Favorite security-focused open-source workbooks for Azure Monitor and Microsoft Sentinel
Let's explore some of the Open Source workbooks that exist for Azure Monitor and Microsoft Sentinel. Why are they important to know about? What are some use cases? Read this article to understand some of my favorite use cases and well-used workbooks, tailored to my specific needs.
Table of Contents
I have previously talked about workbooks in various forms. For more insights into how they can be utilized, I recommend browsing through these posts.
- Visualize Log Analytics data ingestion using Microsoft Sentinel
- Discover sensitive Key Vault operations with Microsoft Sentinel
In this article, I will explore the concept of open-source workbooks for Azure Monitor, and why they are important to know about. I am also elaborating a bit about the use cases I have when working with these workbooks.
What are open-source workbooks?
Microsoft has a repository on GitHub, https://github.com/microsoft/Application-Insights-Workbooks, where you can find a big portion of ready-to-use workbooks.
These workbooks are open source, and you can modify them as you want to fit the needs of your organization. The benefit of these templates is that most of the grunt work has been done for many common tasks.
I initially wrote this as a draft in November 2021, when there were 349 workbooks in the library. Since then, it has had many updates indicating that the repository is well maintained.
- Explore all the workbooks (GitHub)
Since the GitHub repository doesn't come with any good insights into how each workbook looks, and what capabilities they offer, I will go through a few of my favorite workbooks below. But first, the why.
Favorite use cases
While there are features and capabilities, and a lot of workbooks at our disposal, it's always a good idea to step back and ask "Why?".
I want to highlight some use cases I find interesting and that would easily be applicable when I've worked with operating distributed cloud solutions. We'll later explore a few of these workbooks to get an understanding of how powerful they are.
These are workbooks I've used for real-world systems.
Use case: Get security insights
In one of my previous roles, security and compliance were fundamental aspects of daily routines. I planned, architected, deployed, and operated distributed cloud-native applications in Azure.
With a distributed workload that spans multiple subscriptions in various regions, it's essential to be able to keep tabs on what's happening cross-resources and cross-subscriptions.
Below is a list of a few of my favorite workbooks to get started with for building up security insights. Each section has multiple sets of workbooks from which we can learn.
The list is a catered list of things focusing on security that I've found interesting and that was a direct benefit for my role in securing and analyzing our cloud estate.
- Microsoft Defender for Cloud
- Active Alerts
- Compliance
- Container Security
- Coverage
- Governance
- Log4j
- Price Estimation
- Ransomware
- Secure Score
- System Updates
- Vulnerabilities
- Azure Active Directory Conditional Access
- By conditional access status
- By continuous access evaluation
- By grant controls
- Conditional Access Gap Analyzer
- Conditional Access Insights and Reporting
- Legacy Authentication
- Single Policy Insights
- Azure Active Directory
- App Consent Audit
- Auth Methods Activity
- AuthenticationPrompts
- IdentityProtection
- MultiFactorAuthenticationGaps
- SignIns Using Legacy Authentication
- Intune Compliance
- Compliance
Use case: Application Health
With cloud-native applications running in a distributed fashion, it can be tricky to keep a finger on the pulse at all times. While we have alerts and health indicators in Azure Monitor to help us with this, I also find these workbooks helpful to explore the insights interactively and to customize according to my common queries and troubleshooting guides that fit the organization's situation.
- Failures
- Failure Insights
- New Failures Analysis
- App Services - Infrastructure
- App Service HTTP Errors
- TSG (Troubleshooting Guide)
- Exceptions
- Request Failures
- Dependency Failures
While plenty of additional workbooks are available, these are some of the ones I will explore and elaborate on in this post.
How do you want to access your Workbooks?
You can add workbooks to Microsoft Sentinel or Azure Monitor as two examples. I've got workbooks deployed across these services in various instances, offering guidance and insights for different things.
You choose where you want to save your workbooks.
Read more about how to set up workbooks in these services:
- Sentinel: Use Azure Monitor workbooks to visualize and monitor your data.
- Azure Monitor: Azure Workbook templates.
When you've established how to add your custom workbooks to Azure Monitor or Microsoft Sentinel, you can use any of the open-source workbooks I mention here and quickly get them lit up in your Azure subscriptions.
