Programmatically create Azure Container Instances and connect a Managed Identity
"This feature is currently in preview. Previews are made available to you on the condition that you agree to the supplemental terms of use. Some aspects of this feature may change prior to general availability (GA). Currently, managed identities on Azure Container Instances, are only supported with Linux containers and not yet with Windows containers."
- Microsoft Docs
Previously I wrote about a post explaining how to programmatically create new Azure Container Instances (ACI) that are connected to a specific Virtual Network, allowing communication with services and data that resides inside that network.
In this post I'm sharing a brief additional tip on how to connect a Managed Identity to the ACI programmatically upon creation. I am using User Assigned Managed Identity, as I'm re-using the identity across more than one instance - and the code is fairly straight forward here as well.
Like with the previous post, it is a good idea to get acquainted with:
- Microsoft.Azure.Management.ContainerInstance.Fluent SDK (NuGet)
- The
IAzureobject, where you'll get authenticated and get your connections wired up. - Read how to set up the Authentication and get your token here.
Get a Managed Identity using the Azure Fluent SDK
Before we continue, let's ensure we can get a reference to the IIdentity object. The IIdentity object represents my User Assigned Managed Identity.
Listing all Managed Identities in a Resource Group:
public async Task<List<IIdentity>> ListManagedIdentitiesInResourceGroup(string rgName)
{
var identities = await azure.Identities.ListByResourceGroupAsync(rgName);
return identities?.ToList();
}
Another example is to get a reference to an identity if you know the id:
var identity = await azure.Identities.GetByIdAsync("manage identity resource id")
As a reminder, the "resource id" is the full resource ID, like this:
/subscriptions/YOUR_GUID/resourceGroups/YOUR_RESOURCE_GROUP/providers/Microsoft.ManagedIdentity/userAssignedIdentities/your-identity
Create an IContainerGroup and attach a User Assigned Managed Identity
At this point we have already authenticated, and retrieved our IIdentity object, and we are ready to create our Azure Container Instance.
var containerInstance = azure.ContainerGroups.Define(containerGroupName)
.WithRegion(Region.EuropeWest)
.WithExistingResourceGroup(this.ResourceGroupName)
.WithLinux()
.WithPrivateImageRegistry(acrServer, acrUser, acrPass)
.WithoutVolume()
.DefineContainerInstance(containerGroupName)
.WithImage(containerImage)
.WithCpuCoreCount(2.0)
.WithMemorySizeInGB(2)
.Attach()
.WithRestartPolicy(ContainerGroupRestartPolicy.Always)
.WithExistingUserAssignedManagedServiceIdentity(identity)
.Create();
In the above code, the key line is the .WithExistingUserAssignedManagedServiceIdentity method, where I am connecting to my IIdentity object that we retrieved previously.
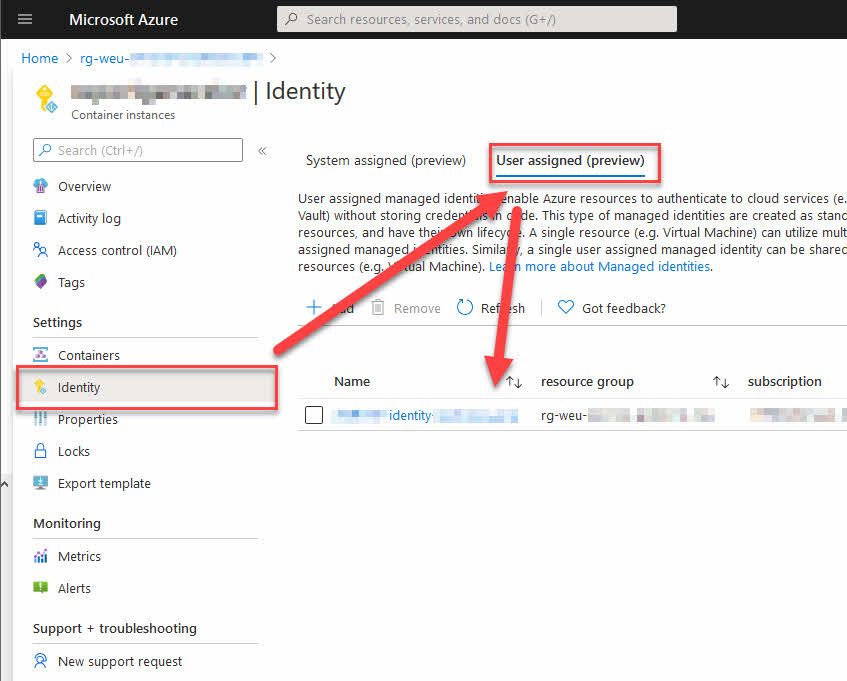
When I now create it, we can see that it works and the identity is connected:
Summary
Thanks for tuning in.
As a refresher, here are some interesting previous posts about Azure Container Instances and related topics:
- ACI - Using Managed Identity to access Key Vault secrets with C#
- ACI and Secrets - Creating secret volumes and consume secrets using C# .NET Core
- ACI and Secrets - Using Secure Environment Variables
- ACI and ACR - C# .NET Core apps running as containers in your private Azure Container Registry
Posts about Azure Container Registry:
- Best Practices for security in Azure Container Registry
- How Tokens and Scope Maps for Azure Container Registry introduces great repository-level access restrictions
- Thoughts on Bring Your Own Key, or BYOK, to Azure Container Registry
- Protecting your Azure Container Registry by denying all requests except from allowed IP addresses
More reading from Microsoft about Azure Container Instances and identities:
- How to use managed identities with Azure Container Instances (Microsoft Docs)








Recent comments