
Securing Microsoft Teams
Recently, Microsoft Teams adoption in organizations world-wide has skyrocketed. To keep up with this pace, here's a post about securing the Collaboration Experience, configuring Compliance, and a look at Security options!
Microsoft Teams is great. I use it every day for communication and collaboration with my colleagues, industry peers, partners and customers.
Recently, Microsoft Teams adoption in organizations world-wide has skyrocketed. With the rapid pace of on-boarding to the platform, it can be tricky to stay up to date with all the changes and configurations that you need to take a look at to ensure a secure experience across the board.
I want this post to be a reminder to myself, and to others, about where we can configure various security, compliance and safety settings for Microsoft Teams.
If you see something missing, please leave a comment, or contact me - I'll be sure to add it, and add your attribution. Thanks! 🚀
What to expect from this post.
This is a long post with a lot of information. Here's the overview, so you can see if you want to read the sections one by one, or simply scroll to your desired area to read about it.
I have divided the post in three areas. Collaboration experience, compliance, and security. Here's the overview of what I'm covering.
Update March 3rd, 2021:
- Added "Microsoft Teams Connect"
- Added "Invite only meeting options"
- Added "Safe Links for Microsoft Teams"
- Added "Microsoft Teams Multi-Geo Support"
- Added "Disable attendee videos in meetings"
Collaboration Experience:
- Microsoft Teams Connect
- Meeting permissions and policies
- Disable attendee videos in meetings
- Design for channel moderation
- Teams Apps settings
- Org-wide Teams Settings
- Designing and implementing External Access
- Designing and implementing Guest Access
- Designate roles for Teams meetings
- Understanding and configuring Cloud Recording
- Make use of Information Barriers
Compliance:
- Configure communication compliance
- Configure data retention
- Understand data location and sovereignty
- Microsoft Teams Multi-Geo Support
- eDiscovery in Microsoft 365
- Auditing user activity
Security:
- Review the Security Guide for Microsoft Teams
- Enforcing MFA
- Understanding Conditional Access for Microsoft Teams
- Enforce Conditional Access with Endpoint Manager
- Setting up Data Loss Prevention (DLP)
- Use Advanced Threat Protection (ATP)
- Use and review Cloud App Security
- Prevent users from installing trial apps and services
We've set the scene - let's jump in.
1. Collaboration experience
Below are some of tips and resources for strengthening the security posture for Microsoft Teams in your organization. The below configurations can impact the collaboration experience for your users.
Share channels with Microsoft Teams Connect
During Microsoft Ignite 2021, Microsoft announced Microsoft Teams Connect. This makes it easy for anyone to share channels with anyone. Internal, and externals alike.
Note: This is in a private preview when this post is written; it will be rolled out globally during 2021.
For admins, it might be interesting to know that you have granular controls to manage how this will work.
I wanted to mention this capability as it is a setting you'll need to understand, so you know how your organization is collaborating with others.
I will share more info about the hands-on experience with Teams Connect as it becomes generally available to everyone.
- Coming soon: When this has rolled out, I will share screenshots and steps for configuring.
Configure invite-only meeting options
Rolling out in 2021, as announced during Microsoft Ignite, Microsoft Teams will have a capability to configure invite-only meetings.
If a user were explicitly invited to the meeting, they're automatically admitted into the call. However, if someone is joining and were not on the invitation list, they will linger in the lobby until someone admits them.
This is a great capability to control who joins your calls, and to further strengthen the confidence we have in delivering sensitive information in remote meetings.
- Coming soon: When this has rolled out, I will share screenshots and steps for configuring.
Meeting Permissions & Policies
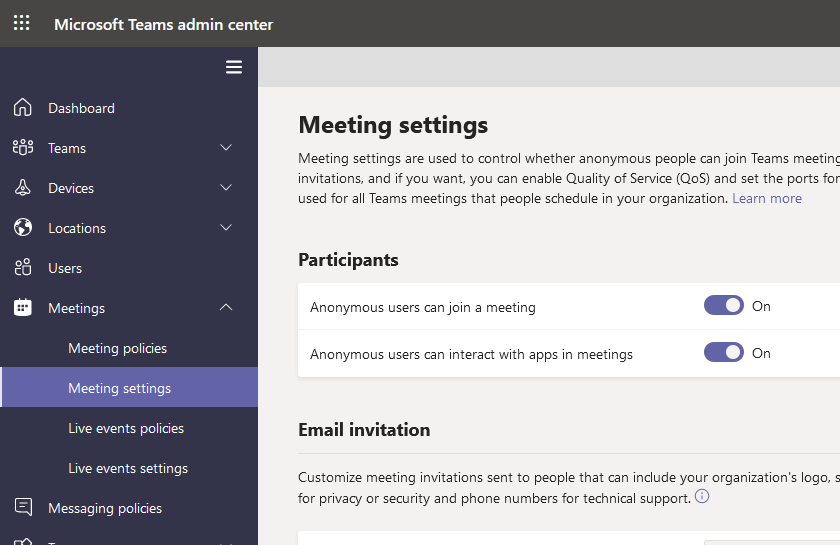
Changing participant permissions for meetings in Teams can be an important feature to understand. Your organization's default settings are always applied, but you can override this for specific meetings, too, if you want.
Noteworthy settings for instant/ad-hoc meetings include:
- Who can bypass the lobby?
- Get notified when callers join or leave the meeting.
- Choose who can present in your meeting.
- Preventing attendees from unmuting themselves.
The list of policies and settings for your org-wide configuration is too long to be listed here, so check out the links below for additional information on how to configure these policies and settings. These can be key to a secure experience across the organization, as well as ad-hoc meetings with internal and external parties.
Read more:
- Manage meeting settings in Microsoft Teams (Microsoft Docs)
- Manage meeting policies in Microsoft Teams (Microsoft Docs)
- Participant permissions for meetings in Teams (Microsoft Support)
Disable attendee videos in meetings
A killer feature that was long missing is the ability to disable attendee videos for all attendees, or for individual users.
Increasing the meeting safety is important, and is much like what we already can do with muting the participants - but for the video.
During Microsoft Ignite 2021, Microsoft announced that this capability is being rolled out during 2021. Stay tuned for it.
Design for channel moderation
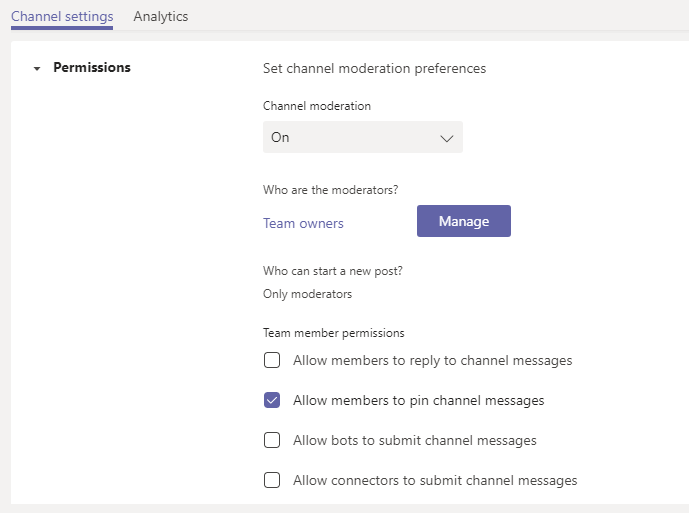
A team owner can turn on moderation to stay in control of who can perform specific tasks in the team and particular channels. This can be helpful if you use a channel for announcements only, or if you use Teams to present something and want to have threaded discussions on-topic, without any other posts/threads making noise.
If moderation is turned on for a channel, a moderator can:
- Start new posts in the channel. No other users can do this.
- Moderators can add other users as moderators, or remove them. However, they cannot remove an Owner as a moderator, as they have this permission inherently.
- Decide whether members can reply to existing channel messages.
- Decide whether bots and connectors can send messages to the channel.