Exploring some of the workbooks
I mentioned that many workbooks offer a wide range of use cases. I want to highlight some of the workbooks I've put to good use throughout managing distributed cloud environments.
This is only a partial list.
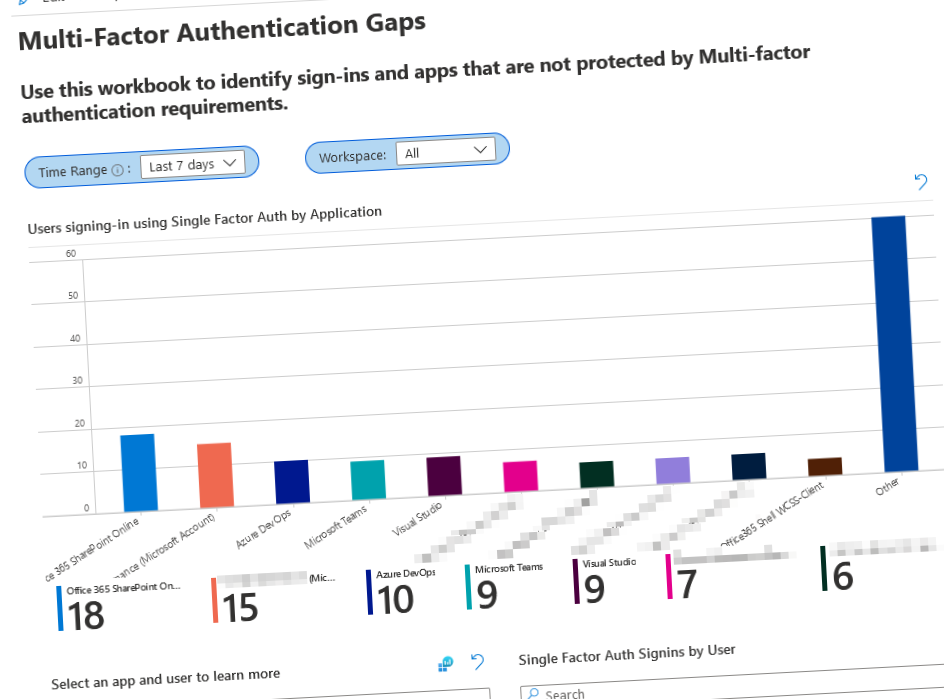
Workbook: Multi-Factor Authentication Gaps
See the latest version of the Multi-Factor Authentication Gaps workbook on GitHub.
There's an excellent workbook for precisely this purpose to explore gaps in Multi-Factor Authentication.
