
A few tips for securing your remote workforce in a Microsoft cloud landscape
Are you a CIO, CISO, or are you at any level responsible for security in your organization? Are you just getting started with Azure and the cloud, and having a remote workforce - or are you seasoned in the cloud, but your users are not? Here's a couple of tips from the field that I hope can help.
Work From Home, or #WFH, is a thing today. I have been successfully working remotely for more than seven years, and I have enjoyed every minute of it - but it isn't without challenges.
I get questions regularly now, both from family and friends, and from colleagues in the broader business landscape, and readers (and listeners). The typical pattern I have identified is that many organizations are already embracing Azure AD. However, they haven't considered what would happen when their entire workforce stays at home and still needs to connect to all resources you have in-house.
In this article, I'll brief on the topics I find most important for a remote workforce when it comes to securing your organization's assets and accounts.
Require Multi-Factor Authentication (MFA). Period.
In 2019, Microsoft wrote the following statement:
One simple action you can take to prevent 99.9% of attacks on your accounts.
They were talking about MFA. Let that sink in. 99.9% of attacks on user accounts are blocked simply by enabling MFA.
The most common vulnerabilities include, according to SANS SSI:
- Password re-use, where compromised passwords are used to target other systems where someone is using the same password.
- Legacy protocols still being allowed, and they don't support MFA.
- Business e-mails are compromised, which is a lot easier without MFA.
There's no excuse not to enforce this for all users in the organization. Working remotely makes this use case an even hotter topic.
If you're in the Microsoft landscape and you're employing Azure AD, for example, enforcing stringent policies with Conditional Access is a must with a remote workforce.
Read more:
- How it works: Azure Multi-Factor Authentication (Microsoft.com)
Make use of Conditional Access
With Azure AD, Conditional Access plays an imperative role in the security landscape.
Examples of common policies with Conditional Access include:
- Block all legacy authentication
- Require MFA for Admins, Azure Management tasks, and for all users
- Risk-based Conditional Access
- Require a trusted sign-in location
- Block access by location
- Require compliant (approved) device
- Block all access except for specific apps
- And more.
Read more:
- Azure AD Conditional Access Documentation (Microsoft.com)
Advanced Threat Protection for Office 365 helps!
You upload files to SharePoint Online, OneDrive, and Microsoft Teams. You have incoming e-mails in Exchange Online. There are a plethora of angles where threats are targeted every day, mostly without us ever seeing them because the systems are smarter than the threats—most of the time.
Using Office 365 Advanced Threat Protection, you can help stay safer as an organization, enabling your users to keep their flexibility in how they work. At the same time, you can maintain and enforce the malware checks you need.
Read more:
- Office 365 Advanced Threat Protection Documentation (Microsoft.com)
- Office 365 Advanced Threat Protection service description (Microsoft.com)
- Office 365 ATP for SharePoint, OneDrive and Microsoft Teams (Microsoft.com)
Bringing on-premises and cloud together, more securely
If your organization is usually working on-premises with a lot of security and networking already in place, there's a couple of capabilities in Azure that might be interesting to review. If you are now moving to or accelerating your cloud growth, it helps to look at the hybrid capabilities.
- Bring Conditional Access, Multi-factor Authentication, Identity Protection, and more to your legacy apps.
- Enable SSO and Passwordless authentication for your legacy apps.
- Centralize access management for both cloud and legacy apps.
- Enable secure remote access to on-premises web apps with Azure AD Application Proxy.
Read more:
- Azure AD Application Proxy (Microsoft.com)
- Azure AD Secure Hybrid Access (Microsoft.com)
Embrace Zero-Trust, and assume breach. Take the assessment!
In a previous article, I wrote about Security Development Lifecycle (SDL); I mentioned Zero-Trust.
Just this week, Microsoft announced that you could Take the Zero Trust Assessment and see where you are in your journey.