Read more:
- Set up and manage channel moderation in Microsoft Teams (Microsoft Docs)
Teams Apps settings
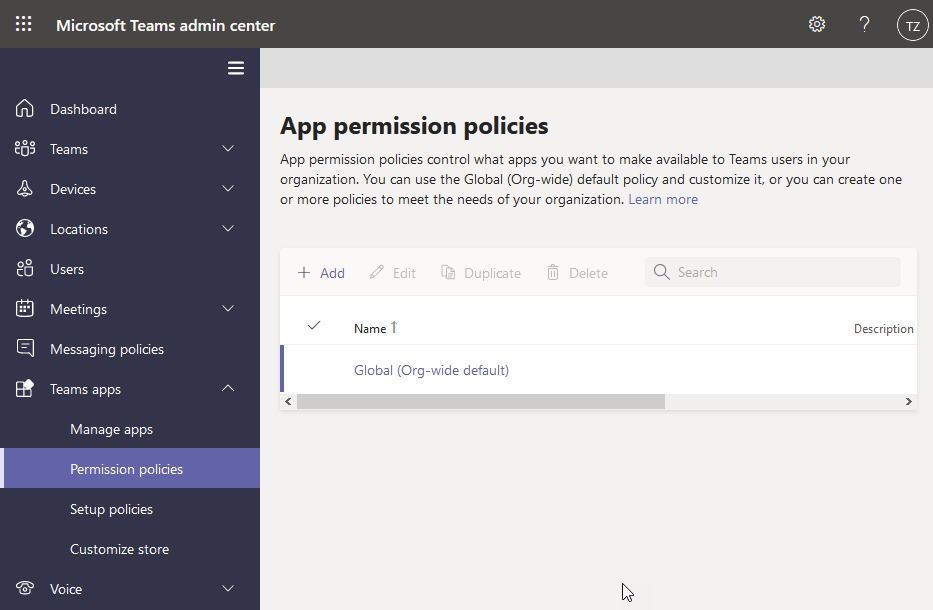
Manage apps for your organization in Teams apps, in the Teams Admin center. You can control apps, permission policies, app setup policies, and more.
Staying on top of these configurations help us stay in control of how apps are used in the organization, and can ultimately help us better secure our collaboration experience.
- Set policies to control what apps are available org-wide.
- Set policies to control what apps are available only to specific teams, or users.
- Pin the most important apps for your users, so they can easily find them.
Read more:
- Admin settings for apps in Microsoft Teams (Microsoft Docs)
- Manage your apps in the Microsoft Teams Admin Center (Microsoft Docs)
Org-wide Teams settings
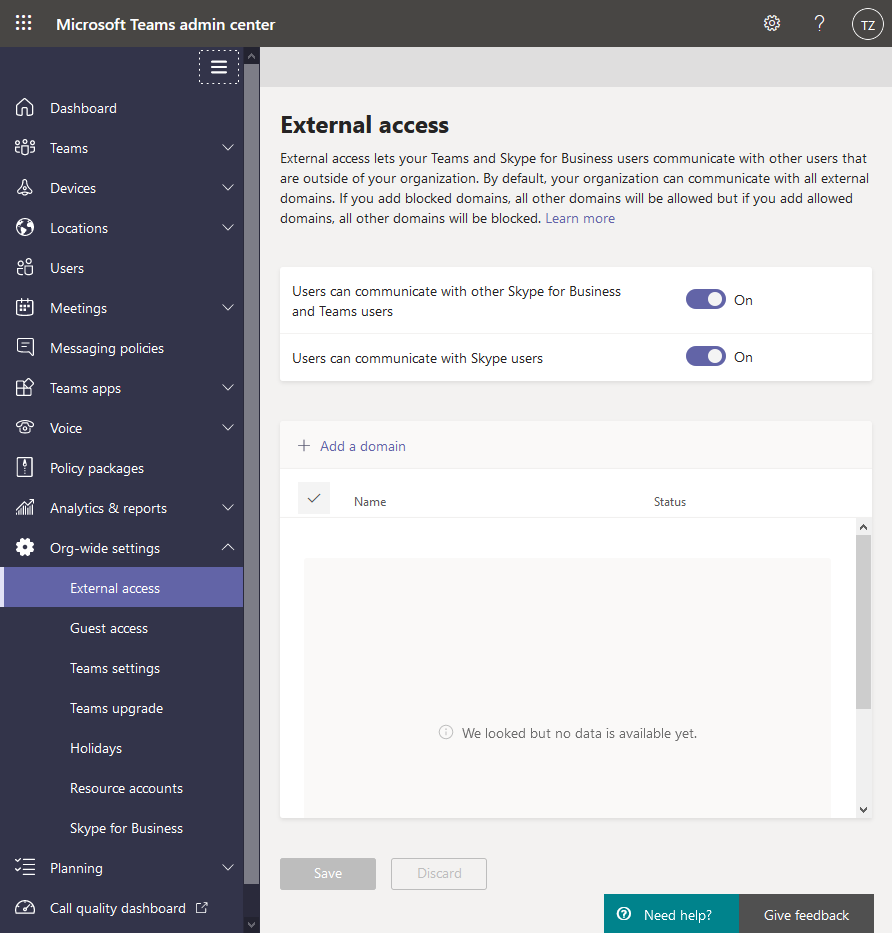
From the Microsoft Teams Admin Center, there are some org-wide settings available to help us stay in control of who can have access to our data and collaboration features.
Relevant areas of configuration include:
- External access
- Guest access
More details about the external and guest access configurations further below in this post. However, it can be important to understand the difference between Guest access and External access. Here's the short rundown:
Guest access: Use this for example when you want external users to have access to teams and channels. Guest users can be added to a team and can chat, call meet, and collaborate on files. A guest user have close to the same access as a normal team member. Therefore, understanding this access level is important, since they can collaborate, and access your Office 365 / SharePoint / OneDrive for Business files.
External access: Users in other domains can find, call, chat and meet with your users. These users have no native access to your teams and resources. By default, this is enabled in Teams and your organization can communicate with any other organization, unless the Teams admins opt-out of using external access.
Read more:
- Manage Microsoft Teams settings for your organization (Microsoft Docs)
- Compare external and guest access (Microsoft Docs)
Designing and implementing External Access
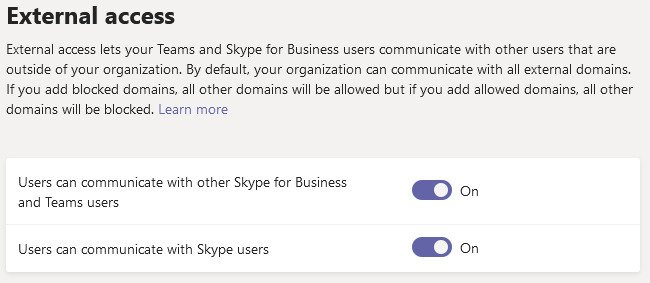
By default, external access is enabled in a Teams deployment. Administrators can opt-out of this, of course. Understanding how to properly configure External access is important, as well as understanding how it differs from Guest access. See the previous headline about the differences, and the link to a comparison guide.
When managing external access, you can, for example:
- Allow or block domains
- Configure whether you can communicate with Skype, or Skype for Business users, and more.
For some organizations, it makes sense to disable external access by default, and only grant access as required on a case-by-case basis. I like that approach, because it aligns a lot with Zero Trust and keeping things sealed from start, and opening the doors where and when it's needed.