I'm exploring one of my research directories. The workbooks highlight the potential gaps in MFA, including which apps and users have used single-factor sign-in.
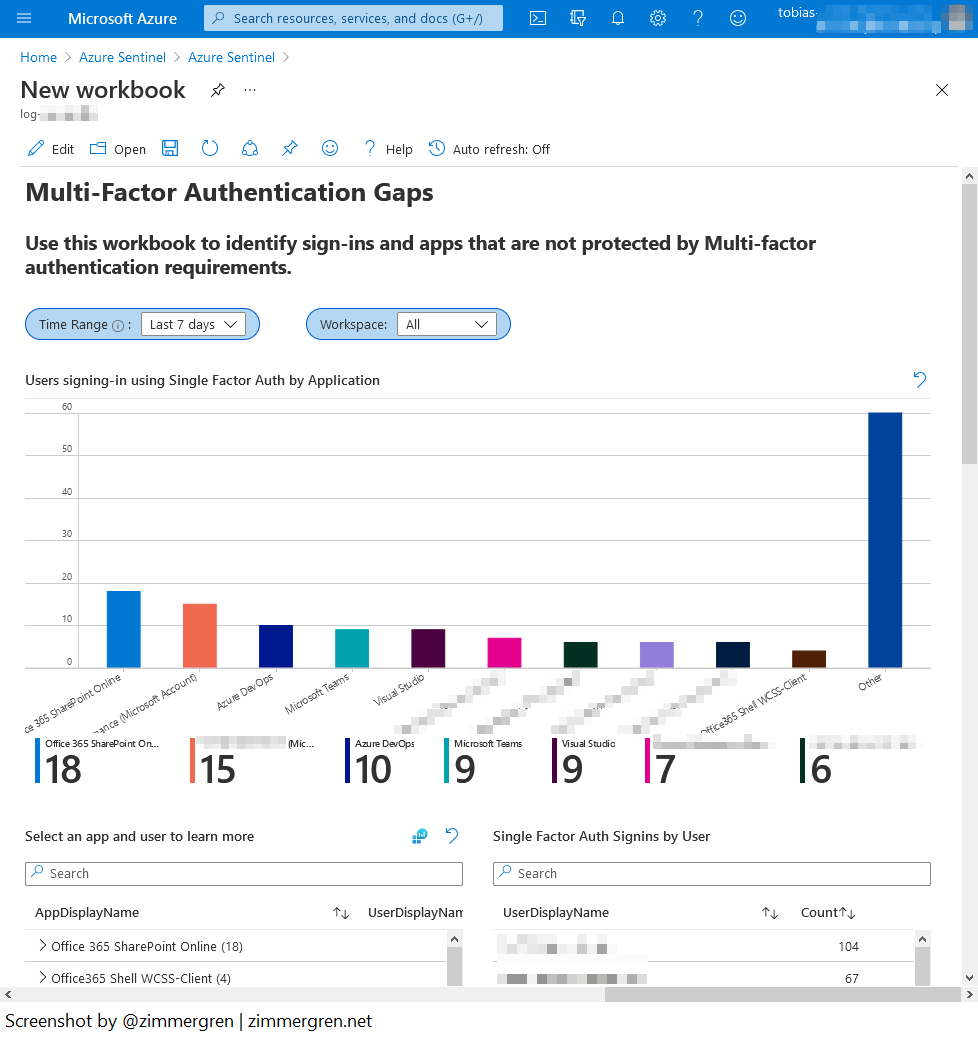
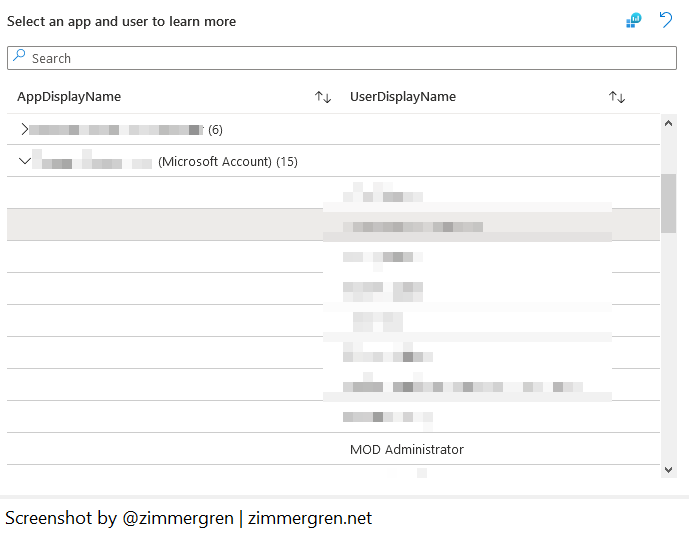
While I've redacted most of the details below, you can see that you've got the AppDisplayName and the UserDisplayName, indicating which users and apps lack proper MFA security configuration.
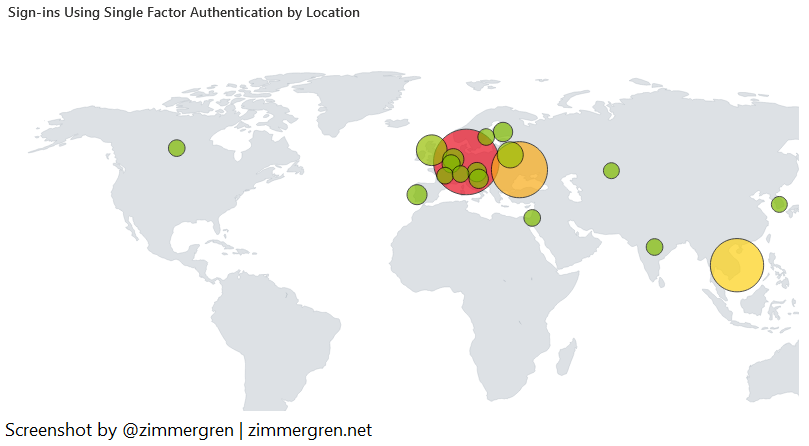
Further, this workbook shows the non-MFA sign-ins visualized on a map. I love this because it can help us better understand if location-based patterns of the issue are emerging.
