Exam Study Guide: SC-100 - Microsoft Cybersecurity Architect Expert
Table of Contents
I recently decided to sit the SC-100: Microsoft Cybersecurity Architect Expert exam which, if you pass, grants you the certification with the same title. I am happy to share that I passed the exam.
In this post, I will share some details about the experience, and links and insights for how to prepare for this exam using only free resources.
Many of the resources I collected comes from Microsoft Learn and Microsoft Docs, where there's an incredible pool of knowledge and experience bundled together in a self-paced learning format. More on the specific learning paths below.
Establish your expectations
To set the scene and align expectations, I want to take a moment to share my thoughts on this exam.
This is not a deep security exam - on the contrary, it's very wide and will ask you about knowledge across the stack of products in the Azure security space. The exam does test your ability for some advanced scenarios, but without the deep technical knowledge like specific commands or lines of code.
You should consider this exam if you're a Microsoft cybersecurity/security architect with expertise in designing and evolving your organization's security strategy. Studying for this will help identify any gaps in your knowledge that may prove fruitful in your continued adventure in the ever-changing security landscape.
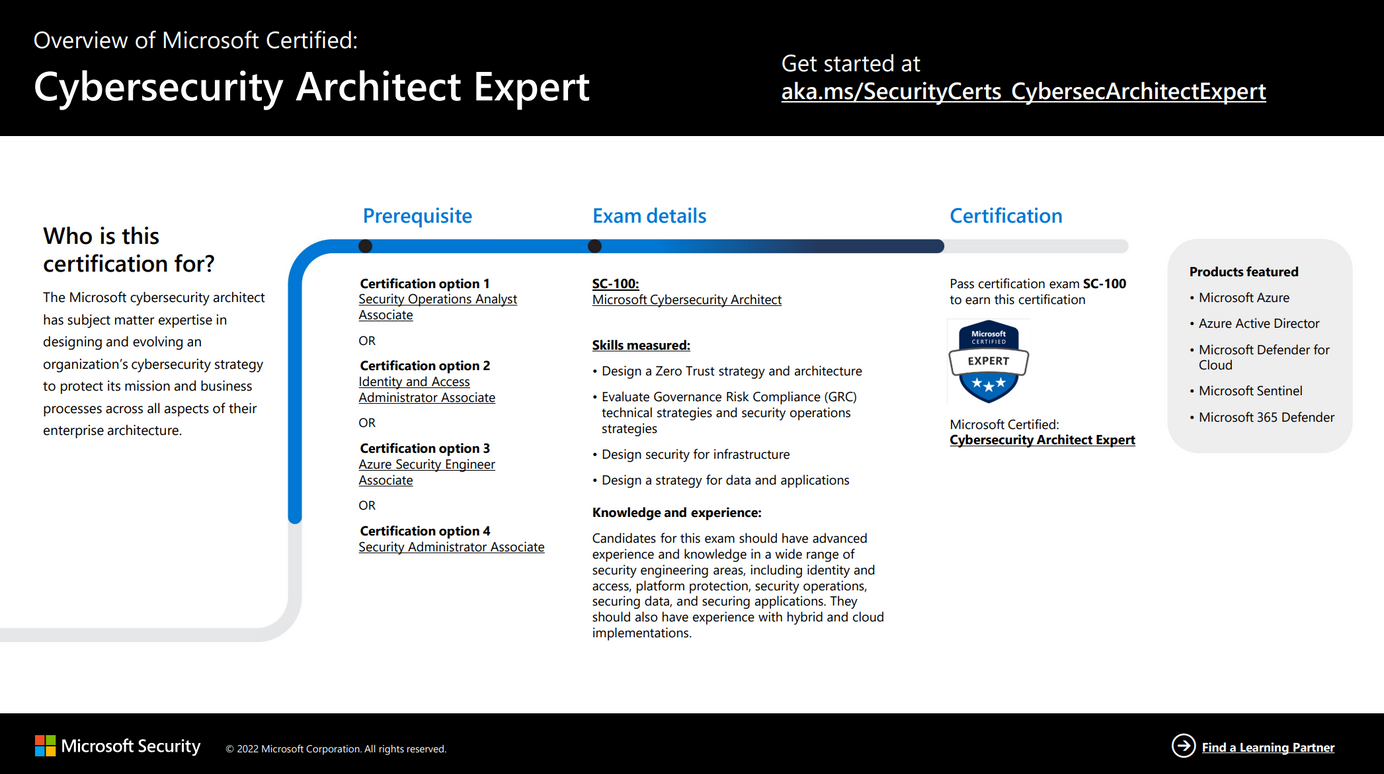
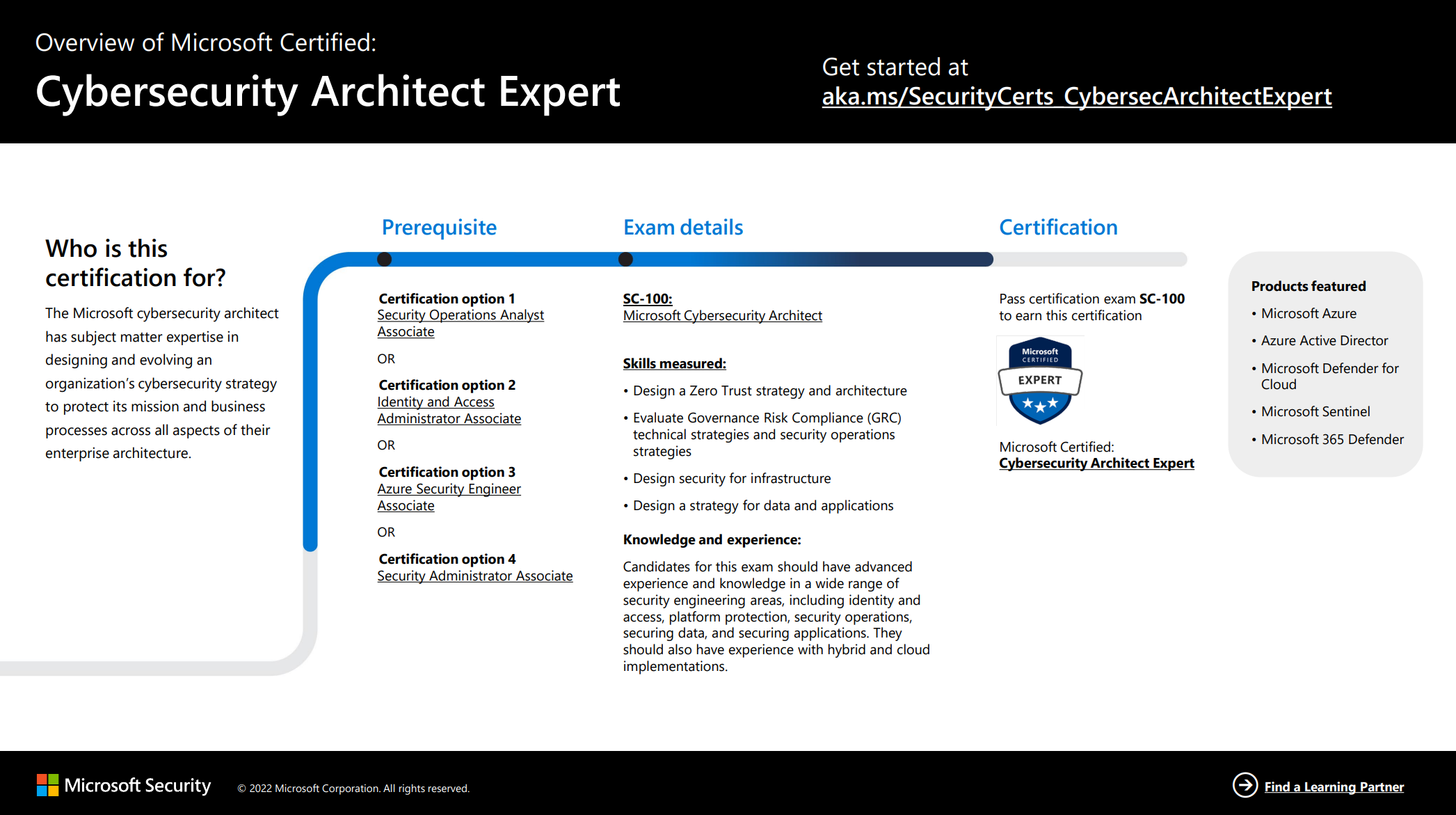
Pre-requisites
You can pass the exam regardless of previous exams. However, to earn the certification you also need to pass at least one of the pre-requisite exams.