Read more:
- Manage external access in Microsoft Teams (Microsoft Docs)
Designing and implementing Guest Access
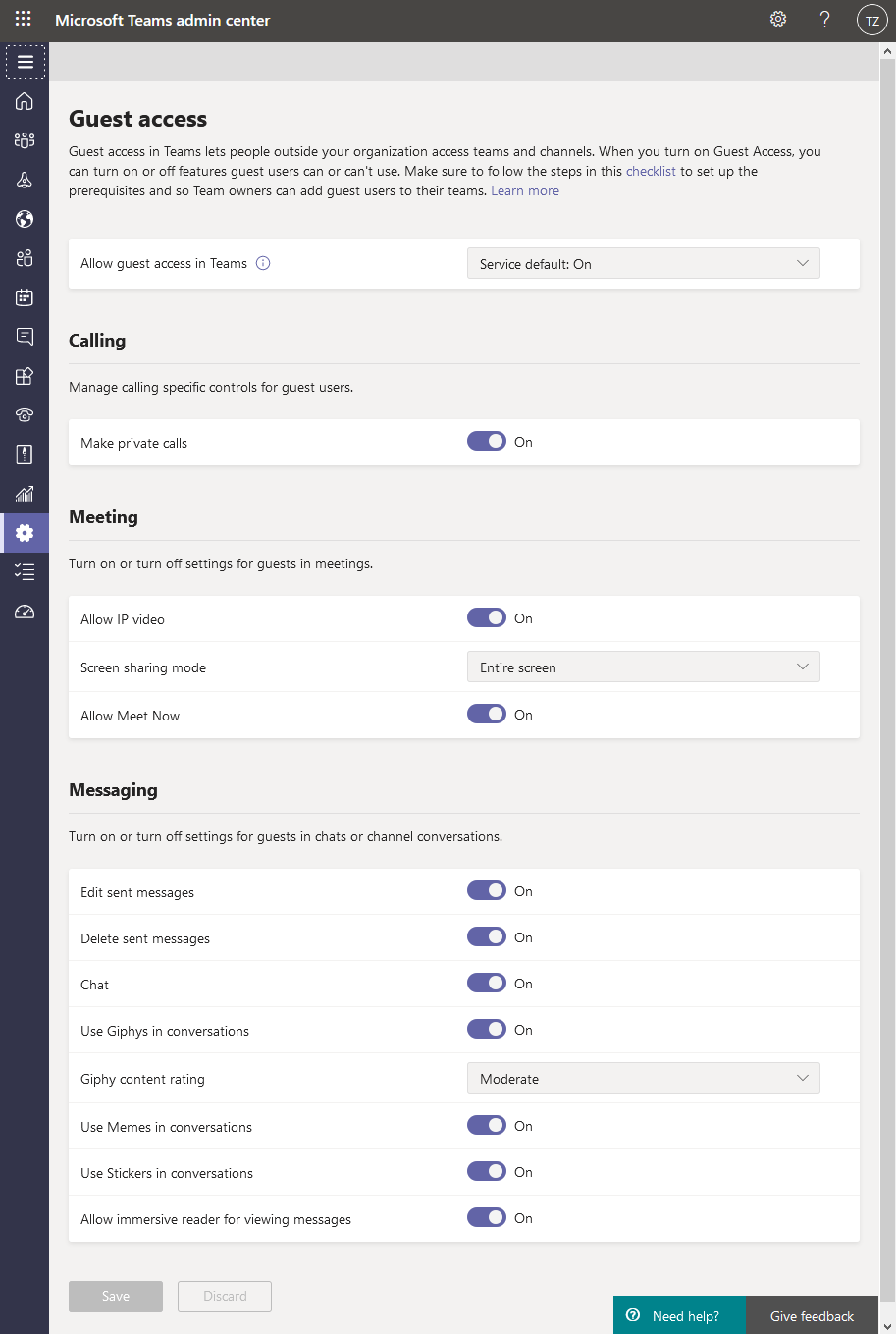
Guest users get similar access as normal users of the team, and therefore it's important to understand how it differs from external users. See the comparison link under the "Org-wide teams settings" headline in this post, just a few lines up.
Note! After February 2021, Guest access will be enabled by default for new customers, and for any existing customer who haven't configured this setting.
Read more:
- Guest access in Microsoft Teams (Microsoft Docs)
- Turn on or off guest access to Microsoft Teams (Microsoft Docs)
Designate roles for Teams meetings
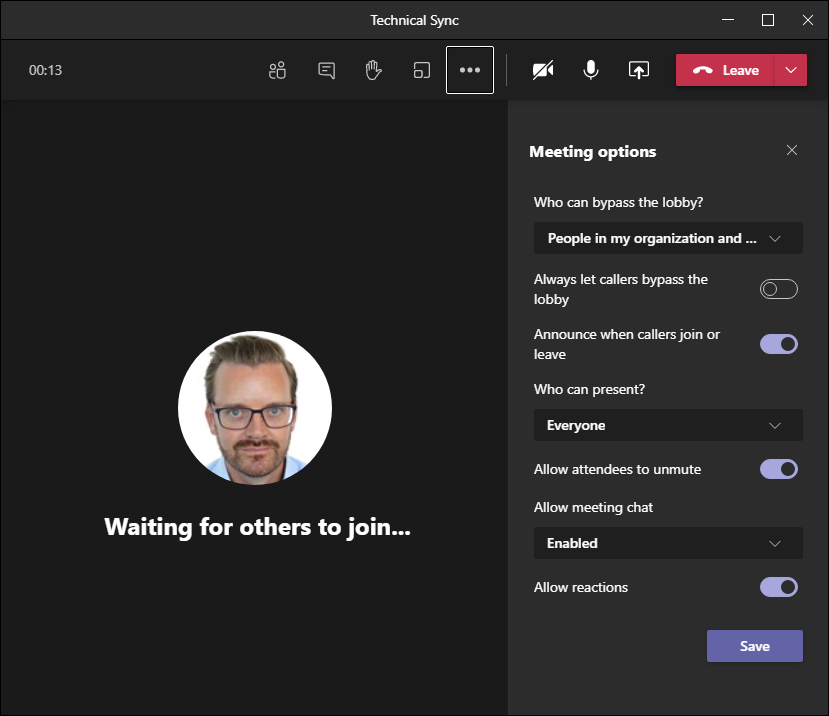
Learn about the roles you can designate the attendees in meetings. Knowing how to do this with precision can greatly help you achieve a more reliable and secure meeting experience at large.
- Organizer
- Presenters
- Attendee
Check out the below links to understand what role can do what things, and what things you can set up as policies as well as before and during meetings.
- Roles in Teams meetings (Microsoft Support)
Understanding and configuring Cloud Recording
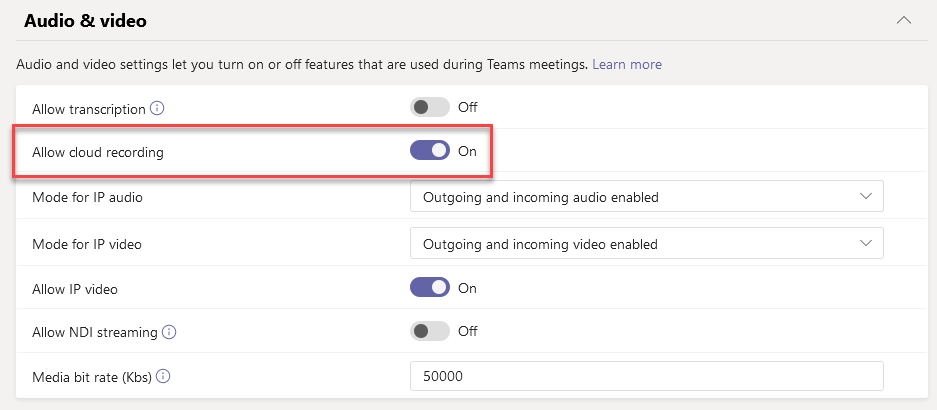
Recording meetings is a great capability. When we know where, and how the videos and data are stored. Understanding compliance and getting users to consent to recording and storing videos are, however, critical to the success of cloud recordings.
- Where are my meeting recordings located (data sovereignty)?
Recordings are stored in Microsoft Stream.(Classic)- Recordings are stored in OneDrive for Business and SharePoint.
- Read the below link for compliance and eDiscovery info.
Cloud Recording will move from Stream to OneDrive and SharePoint
As per the updated timeline in the docs; Use OneDrive for Business and SharePoint or Stream for meeting recordings, cloud recordings will be persisted to OneDrive for Business and SharePoint.
See the above link for more details about when the roll-out will be ready for your type of tenant.
Read more:
- Teams cloud meeting recordings (Microsoft Docs)
Make use of Information Barriers
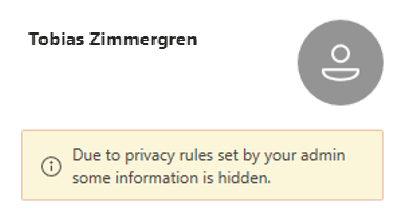
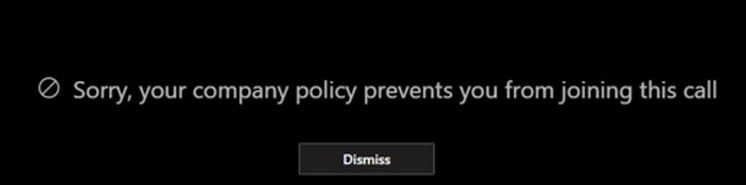
IB's, or Information Barriers, are policies we can make use of to prevent users or groups from communicating with each other. This can be both useful and important to understand, as it can quickly help us maintain the information governance in our organizations.
Use them, for example, to:
- Prevent Team A from communicating with Team B.
- Ensure that Team C can not communicate with anyone outside of the team.
Information Barriers are triggered when certain Teams event take place, for example:
- Members are added to a team
- A new chat is requested
- A user is invited to join a meeting
- A screen is shared between two or more users
- A user places a phone call (VOIP) in Teams
- Guest users in Teams
Read more:
- Information Barriers in Microsoft Teams (Microsoft Docs)
2. Compliance
In this section I want to highlight configuration aspects that relate to organizational compliance. Configurations in this area are related to compliance, and doesn't necessarily have to impact the collaboration experience of your users.
