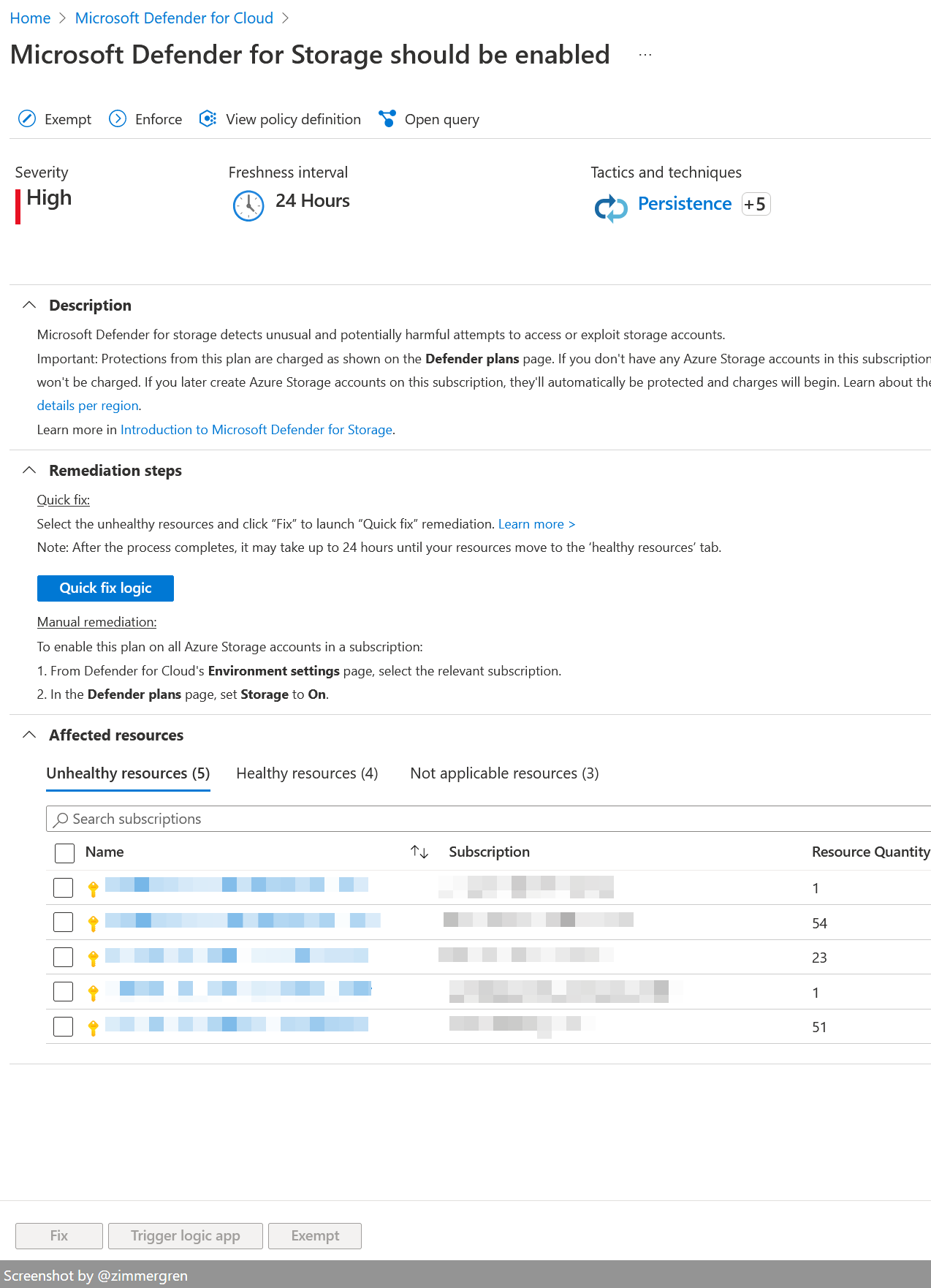
The insights we get here are amazing. Just remember to understand the implications of any "Quick fix" you perform, and also of any manual remediation.
For example, I recently wrote about understanding the real cost of enabling Microsoft Defender for Cloud. Estimate the price of enabling this for your workloads before you hit the quick fix button.
Bonus feature: Continuous export.
I could write a lot about the continuous export capability. Previously, I published the article track your Secure Score over time in Azure. That post walks through how to configure continuous export, and ways to utilize the data with some built-in workbooks.
Read more:
- Track your secure score over time in Azure (Zimmergren.net)
- Continuously export Microsoft Defender for Cloud data (Microsoft Docs)
Summary and resources
It's an absolute thrill to have this tool at our fingertips. It can greatly help us navigate the ever-changing cloud security landscape.
- Estimating the real cost of Microsoft Defender for Cloud (Zimmergren.net)
- Create rich, interactive reports of Defender for Cloud data (Microsoft Docs)
- What is Microsoft Defender for Cloud? (Microsoft Docs)
- Track your Secure Score over time in Azure (Zimmergren.net)
- Continuously export Microsoft Defender for Cloud data (Microsoft Docs)








Recent comments