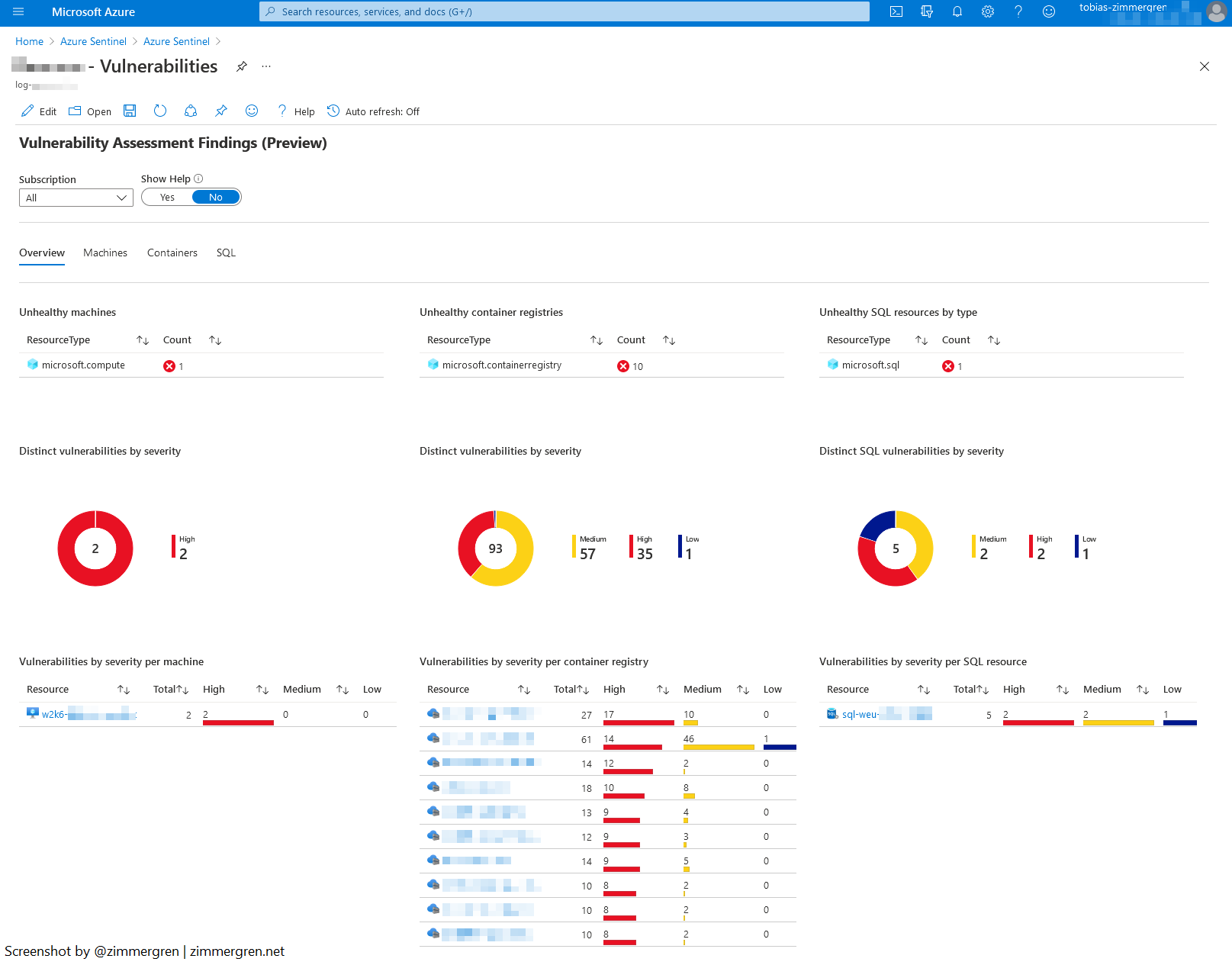
Workbook: Vulnerabilities
See the latest version of the Vulnerabilities workbook on GitHub.
Using the Vulnerabilities workbook gives you an easily digestible overview of vulnerabilities found across various resource types, including compute, containers, databases, and more. Microsoft Defender for Cloud has similar capabilities built-in, but these workbooks can easily be extended, which is one of my critical use cases.