Configure Communication Compliance
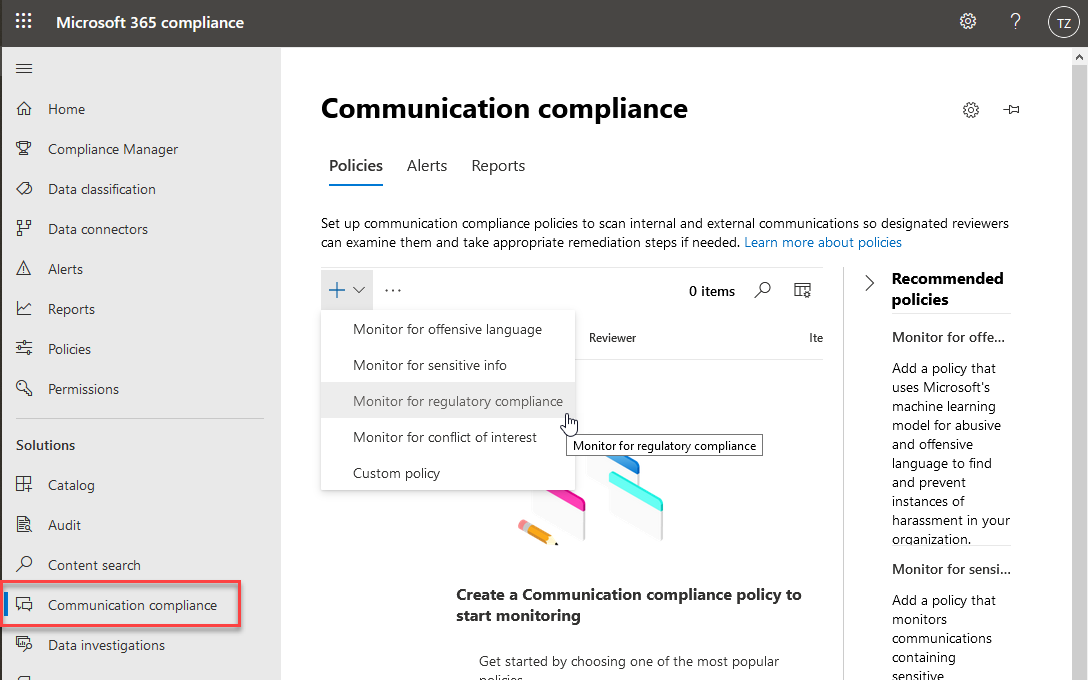
Using the Microsoft 365 Compliance Center we can control communication compliance for Microsoft Teams.
Please note. Before you can configure any Communication Compliance policies, you need to assign the appropriate permissions to your account. Even as a Global Admin, you do not have permissions in this area until you have configured these permissions.
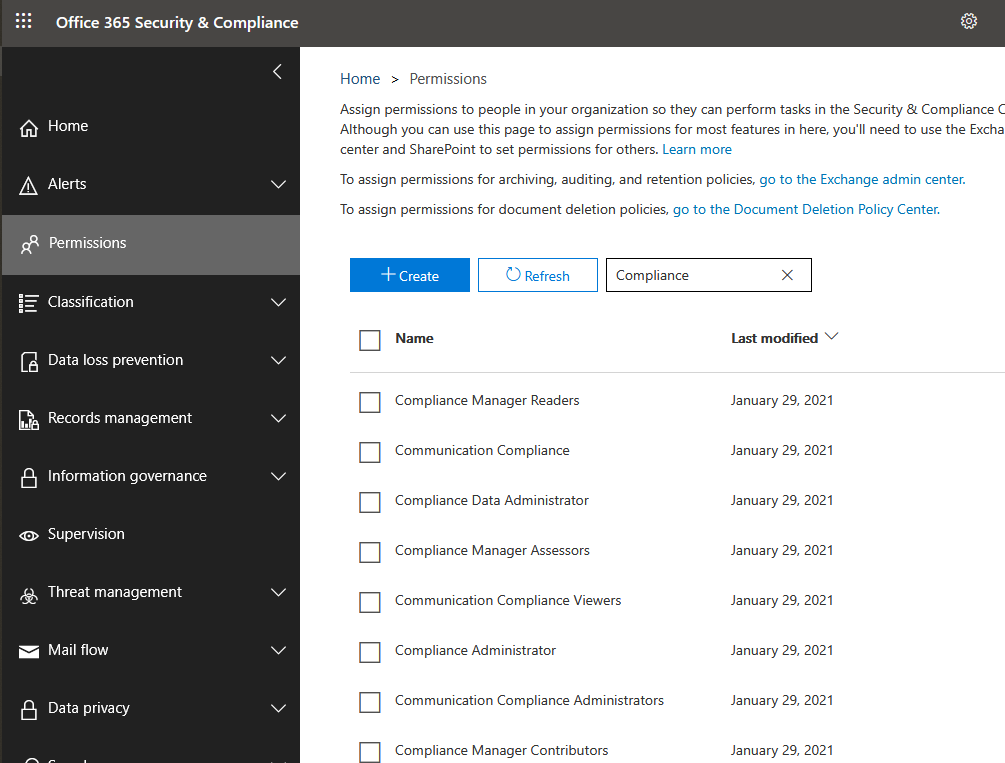
- How to: Enable permissions for Communication Compliance (Microsoft Docs)
Communication compliance is a powerful way to address compliance concerns in your organization's Teams and communication platforms.
- Intelligent customizable templates.
Apply Machine Learning to detect communication violations in your organization. - Flexible remediation workflows.
Quickly identify and take action on messages with policy matches. Remediation is made a lot easier with the new features being rolled out in this area. - Actionable insights.
Interactive dashboards for your alerts, policy matches, actions, and trends.
This is definitely an area to keep your eyes on if you are concerned about regulatory compliance and communication compliance at large. With the tools available today in the Compliance Manager, we get a lot of auditing, control, and insights in how we can learn and improve.
Read more:
- Learn about Communication Compliance in Microsoft 365 (Microsoft Docs)
Configure data retention
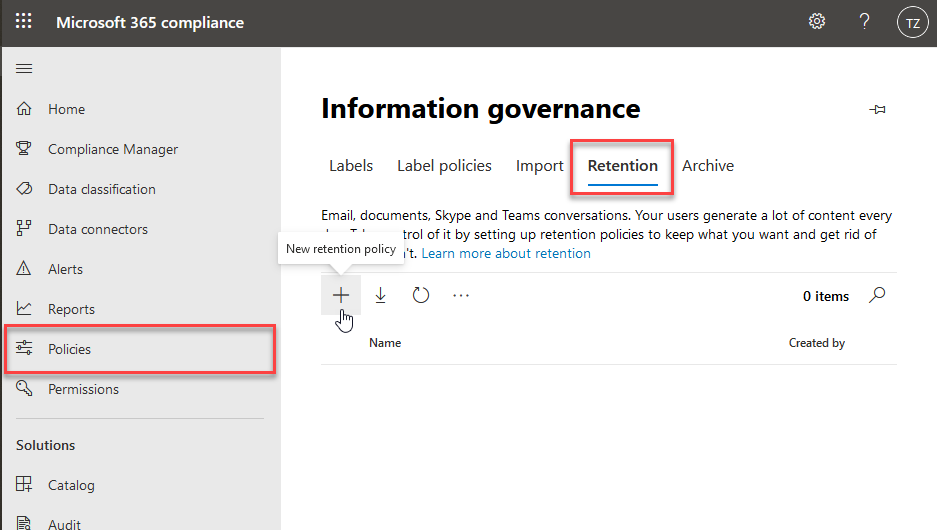
An important part of information governance that can often be forgotten is data retention. With this feature, you can more effectively manage the information you have in your organization .
Make use of retention policies to help comply with your corporate policies, industry regulations, legal needs, or any other aspect that requires you to keep data for specific periods of time. The opposite is also a possibility; ensuring that data is deleted if it's considered a liability, doesn't have any business or legal value, and you no longer need to keep it
Teams support data retention policies for:
- Teams Chat Messages
- Teams Channel Messages
Apply Teams data retention policies to your entire organization, or to specific users and teams.
Unfortunately, retention labels is currently not supported by Teams.
Designing good retention policies usually requires extensive research and work with many teams across an organization, or multiple organizations. There's some good insights in the Microsoft Docs to get started, but work is up to you!