I previously outlined some of my experiences in passing the AZ-500 exam. Below is a picture illustrating the prerequisite exams if you want to earn the SC-100 certification after passing the exam.
Study Guide format
The below sections of this guide will include both resource documentation and free training from Microsoft Learn. Each section covers both angles, to best cater for the way you learn best.
This guide will detail these types of resources for each section:
- Resource links
Microsoft Docs or Microsoft Learn-modules, other relevant documentation for SC-100. - Training
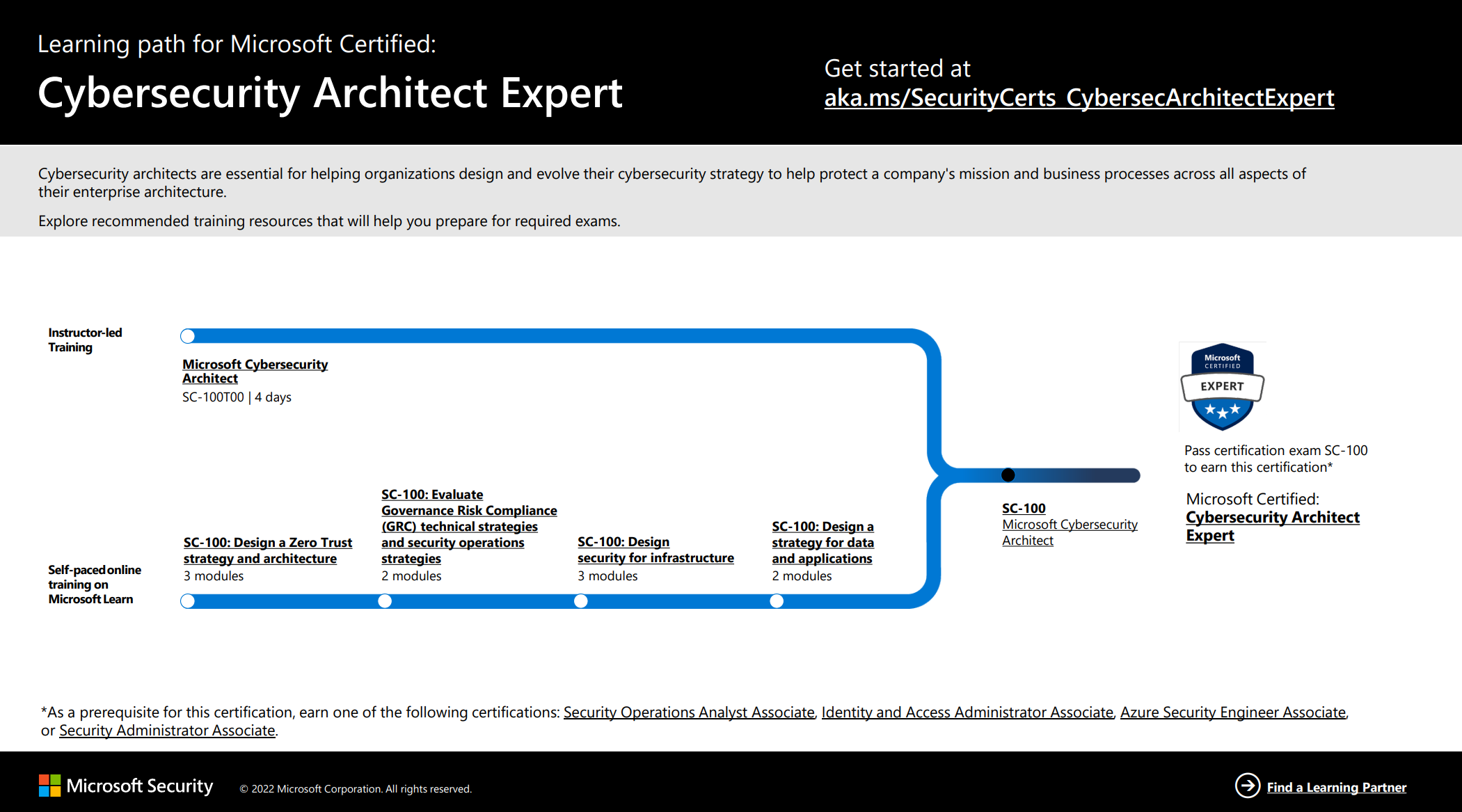
The full and free Microsoft Learn modules targeting SC-100 explicitly.