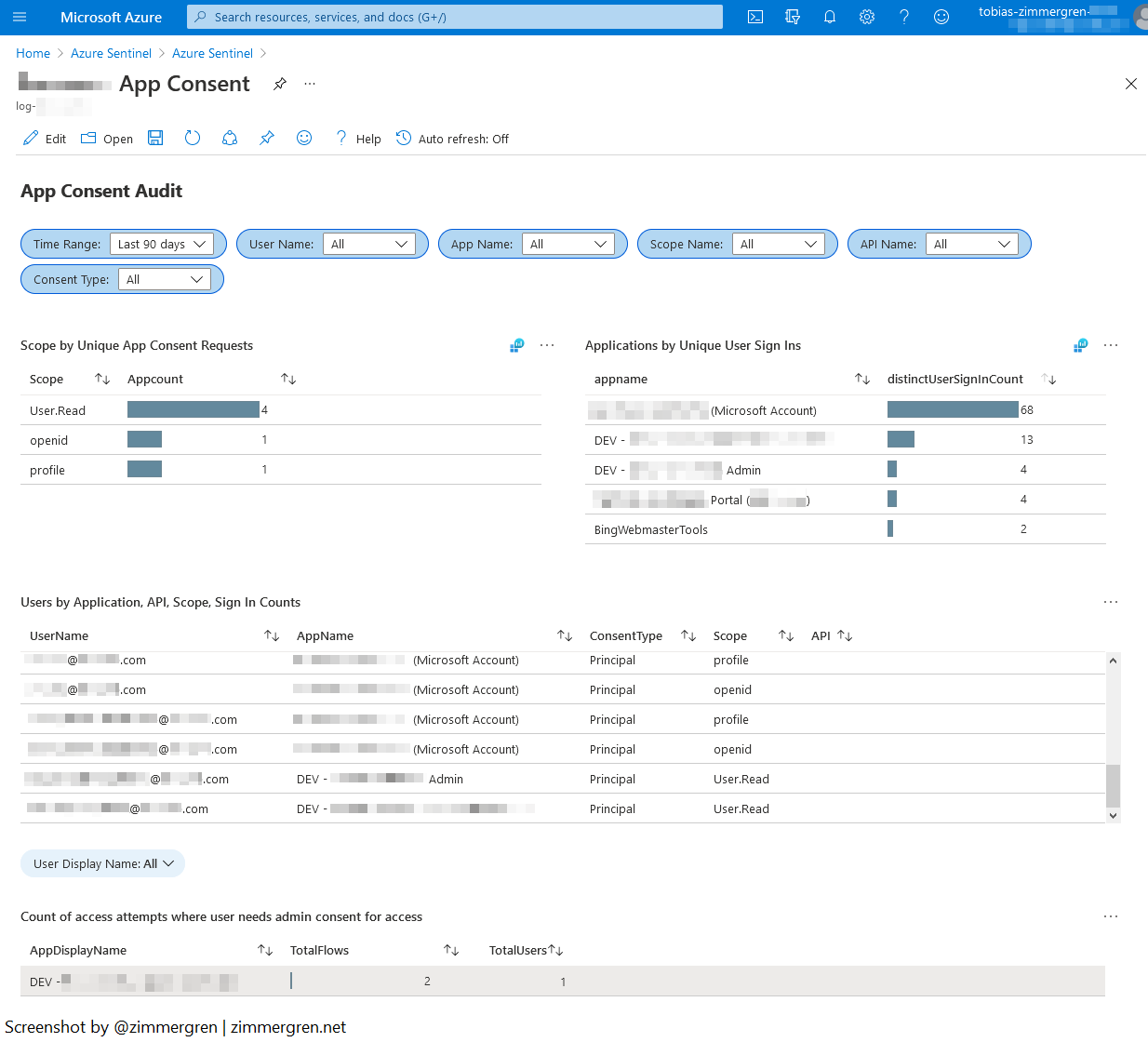
Workbook: Azure AD - App Consent Audits
See the latest version of the App Consent Audits on GitHub.
There are several excellent built-in queries in the workbook:
- Scope by Unique App Consent Requests.
- Applications by Unique User Sign-Ins.
- Users by Application, API, Scope, Sign In Counts.
- Count of access attempts where the user needs admin consent for access.