Read more:
- Retention policies in Microsoft Teams (Microsoft Docs)
Understand data location and sovereignty
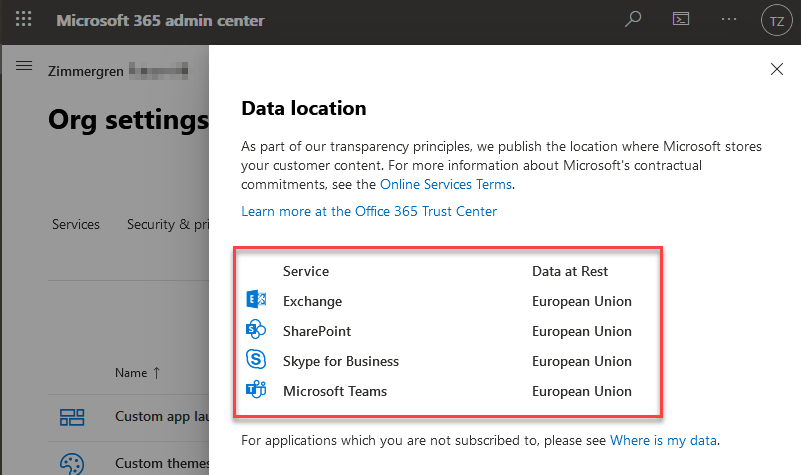
In order to understand and comply with data laws in your countries and organizations, it's important to understand where to store the data. You can easily see where your data is located in Microsoft Teams by navigating to the Microsoft 365 Admin Center -> Settings -> Organization Profile -> See "Data location"
Read more:
- Location of data in Microsoft Teams (Microsoft Docs)
Microsoft Teams Multi-Geo Support
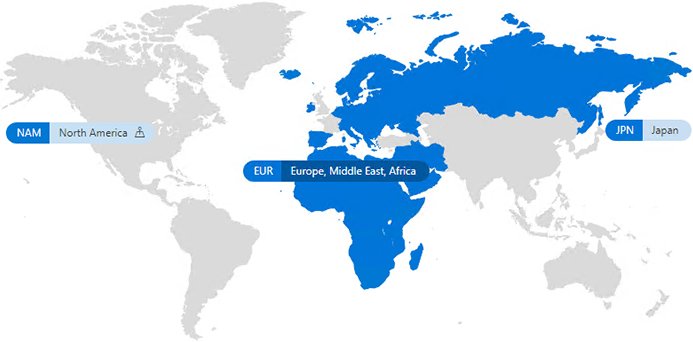
At Ignite 2021, Microsoft announced that they're rolling out support for Multi-Geo capabilities. With the Microsoft 365 multi-geo support, you can control where data is located, and specify data centers for the persistance of information.
Decide where you want to store your data at rest, which ultimately helps you achieve your data compliance and security regulations.
Read more:
- Teams experience in a Microsoft 365 Multi-Geo enabled tenancy (Microsoft Docs)
eDiscovery in Microsoft 365
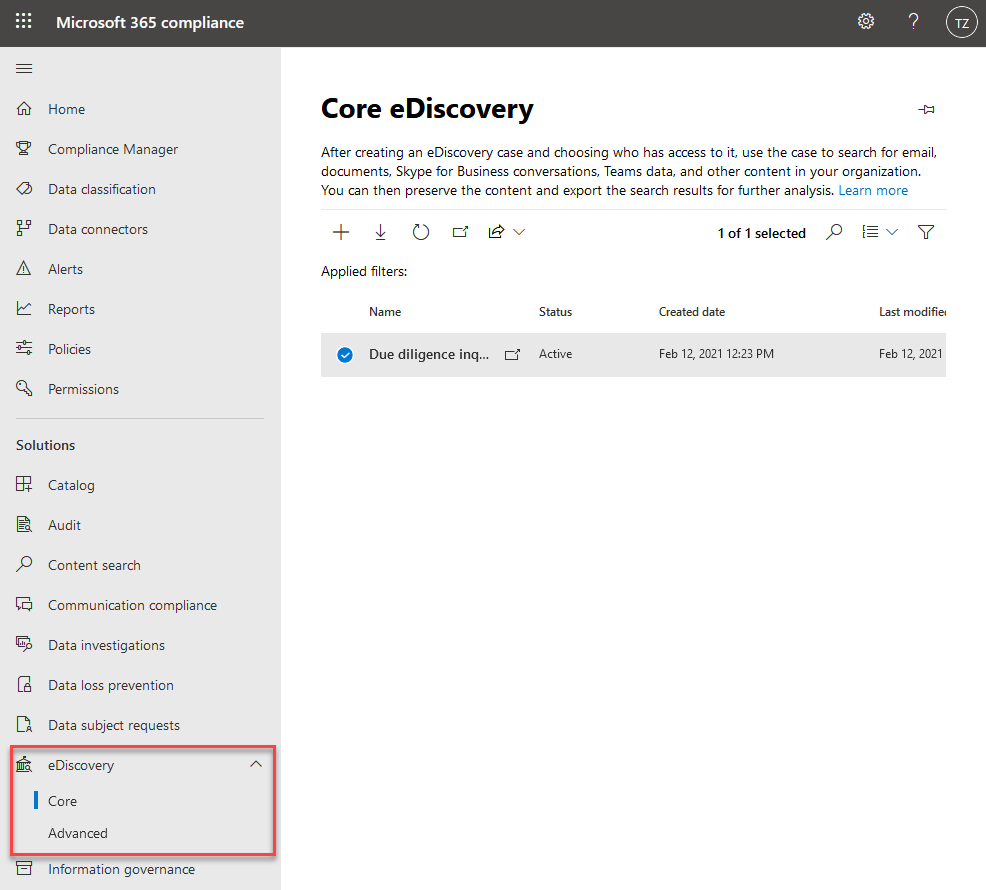
With Electronic Discovery, or eDiscovery, we get powerfull tools to help identifying information that we can use as evidence in legal cases, due diligence processes, and more.
Enable the eDiscovery tools for Microsoft 365 to search for content in various areas, including:
- Exchange Online mailboxes.
- Microsoft 365 Groups
- Microsoft Teams
- SharePoint Online
- OneDrive for Business
- Skype for Business conversations
- Yammer teams
There are three main tools for eDiscovery:
- Content search.
- Core eDiscovery.
- Advanced eDiscovery.
Creating holds, searching for content, exporting data, or any other related actions are fairly straight forward in the UI - but it usually requires a lot of effort in understanding what we need to discover, and how to identify it.