Looking at the learning path with Microsoft Learn, there are four modules that builds up the preparations and groundwork for successfully passing the SC-100 exam. You will find links to them all in the content below.
Study Guide
I generally say that there are two ways around taking an exam.
Either you have the experience and knowledge and will take the exam without preparation, or you want to prepare by reading up or do some training on the areas the test will cover.
Below are links to the resources and training recommended to pass the SC-100 exam. If you want the latest insights on what the exam covers, download the SC-100 Study Guide from Microsoft.
Unfortunately, the official study guide doesn't come with links to relevant resources across the Microsoft documentation or learning platforms. Therefore, I am adding links to the items covered so you can more easily find the right resources in preparation for the exam.
Tag along this guide to find out where you can get the best material to further your preparations and studies in this area. Good luck!
Design a Zero Trust strategy and architecture (30-35%)
The links and resources in this section covers most of the content required to understand designing a Zero Trust strategy and architecture.
Build an overall security strategy and architecture
- Identify the integration points in an architecture by using Microsoft Cybersecurity Reference Architecture (MCRA)
- Translate business goals into security requirements
- Translate security requirements into technical capabilities, including security services, security products,
and security processes - Design security for a resiliency strategy
- Integrate a hybrid or multi-tenant environment into a security strategy
- Develop a technical and governance strategy for traffic filtering and segmentation
Design a security operations strategy
- Design a logging and auditing strategy to support security operations
- Develop security operations to support a hybrid or multi-cloud environment
- Design a strategy for SIEM and SOAR
- Evaluate security workflows
- Evaluate a security operations strategy for incident management lifecycle
- Evaluate a security operations strategy for sharing technical threat intelligence
Design an identity security strategy
Note: includes hybrid and multi-cloud
- Design a strategy for access to cloud resources
- Recommend an identity store (tenants, B2B, B2C, hybrid)
- Recommend an authentication strategy
- Recommend an authorization strategy
- Design a strategy for conditional access
- Design a strategy for role assignment and delegation
(See also: best practices for Azure AD roles) - Design security strategy for privileged role access to infrastructure including identity-based firewall rules, Azure PIM
- Design security strategy for privileged activities including PAM, entitlement management, cloud tenant
administration
Training path
Check out this training path and the accompanying modules to quickly ramp up on this topic.
