
Frameworks to strategically improve your cybersecurity
Learn about popular cybersecurity frameworks like NIST Cybersecurity Framework (CSF), CISAs Cross-Sector Cybersecurity Performance Goals (CPG), MITRE ATT&CK and D3FEND, Microsoft Cloud Adoption Framework's Secure methodology, and Microsoft's CISO Workshop Training.
Table of Contents
In the article about the top 10 cybersecurity misconfigurations the NSA and CISA found we learned about the potential impact of weak network and security configurations for organizations.
In this article, the altitude remains at the executives, IT leaders, and security leaders. The following section will tackle some thoughts on common frameworks you can start implementing and digesting to learn how you, as an organization, can strengthen your security posture all-up.
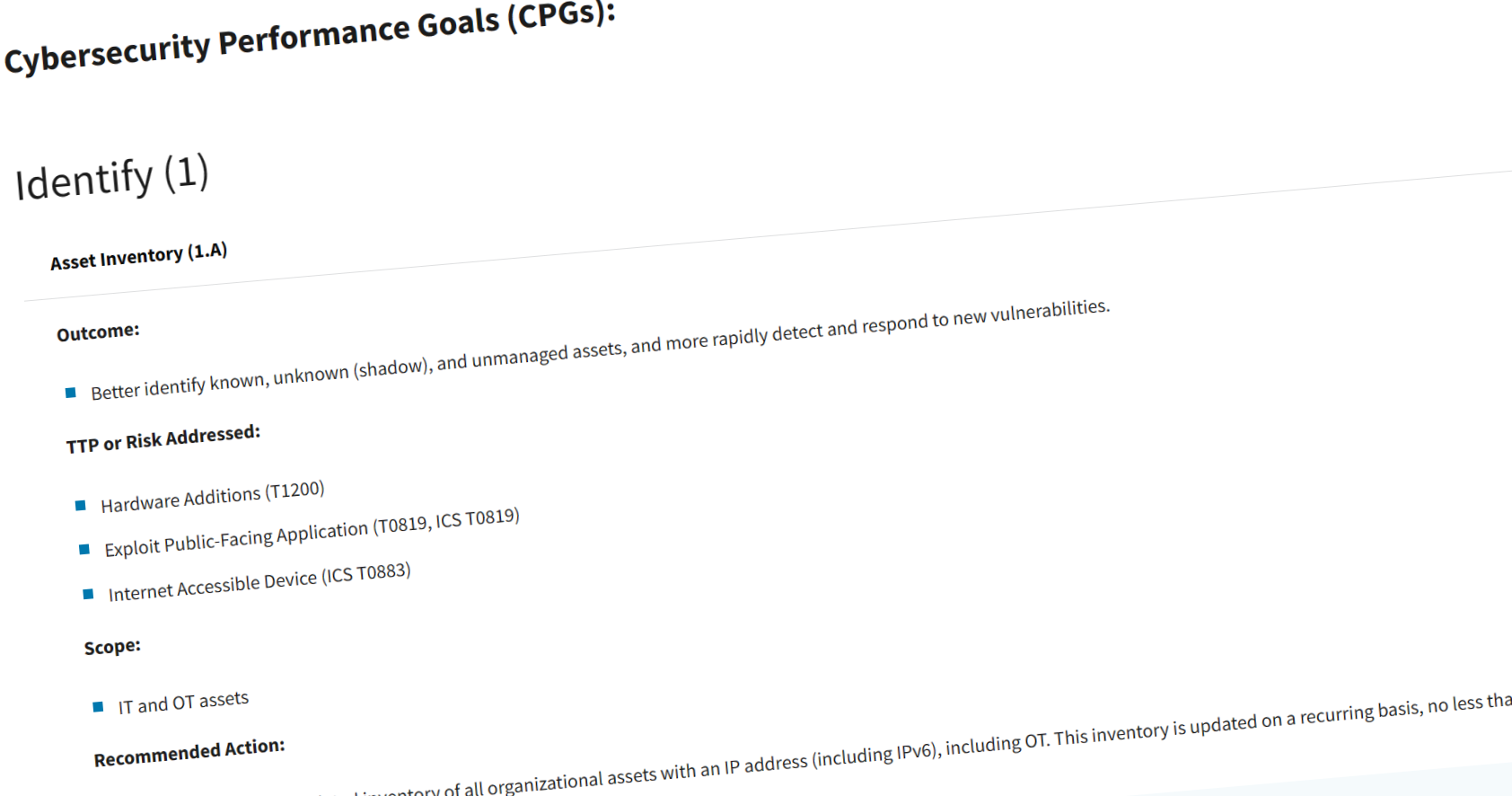
CISA - Cross-Sector Cybersecurity Performance Goals
A set of basic safety measures that all important service providers, big or small, should use to lower the chance and effect of known threats and harmful actions.
These guidelines align with the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF).
NIST Cybersecurity Framework (CSF)
The National Institute of Technology and Standards (NIST) has a popular Cybersecurity Framework (CSF). I've worked with parts of NIST and CSF and am excited for the CSF 2.0 release – see the roadmap below.
