
Using the Azure Resource Graph to improve your Azure Governance game
Learn about some of my key scenarios for using the Azure Resource Graph to gain a better understanding of my Azure resources. This is a great tool for your Azure Governance toolkit.
The official documentation has an excellent overview of what the Azure Resource Graph is. It should give you a good overview of the technical capabilities.
In this post, I want to outline some of the use cases that I think are noteworthy. Let's take a look at these cases and see how the Azure Resource Graph can help.
Simple. Elegant. Quick insights. I can vouch for the Azure Resource Graph!
Scenarios
Here is a set of scenarios, to give insights into how I use the Azure Resource Graph regularly to stay on top of Azure Governance. This helps me in ensuring policy compliance, security posture stays intact, ad-hoc resources don't sprawl out of control, and more.
The examples are from a demo tenant so no real data is surfaced. That means less insightful dashboards and query results, but on the other hand, the results will vary in your environment regardless.
Use case: Extended audits and reviews
In Azure, there are a lot of tools available to perform regular configuration and security audits. I have a set of tools I use myself regularly to strengthen the security posture and general configuration of my infrastructure, code, and processes.
The Azure Resource Graph is part of my arsenal. I am highlighting more examples in future posts, but generally, it is powerful for things like this.
resources
| where type == "microsoft.storage/storageaccounts"
| where aliases["Microsoft.Storage/storageAccounts/supportsHttpsTrafficOnly"] == "false"
or aliases["Microsoft.Storage/storageAccounts/enableFileEncryption"] == "false"
or aliases["Microsoft.Storage/storageAccounts/enableBlobEncryption"] == "false"
| project name, kind, resourceGroup, subscriptionId
In this query, I wanted to quickly discover any storage account where HTTPS was not enabled, or where File or Blob encryption is disabled.
Sometimes I want to review some configuration across multiple subscriptions quickly, and this is one way for me to do that with ease. The example here is trivial. However, it should provide enough insight to understand that we can query our resources tailored to our own needs. Not just what the Security Center or our other tools provide.
Let us continue with a few use cases, and get into security-audit topics in another post.
Use case: Cross-subscription resource insights
In the Azure Graph Explorer user experience in the Azure Portal, you have a selector where you can easily select what subscriptions the queries should target. The current UI looks like this:
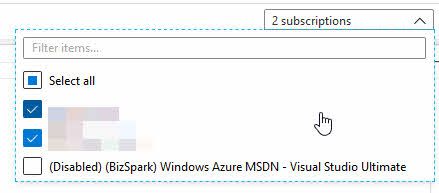
You can also filter by subscription ID from the Azure CLI or PowerShell, or from the Azure Portal in the query, too.
resources
| where subscriptionId == 'YOUR SUBSCRIPTION GUID'
I find this particularly interesting given I have plenty of subscriptions to manage across the globe. I can gather insights or specific properties from all my resources, regardless of the location, which helps to build an understanding of what we have.
Use case: Determine what impact an Azure Policy action can result in
I deploy Azure Policies throughout various environments. Sometimes, these come with actions, like a "deny" action to disallow certain resources to be created, because we have made that decision for some reason.
Before even starting to roll out policies, we can use the Azure Resource Graph to query the resources we have. We can now determine whether our changes could impact any already existing resources.
- In the Ctrl+Alt+Azure Podcast, we discussed Azure Policy a bit, if you want to drill more into what that is.
If you are drilling down into your resources and looking for configurations to disallow, you can now convert your query and construct an Azure Policy, and then roll it out.
Use case: Continuously discover changes.
I manage quite the amount of subscriptions across different management groups and directories. For me to get the insights I need, the Azure Resource Graph is an excellent tool in the tool basket.
For some projects, there are individuals with access to specific resources, resource groups, or a set of resource groups. With this delegated access, it can quickly become hard to get an overview of the changes happening in your environment. Mission-critical resources never have any delegated access. However, we also have a lot of non-production workloads and supporting services, where changes could potentially happen.
Enter the Azure Resource Graph change details. There is the Resource Graph SDK, with support for finding detected change events. It helps me stay on top of what has changed, and by whom or what process.
Things I like with the change events:
- Get changes for any of your resources.
- Compare the configuration in detail "before" and "after" the resource was modified.
- When something breaks, head over to the resources and check out their recent changes to learn if there could be something related to the current broken environment.
- Determine whether an automated process or an individual may have changed something that leads to unwanted results.
- It helps me stay on top of my Azure Governance game every day.
The Microsoft docs have everything you need to know about getting started with querying for changes in your resources:
- Azure Resource Graph - Get resource changes (Microsoft)
Use case: Visualize your inventory
For me, it always helps to paint a picture to understand things. Whether this is a solution architecture, infrastructure requirements, or how I plan to build an outdoor wooden deck.
With the Azure Resource Graph, we can craft queries to help us get relevant data, as we discussed in the previous sections. We can use the built-in capabilities to visualize the results on the fly as we gain our insights. If you now have a set of queries you run regularly, you can save these and save the visualizations to you always look at updated data.
Here is a chart, building on an earlier example of App Services. In this minimal subscription, I can easily see what kinds of app services I have.