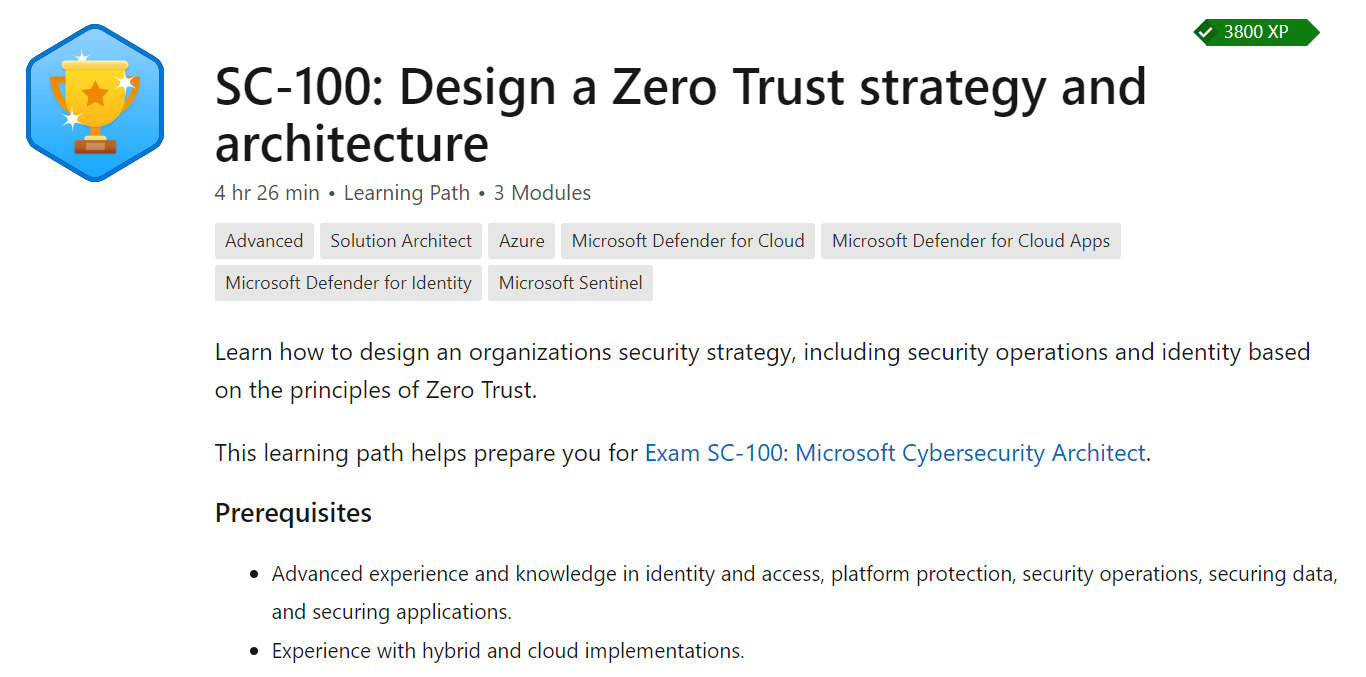
Training Path:
- Training Path: Design a Zero Trust strategy and architecture
Included modules:
- Module: Build an overall security strategy and architecture
- Module: Design a security operations strategy
- Module: Design an identity security strategy
Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies (20–25%)
Documentation
Design a regulatory compliance strategy
- Interpret compliance requirements and translate into specific technical capabilities (new or existing)
- Evaluate infrastructure compliance by using Microsoft Defender for Cloud
- Interpret compliance scores and recommend actions to resolve issues or improve security
- Design implementation of Azure Policy (Module in Microsoft Learn)
- Design for data residency requirements
- Translate privacy requirements into requirements for security solutions
Evaluate security posture and recommend technical strategies to manage risk
- Evaluate security posture by using benchmarks (including Azure security benchmarks, ISO 2701, etc.)
- Evaluate security posture by using Microsoft Defender for Cloud
- Evaluate security posture by using Secure Scores
- Evaluate security posture of cloud workloads
- Design security for an Azure Landing Zone
- Interpret technical threat intelligence and recommend risk mitigations
- Recommend security capabilities or controls to mitigate identified risks
Training path
Check out this training path and the accompanying modules to quickly ramp up on this topic.