It's a quiz, if you will, and asks you questions about your current security and infrastructure:
You'll get a set of results. I ticked a few boxes randomly to get to the conclusion to grab a screenshot. You'll get some pointers that can help you quickly mitigate risks:
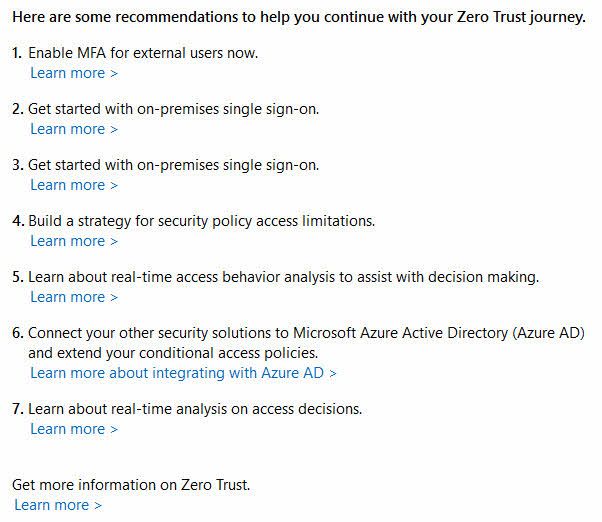
Read more:
- Zero Trust Framework to enable remote work (Microsoft.com)
Make use of Microsoft Intune to restrict device access
Microsoft intune helps you Protect devices, which is something I wouldn't take lightly on. What good does a firewall or corporate policy do on laptops, if the users are also using their mobile device to access all of their sensitive data?
Do not just look at Office 365 / Microsoft 365 as a potential threat vector. See the capabilities to integrate data protection and compliance capabilities from Microsoft Intune with the mobile devices, to allow a more flexible but strict remote workforce efficiency.
- Restrict the use of Hardware features (Camera, Bluetooth, ..)
- Configure compliant and non-compliant apps, and get alerts if disallowed apps are installed, or block them.
- Remotely wipe any company data from a device.
- Require device compliancy; encryption, disallow jailbroken devices, and more.
I like the documentation about Mobile Threat Defense integration with Intune, which can help you understand the capabilities, and why they are essential to consider.
If the task is on your table to decide about device security, corporate data security and, security at large within your organization, don't hesitate to evaluate Microsoft Intune immediately. Users will have to approve Microsoft Intune to have specific capabilities on their devices, to allow a remote wipe of corporate data, for example. Simply put, if users do not like that, they shouldn't be using corporate data on their mobile devices, either.
We are, of course, not just limited to Microsoft Intune. The Microsoft Endpoint Manager includes a whole set of goodies:
- Microsoft Intune
- Configuration Manager
- Co-management
- Desktop Analytics
- Windows Autopilot
- Azure AD Premium
- Endpoint Manager Admin Center
Read more:
- Microsoft Endpoint Manager overview (Microsoft.com)
- What is Microsoft Intune (Microsoft.com)
Inform your workforce about potential risks
Not everyone is a seasoned Work From Home expert. Common threats that merge are also non-technical and targets the users of your organization. You don't want to overwhelm your users with information - imagine that there are thousands of employees now working remotely for the first time. There are many things they have to learn and adjust to, at the same time as they do their daily job. I believe a critical factor in succeeding in the long-term, is simplicity for the users. For you, it may mean a lot of evaluations, agile planning and actions, and executive decision making.
There are a great few lines published on Darkreading about this:
Ultimately, your goal is to make security simple for people. They are overwhelmed right now with a tremendous amount of change, chaos, and anxiety. Whatever we do, simplicity is the key. There are two key elements this. The first is enabling people, we do this by focusing on as few behavior as possible. The more processes, policies, and procedures you throw at people, the more likely they will be overwhelmed and fail. You need to work with your security team to identify the fewest risks that have the greatest impact, and the behaviors that manage those risks
The risks lined up are:
- Social Engineering
- Passwords
- Updating
Take simple measures to get things rolling in the right direction.
Read more: Securing Your Remote Workforce: A Coronavirus Guide for Businesses (Darkreading.com)
Summary and additional links
The challenges for someone in charge of the security, infrastructure, and company assets are many. Primarily if your company usually does not have many people remote.
Securing a remote workforce isn't a trivial task. However, with the capabilities in the Microsoft cloud landscape, it becomes easier to roll out the compliance policies you want across your organization.
Microsoft Azure AD is a vital part of this. If you are already using Azure AD, or a hybrid setup, you might want to evaluate the capabilities offered you to secure devices, accounts, and data.
There are plenty of more things we could cover in this post, but these things are the top-of-mind things you shouldn't neglect, in my experience.
If you have additional tips, I would be happy to include them, too. Leave a comment or tweet me about it.
Additional reading:
- COVID-19 Drives Rush to Remote Work. Is Your Security Team Ready? (Darkreading.com)
- Security Lessons We've Learned (So Far) from COVID-19 (Darkreading.com)
Header photo by Philipp Katzenberger on Unsplash








Recent comments