The framework is guidance, based on existing standards, guidelines, and practices for organizations to better manage and reduce cybersecurity risk. In addition to helping organizations manage and reduce risks, it was designed to foster risk and cybersecurity management communications amongst both internal and external organizational stakeholders

- See the NIST CSF (current version)
- See the NIST CSF 2.0 draft
MITRE ATT&CK and MITRE D3FEND
MITRE ATT&CK and MITRE D3FEND serve complementary but distinct roles in cybersecurity.
- ATT&CK provides a comprehensive knowledge base of adversary tactics and techniques observed in the wild, categorizing the different phases of cyber-attacks.
- D3FEND is focused on the defensive side, offering a structured framework for understanding and specifying cybersecurity countermeasures.
Here's how MITRE paints the picture of the offensive and defensive technique relationship:
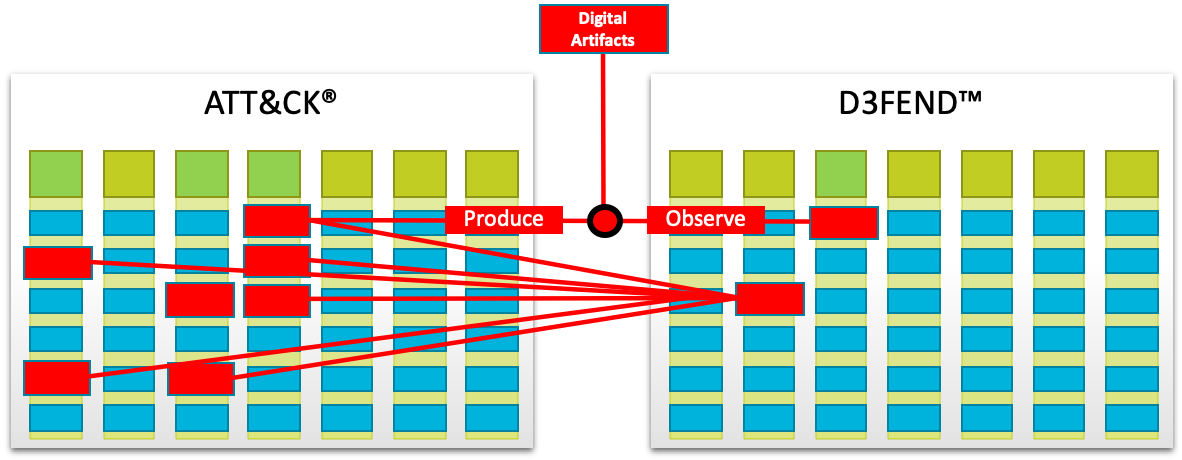
If we're talking about mitigations for enterprises, MITRE ATT&CK for Enterprise helps mitigate and prevent techniques or sub-techniques from being successfully executed.
Both the ATT&CK and D3FEND frameworks come with great overviews in their Matrixes, offering a quick look at the framework, and the important techniques to understand.
Dive into the frameworks here:
Security in the Microsoft Cloud Adoption Framework (CAF)
For decision-makers, IT leaders, security advocates, and platform owners, I highly recommend reviewing the Secure methodology in CAF.
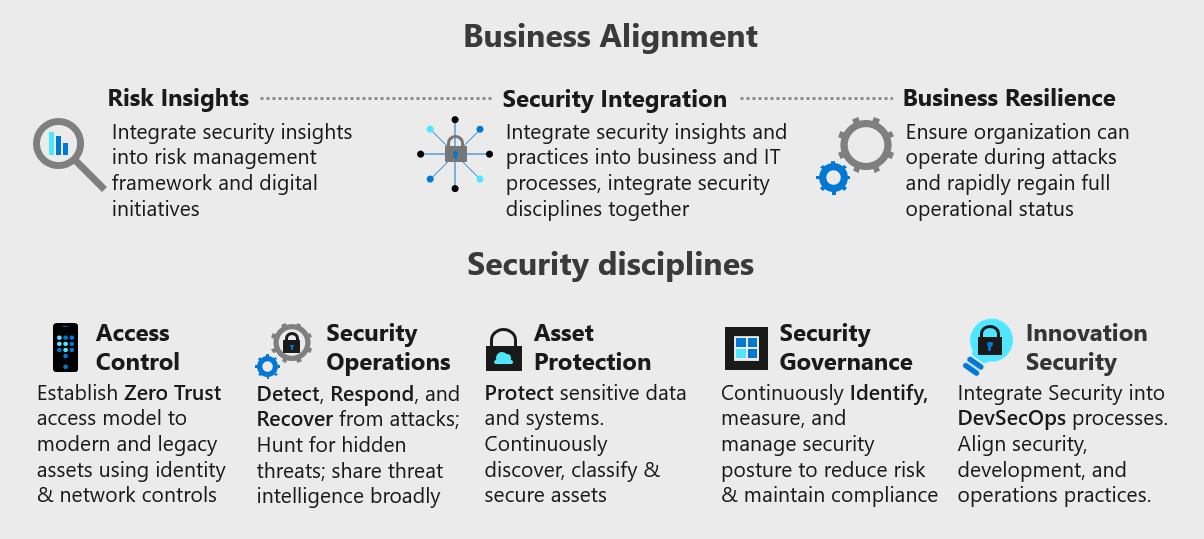
Security is, as we know, a continuous journey. With the Cloud Adoption Framework for Azure, the Secure methodology guides you through topics and processes you need to think about across your organization, including:
- Business alignment: Risk insights, security integration, and business resilience.