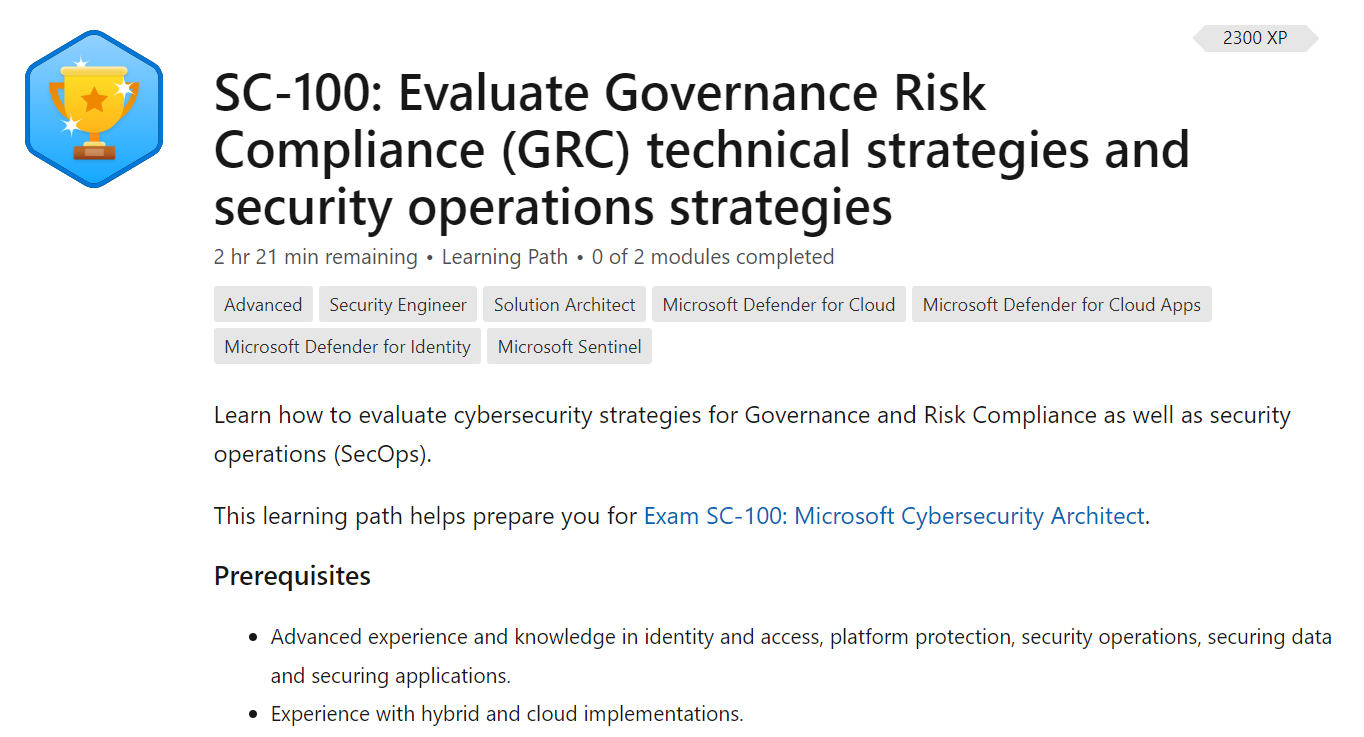
Training Path:
- Training Path: Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies
Included modules:
- Module: Evaluate a regulatory compliance strategy
- Module: Evaluate security posture and recommend technical strategies to manage risk
Design security for infrastructure (20–25%)
Documentation
Design a strategy for securing server and client endpoints
NOTE: includes hybrid and multi-cloud
- Specify security baselines for server and client endpoints
- Specify security requirements for servers, including multiple platforms and operating systems (Make use of the Azure Security Benchmark to improve your knowledge here)
- Specify security requirements for mobile devices and clients, including endpoint protection, hardening,
and configuration - Specify requirements to secure Active Directory Domain Services
- Design a strategy to manage secrets, keys, and certificates
- Design a strategy for secure remote access
Design a strategy for securing SaaS, PaaS, and IaaS services
- Specify security baselines for SaaS, PaaS, and IaaS services
- Specify security requirements for IoT workloads
- Specify security requirements for data workloads, including SQL, Azure SQL Database, Azure Synapse, and Azure Cosmos DB
- Specify security requirements for web workloads, including Azure App Service
- Specify security requirements for storage workloads, including Azure Storage
- Specify security requirements for containers
- Specify security requirements for container orchestration
Training path
Check out this training path and the accompanying modules to quickly ramp up on this topic.