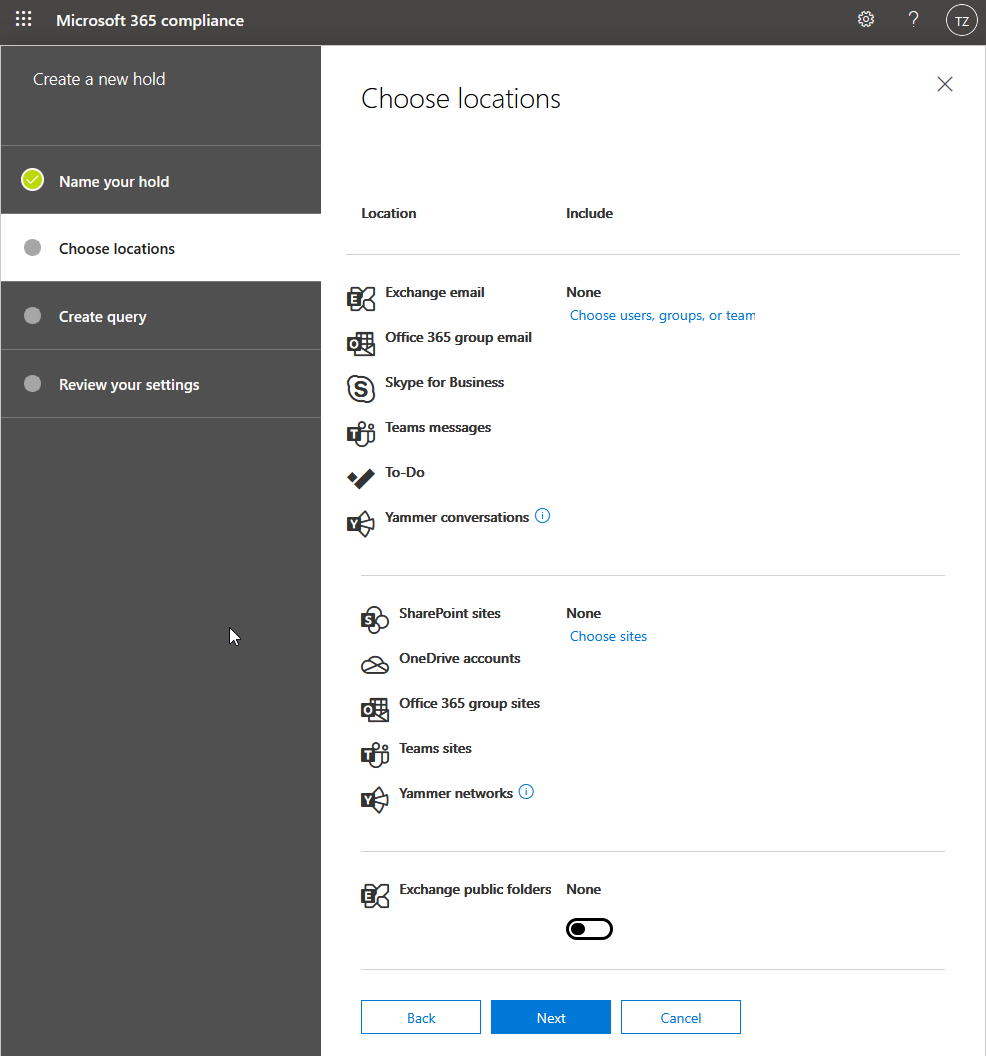
To learn how eDiscovery works, refer to the following overview and drill down from there:
- eDiscovery solutions in Microsoft 365 (Microsoft Docs)
Auditing user activity
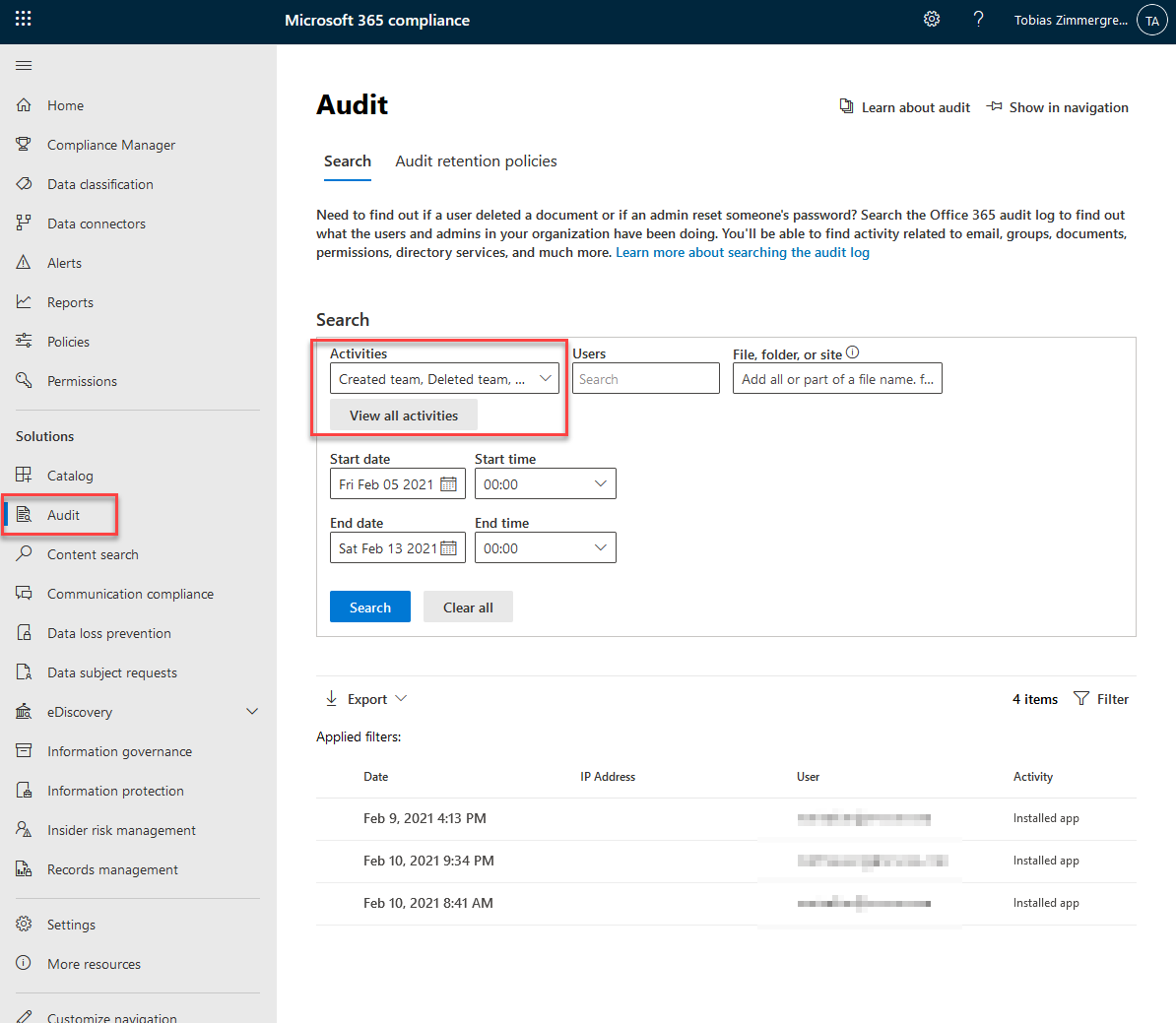
By default in Microsoft 365 and Office 365 enterprise organizations, audit logging is enabled. You should of course verify and ensure that you have audit logs turned on for your tenants (see link further down).
Previously, the audit log search happened from the protection.microsoft.com portal, but has an upgraded experience in the Microsoft 365 Compliance portal (https://compliance.microsoft.com/auditlogsearch).
Relevant activities we can search for in the audit logs are plenty, and the list goes on:
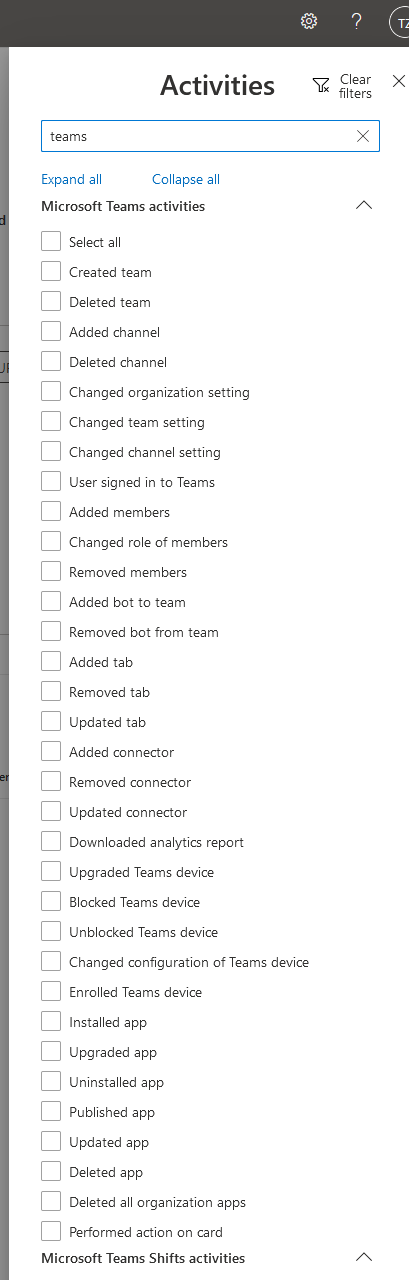
Read more:
- Turn on the audit log search (Microsoft Docs)
- See a full list of Teams activities here (Microsoft Docs)
3. Security
In this section I'm looking at security-specific configurations, to sail a tighter ship. Settings here doesn't necessarily have to impact the collaboration experience of your users.
Review the Security Guide for Microsoft Teams
Microsoft is doing a great job in providing updated information about their security posture, how they develop securely using the Microsoft Security Development Lifecycle (SLD), and more.
The resources provided in the links below are crucial to understand how Microsoft deals with and designs for security, which can help you make more informed and trusted decisions down the road.
I find myself coming back to this document often when I need to understand how particulars work, or for example reviewing the information about FIPS. Generally a great document to understand a lot about security, trust, and threats. Well done Microsoft 👏
Read more:
- Security framework for Microsoft Teams (Microsoft Docs)
Enforce Multi-factor Authentication (MFA or 2FA)
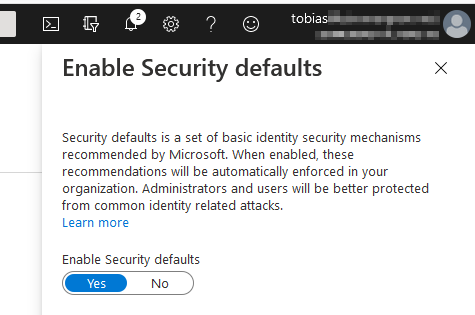
This is one of the most important tips in this article. Do not neglect MFA. According to official docs from Microsoft, enabling MFA (or 2FA) ensures your accounts are up to 99.9% less likely to be compromised.