- Security disciplines: Access control, security operations, asset protection, security governance, and innovation security.
I recommend you visit the docs to learn more about strengthening your organizational security posture.
CISO Workshop Training
If you're a CISO, IT- or Security leader, enterprise- or security architect, the CISO workshop training is a great resource to foster a security culture.
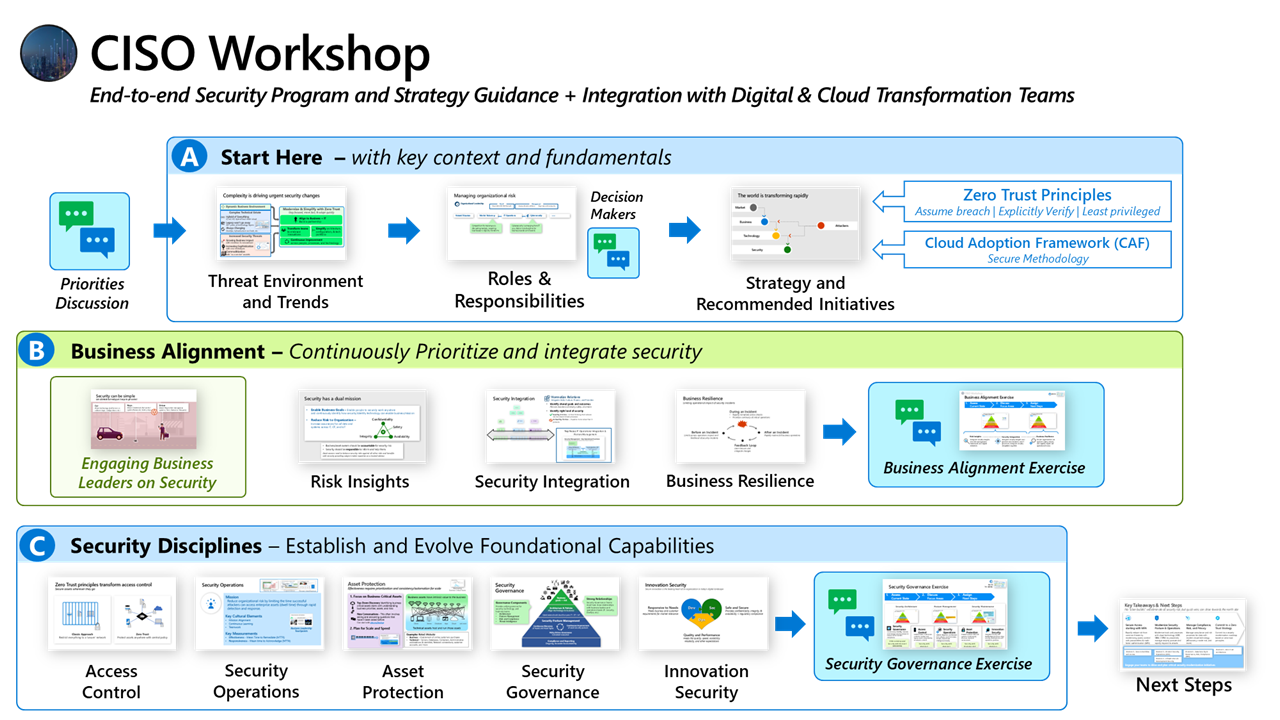
The CISO Workshop consists of a set of training materials, mostly videos, focusing on three areas:
- Part A: Key Context and Fundamentals
- Threat Environment and Trends
- Roles & Responsibilities
- Strategy and Recommended Initiatives
- Part B: Business Alignment
- Engaging Business Leaders on Security
- Risk Insights
- Security Integration
- Business Resilience
- Maturity Model for Business Alignment
- Part C: Security Disciplines
- Access Control
- Security Operations
- Asset Protection
- Security Governance
- Maturity Model for Security Governance
There is plenty of high-value, high-impact content to dive into and learn more about adopting proper security best practices and aligning your organization around sound security principles.
Closing thoughts and next steps
Increasing your security posture is an organization-wide responsibility, at all altitudes. However, as executives and IT- or security leaders, your leadership strengths will come to play to ensure you can motivate the organization to adopt and adhere to sound security policies and programs.
While you can enforce a lot of security through policies and automation, much is also about training for the users, and teaching them about risks and potential business impact.
If you're keen on seeing the NSA and CISA report of the most common cybersecurity misconfigurations in the wild, check this out:

Stay safe, stay secure, have fun!









Recent comments