Cybersecurity
Content that touches on Cybersecurity, cloud security, security for executives, and more.

Thoughts on Bring Your Own Key, or BYOK, to Azure Container Registry Paid Members Public
In this article, I am exploring the capabilities of Bring Your Own Key with the Azure Container Registry. A way for you to get better control of the full Key Lifecycle Management process, should you need to. I am detailing a few of my thoughts that come up around different

Cybersecurity tips for Remote Workers - Get online, stay informed, stay secure! Paid Members Public
Here's a list of simple and efficient tips to stay more secure when Working From Home. Cybersecurity tips for Remote Workers that anyone can benefit from!
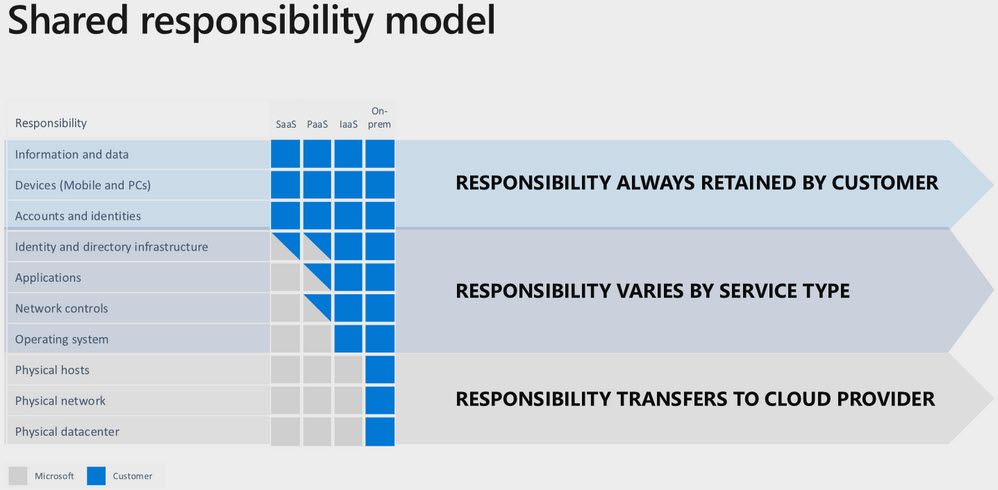
Embrace a Secure Software Development Lifecycle (SDLC) for Azure Paid Members Public
While threats are ever-increasing, so are the capabilities, methodologies, and technologies we have at our disposal to mitigate risks at a higher cadence than ever before. In this article, I'll talk about the responsibility we have as developers, solution architects, DevOps engineers, and anyone else involved in your





Recent comments