I like to roll out MFA as part of Conditional Access policies, requiring multi-factor authentication for any sign-in to our tenants. Always. This way, I can also easily control from where (locations, IP, etc) users connect and authenticate, and I can require additional attributes to be true for administrators signing in.
Block legacy auth protocols, roll out conditional access, and ensure you have an org-wide requirement for MFA.
If you don't have Conditional Access, make sure you have enabled the Security Defaults, which also comes with MFA requirements.
Read more:
- Azure AD Multi-Factor Authentication (Microsoft Docs)
- Conditional Access: Require MFA for all users (Microsoft Docs)
Understand Conditional Access for Microsoft Teams
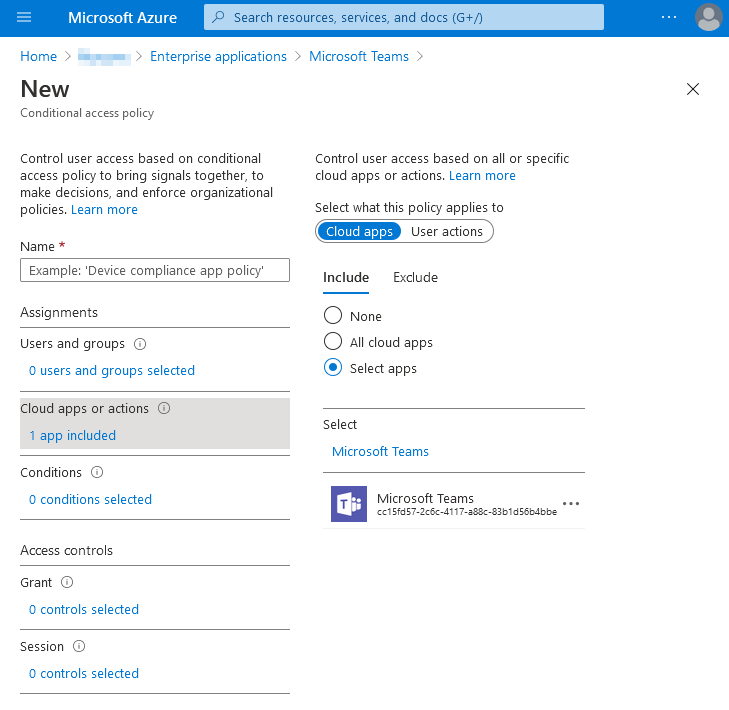
Enabling Conditional Access for the Microsoft Teams app in Azure Active Directory is a powerful way to control how your users can access the app.
Please be aware of this: Since some of the data in Teams come from SharePoint and Exchange Online, users can potentially still access resources in these areas even if you have Conditional Access policies for your Teams App. When you roll out Conditional Access for Teams, it makes sense to evaluate how you should roll this out for Exchange and SharePoint, too.
Read more:
- How conditional access policies work for Teams (Microsoft Docs)
- Enforce Conditional Access from the Microsoft Endpoint Manager (Microsoft Docs)
- Require multi-factor authentication and set up Conditional Access (Microsoft Docs)
Set up Data Loss Prevention (DLP)
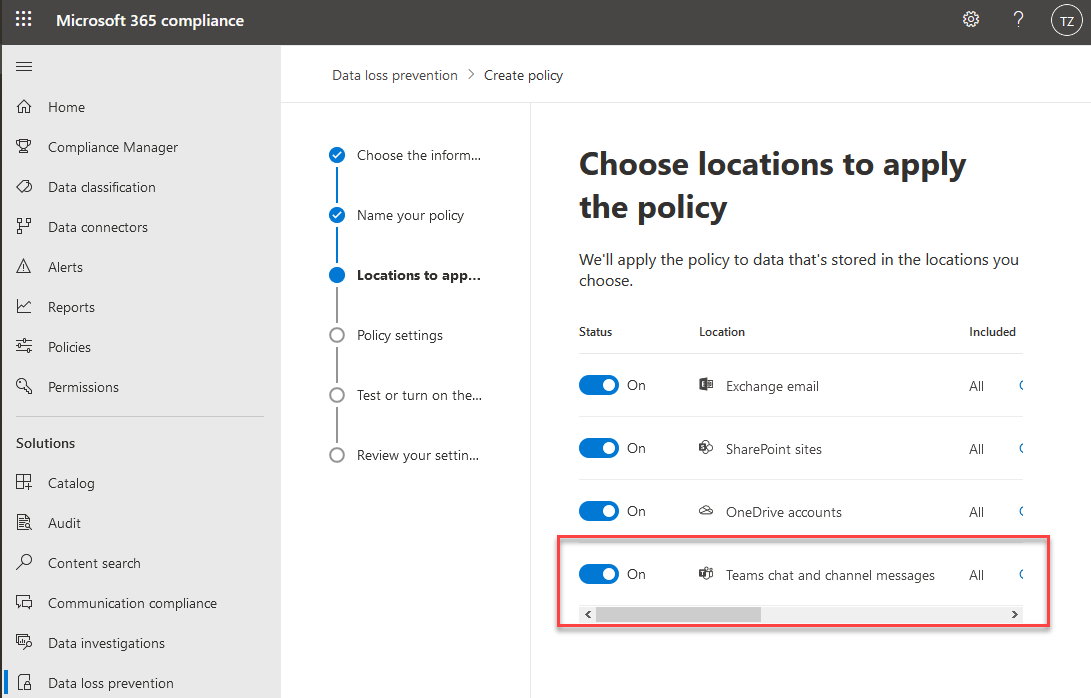
Making use of DLP for Microsoft Teams chat and channel messages is another way to protect data in your organization. With DLP you can define policies that prevent users to share sensitive information.
My short take on DLP for Teams is: Make sure your users don't share sensitive information in chat/channels, email or documents with the wrong people. DLP for Teams can, for example, prevent sensitive information from being shared in these areas.
- Teams Channel Messages
- Teams Chat messages
- Teams Private Channel Messages
Make sure to understand this:
DLP for Teams is only supported when the user has a mailbox that is in Exchange Online.
- Data Loss Prevention and Microsoft Teams (Microsoft Docs)
Use Advanced Threat Protection (ATP)
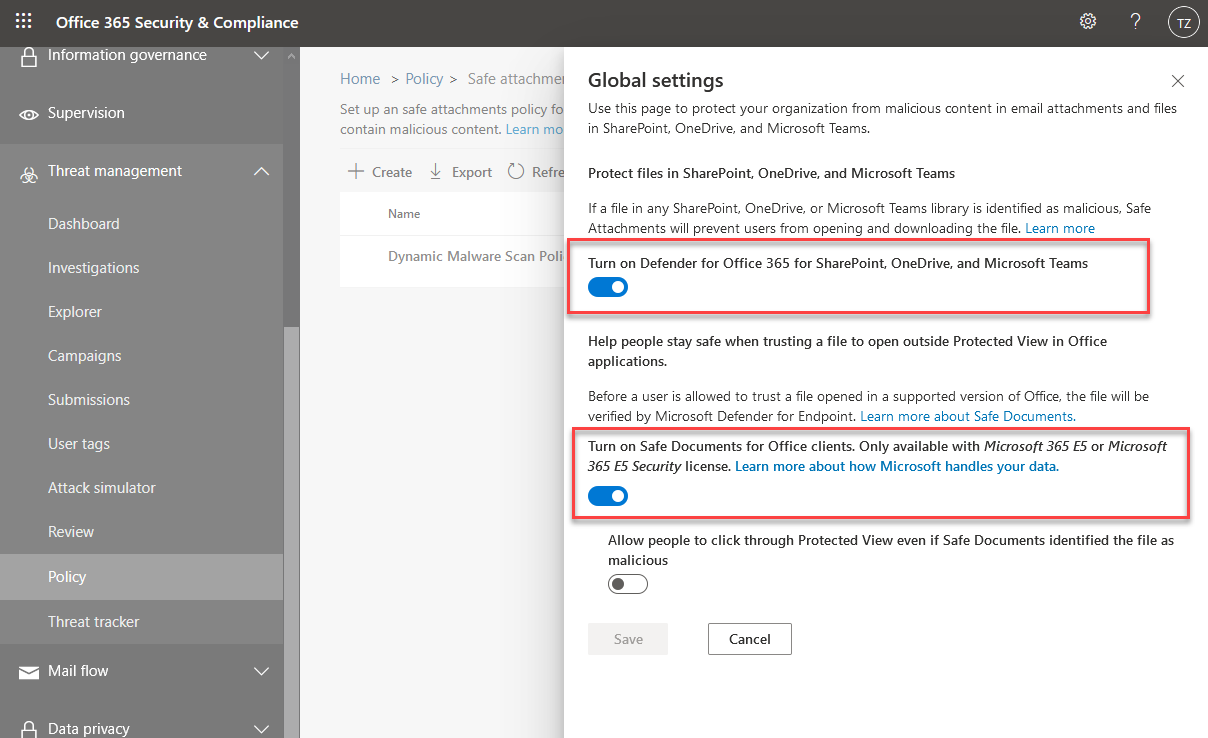
With Advanced Threat Protection, ATP, we get added layers of protection. Safe Attachments for SharePoint, OneDrive, and Microsoft Teams help us block files that are identified as malicious files.