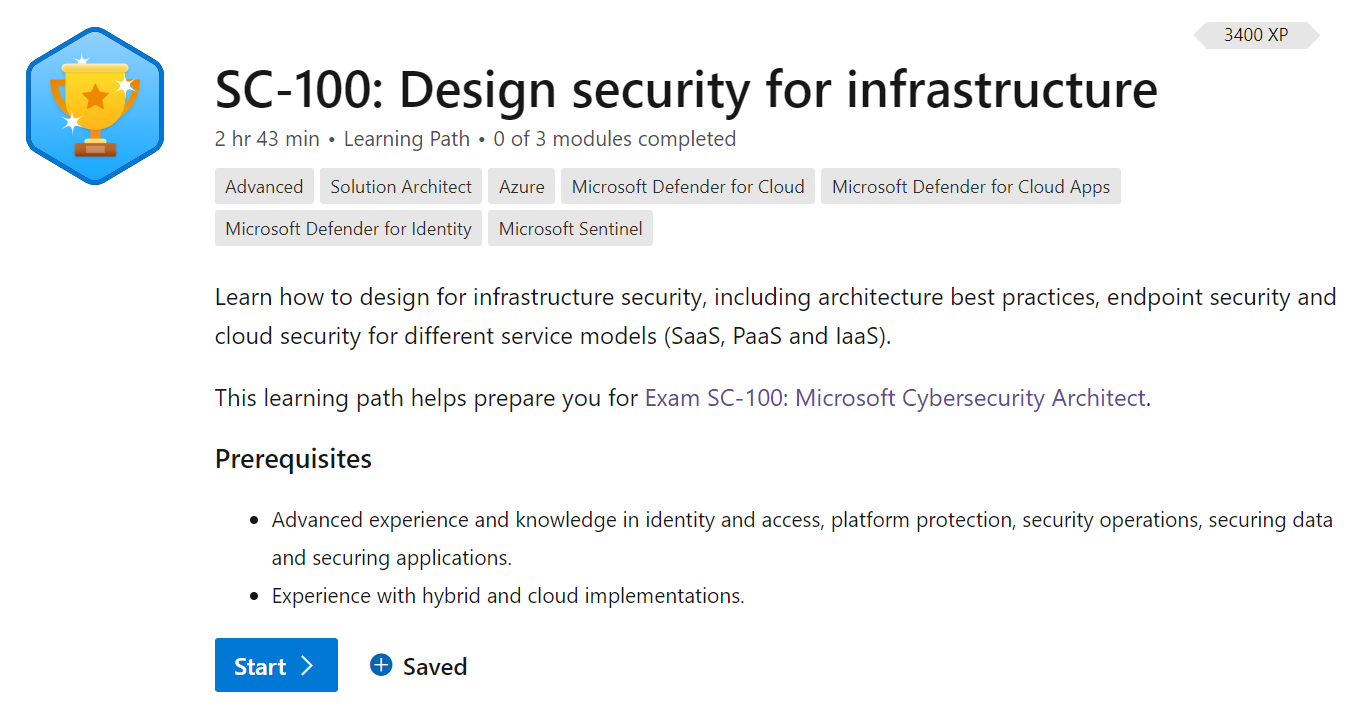
Training Path:
- Training Path: Design security for infrastructure
Included modules:
- Module: Understand architecture best practices and how they are changing with the Cloud
- Module: Design a strategy for securing server and client endpoints
- Module: Design a strategy for securing PaaS, IaaS, and SaaS services
Design a strategy for data and applications (20–25%)
Documentation
Specify security requirements for applications
- Specify priorities for mitigating threats to applications
- Specify a security standard for onboarding a new application
- Specify a security strategy for applications and APIs
Design a strategy for securing data
- Specify priorities for mitigating threats to data
- Design a strategy to identify and protect sensitive data
- Specify an encryption standard for data at rest and in motion
Training path
Check out this training path and the accompanying modules to quickly ramp up on this topic.