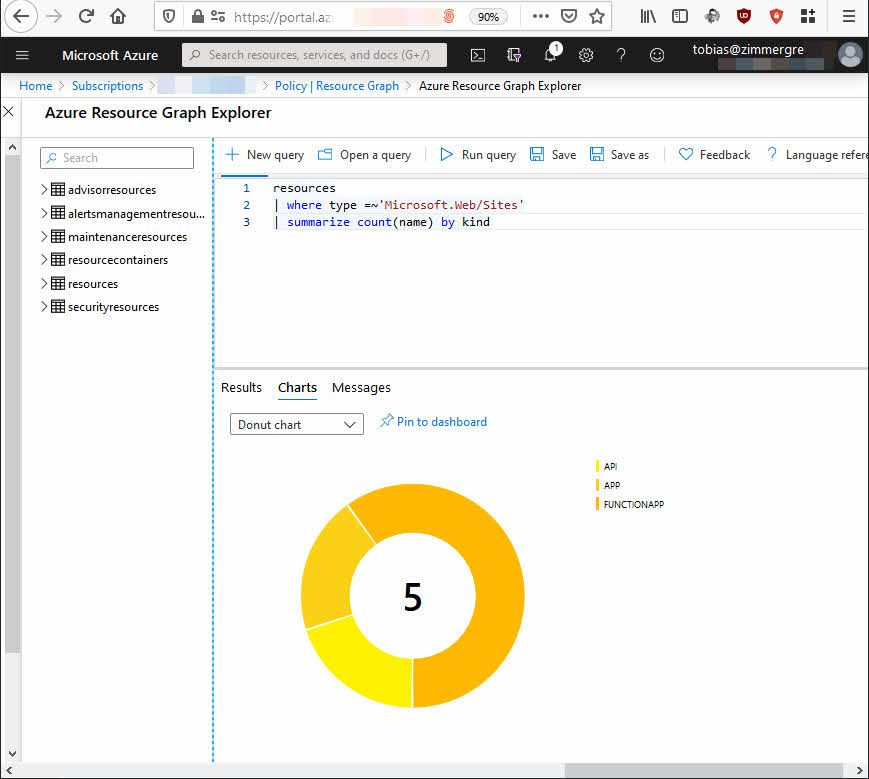
While I cannot share any details or screenshots of any more substantial production data in this blog, the concept remains the same. I can quickly drill down into my various resources, in an instant, and get an excellent visual overview.
Part of my job is ensuring the ongoing success of anything in the cloud. I like to stay up to date with what is happening, what resources I have, and what the current state of my subscriptions are.
Dashboards come in handy to get quick insights into what I have and what I think is essential to review regularly.
Below are examples of how it can look like, not my real dashboards.
Clicking "Pin to dashboard" pins it to the current dashboard. If you are unsure about what your selected dashboard is, head on over to "Dashboards" first. Create a new one or use an existing one, and then head over to the Azure Resource Graph again to pin.
I took my two example queries from above and pinned them to a new dashboard to showcase this functionality. I like it.
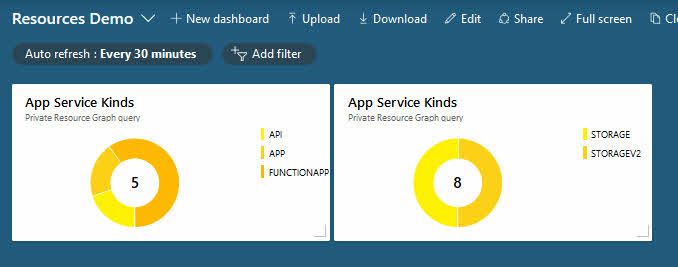
Tip: If you decide to do real dashboards, make sure to save your queries with proper names, as they will appear in the dashboard as above. You can perhaps notice that I re-used the same query window and my saved query for both of these examples. In my production environments, I have a lot of saved queries I resort to regularly.
Another great tip here. Enable the "Auto-refresh" and put the dashboard in a browser on any spare monitor or TV. You have an automatically updating view of your current landscape. For me, with my production workloads, there can be quite some changes, and of course, a lot more things to look at than the above examples.
See what's coming, and submit ideas.
To stay updated with what capabilities exist, are being worked on, and have been suggested, I like the Azure Feedback site. You can also easily submit your feedback and feature requests here, and collect votes on the ideas.
- Azure Resource Graph feedback and ideas (Microsoft)
Summary and links
This article was a short write-up about how I see benefits with the Azure Resource Graph. Recently, I have had chats with people asking how to get an overview of their Azure environments. More specifically, how we can more easily avoid losing control as the environments grow.
There are many solutions and ways to go about things. This is just another set of tools for your toolbox. I hope it helps.
General overviews:
- Using the Azure Portal to run Resource Graph queries (Microsoft)
- Using PowerShell to run Resource Graph queries (Microsoft)
- Using the Azure CLI to run Resource Graph queries (Microsoft)
- Understanding the Azure Resource Graph query language (Microsoft)
- Azure Resource Graph - Get resource changes (Microsoft)
More about queries:
- Starter Resource Graph queries (Microsoft)
- Advanced Resource Graph queries (Microsoft)
Header photo by Bernd Klutsch on Unsplash






Recent comments