Enabling Defender for Office 365, and enabling Safe Documents is fairly straight forward. Go to your Office 365 Security & Compliance portal -> Threat Management -> Policy -> Global Settings.
I don't see a valid reason why this wouldn't be enabled in any organization.
- Microsoft Defender for Office 365 (Microsoft Docs)
- ATP for SharePoint, OneDrive and Microsoft Teams (Microsoft Docs)
- Security in Microsoft Teams (Microsoft Docs)
Safe Links for Microsoft Teams
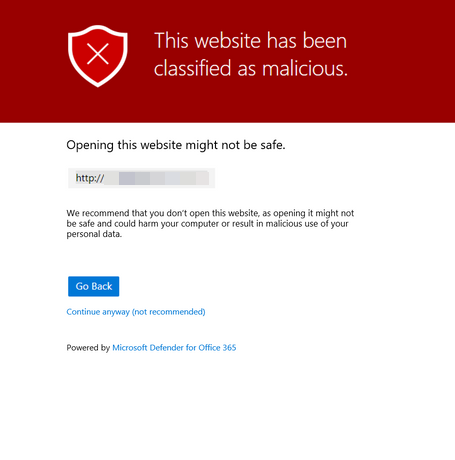
During the Ignite 2021 conference, Microsoft announced the preview roll-out of Safe Links for Microsoft Teams.
With Safe Links for Microsoft Teams, you can configure what happens with links classified as unknown or potentially malicious.
Read more:
- Safe Links settings for Microsoft Teams (Microsoft Docs)
Use and review Cloud App Security
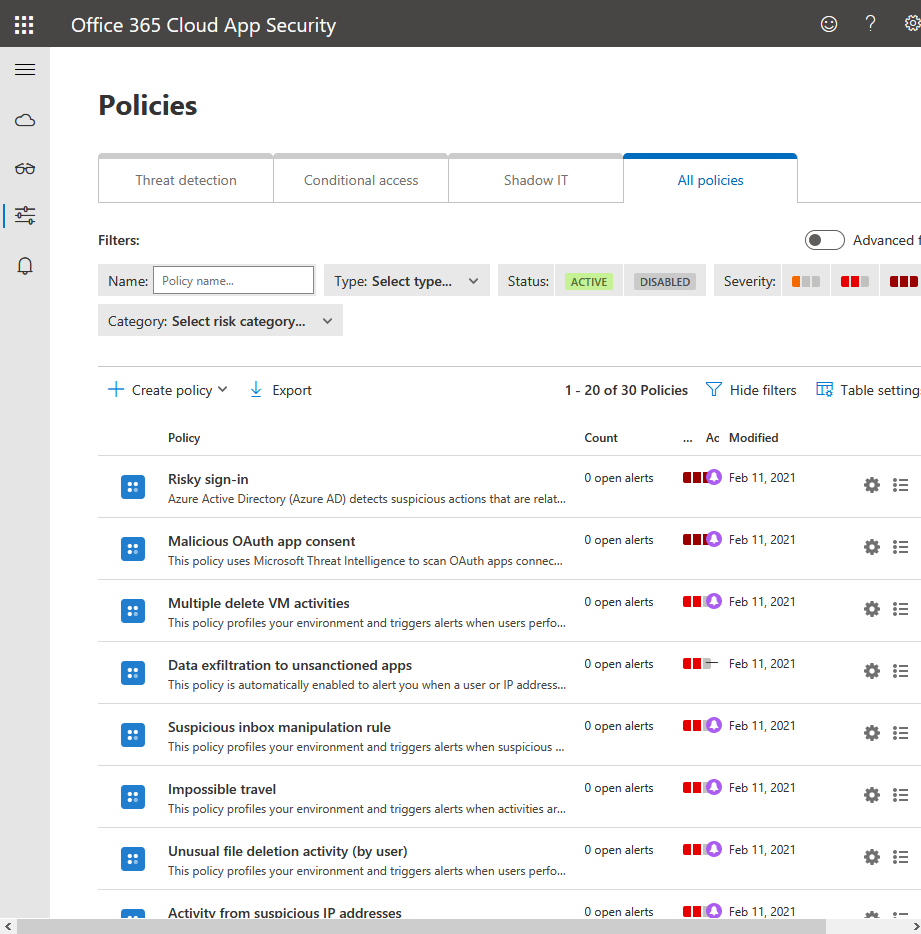
Using Microsoft Cloud App Security is another great way to do risk assessment for apps in your Microsoft 365 environments. You can use Cloud App Security to discover apps, and proactively identify risky, non-compliant, and trending apps.
Some recommendations:
- Configure App Discovery. Find trending, non-compliant, or risky apps.
- Monitor OAuth consents from users. You can manage OAuth apps that are authorized by users in the organization, enabling you to stay informed about what permissions have been granted to various apps, including by admins.
- Make use fof Defender for Endpoints to discover Shadow IT. With Cloud Discovery, we get visibility and continuous monitoring for unsanctioned apps and cloud use.
- Tag apps! You can tag various apps with Sanctioned or Unsanctioned, indicating whether they are allowed to be used or not.
- Use File policies. You can create data exposure policies, to see what files shared externally that contains sensitive data, has been labeled as Confidential, or has been shared with unauthorized domains, and more.
- Protect confidential data. With a file policy, we can protect data classified as "Confidential", ensuring that it's not being shared with external users. Ultimately, this helps us ensure that the confidential data doesn't leave our organization.
- Monitor sessions with external users. Using Conditional Access App Control, we can monitor sessions for external users. We do this with a session policy, and we can monitor the sessions between internal and external users - we get the insights, can notify users that their sessions are being monitored, and we can limit specific activities.
- Detect unusual location activity. The same way we can get ATP to provide us with insights into unusual location activity, we can detect activity from unexpected locations or countries in Teams. We can do this by using an Activity policy, and you can get notified when users sign in from unexpected locations - this can help us understand if there are compromised sessions, so you can remediate.
There's a lot more to wade through with Cloud App Security, and it would warrant both a few consulting sessions and additional documentations and organizational research and review to fully make use of. I hope that this at least can give a sense of the capabilities, and the links below should get you started.
Read more:
- Protect apps with Microsoft Cloud App Security (Microsoft Docs)
- What is Cloud App Security (Microsoft Docs)
Prevent users from installing trial apps and services
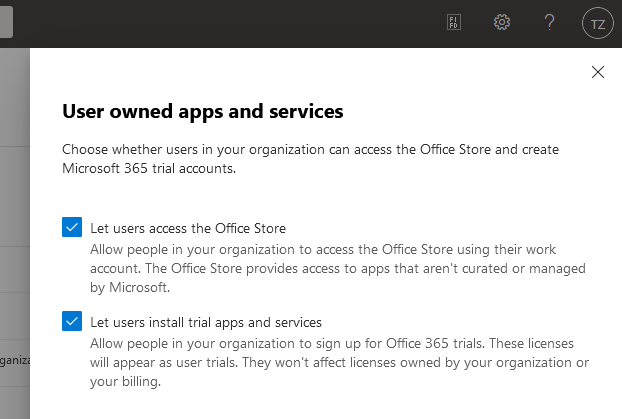
If you see app proliferation, or users not using apps the way your organization intended, there's a way to prevent users from installing trial apps and services. This prevents them from running what we know as the Teams exploratory experience.
You can:
- Disable user's access to the Office Store
- Disable user's access to install trial apps and services
Read more:
- Prevent users from installing trial apps and services (Microsoft Docs)
Summary
Whew. This took a long time to write and summarize, and a lot of effort went into portraying what I believe are the most important aspects to consider to securing your Microsoft Teams experience and information.
If you think there's something missing, please leave a comment here or directly to me. If you find outdated information, as time goes on, please also reach out and inform me and I will try to keep this information up to date.
Thanks for reading. Stay safe and healthy.
Tobias.








Recent comments