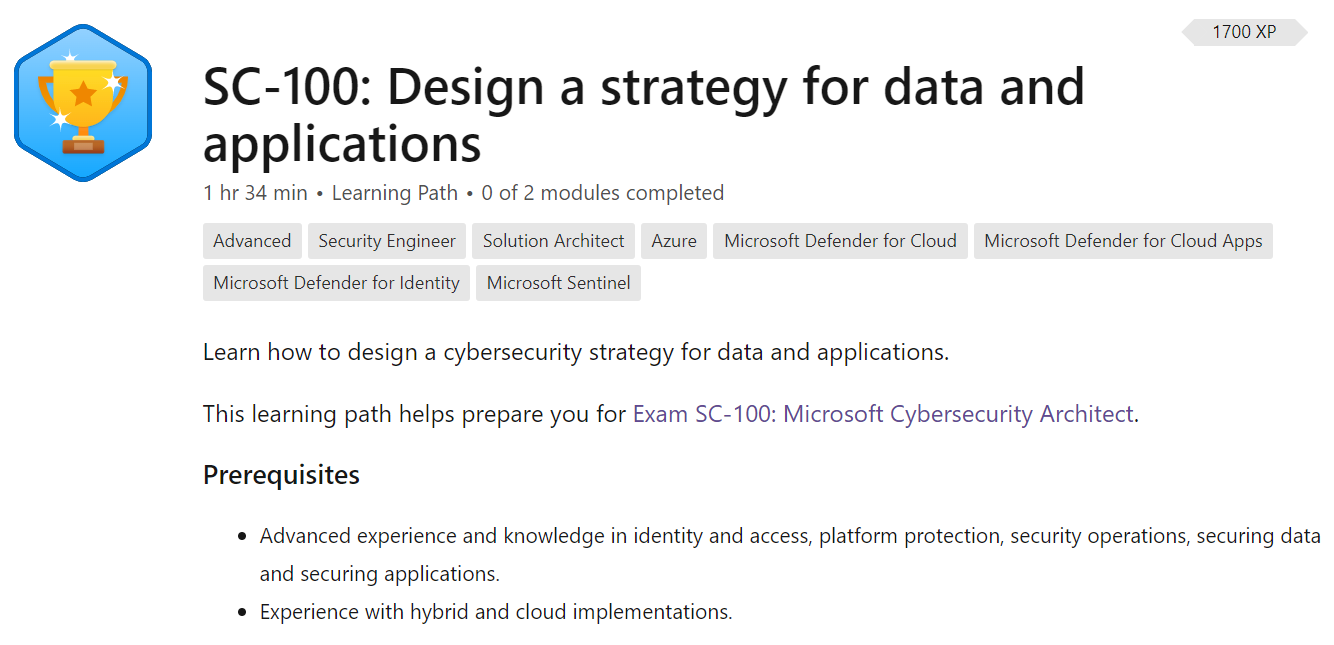
Training Path:
- Training Path: Design a strategy for data and applications
Included modules:
Extras
While searching for additional insights to put into this post, I found some relevant study guides that can help you ramp up quicker.
SC-100 Study Cram (Video)
John Savill has a great "Study Cram" session that covers many of the topics that you'll be exposed to during this exam. While the video isn't going to get you all the knowledge you need (that's on you to learn), it has a nice "recap" of what the exam expects you to know, and an intro to those concepts.
SC-100 Study Guide (Book)
There is a pre-order available for the Exam Ref SC-100 book, aiming to be released in February 2023. The book is authored by some well-known names in the Microsoft security space. Keep an eye out for when it releases!








Recent comments