Importing the latest workbook from GitHub and viewing the data from one of my directories can look like this. From here, I can discover more about App Consent audit logs.
Visualizing and aggregating this information is crucial in the security operations of any business operating in the cloud. This exemplifies the importance of the Azure workbooks to achieve more with less.
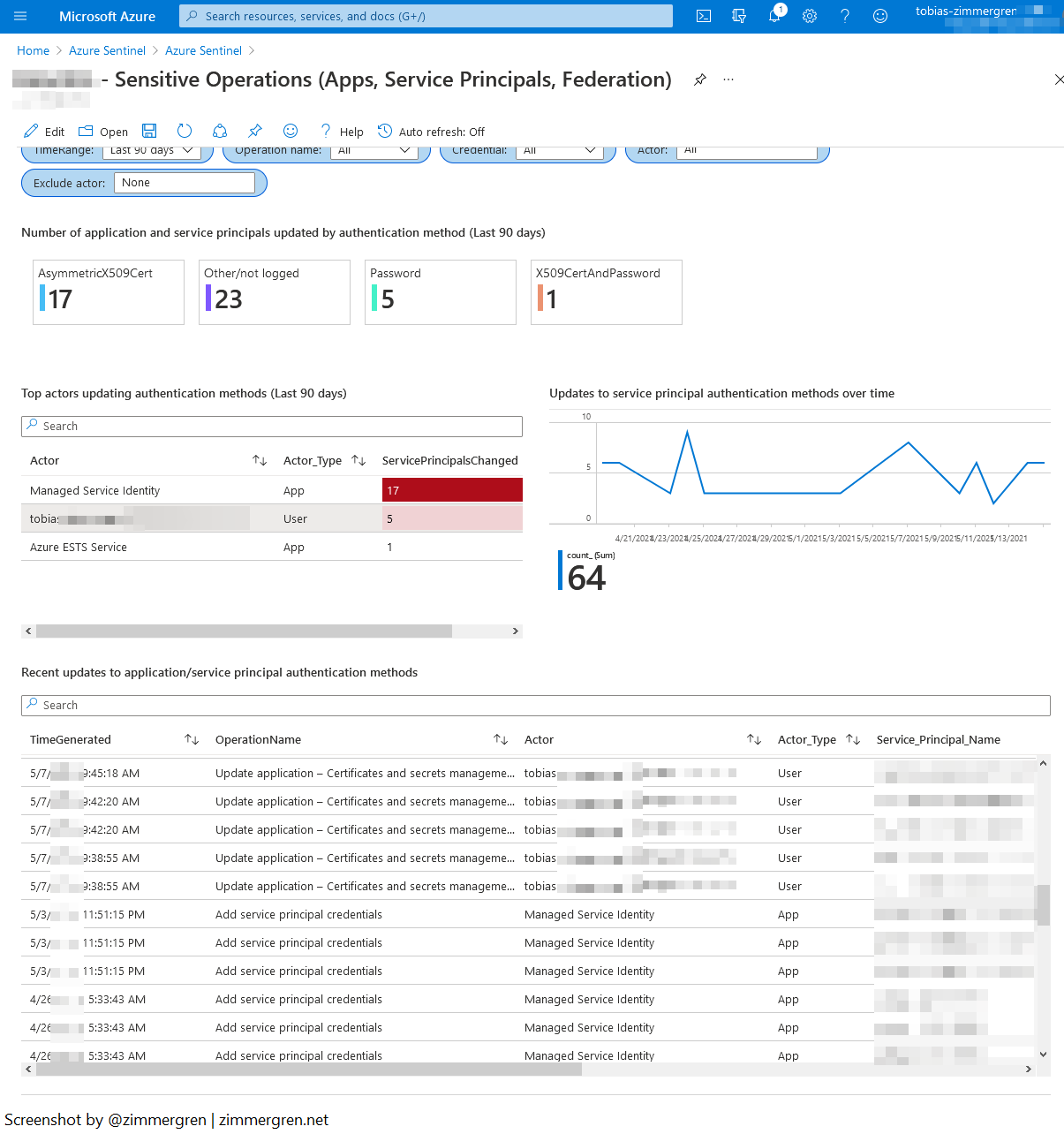
Workbook: Azure AD - Sensitive Operations
See the latest version of the Sensitive Operations workbook on GitHub.
Here's another workbook with great insights. With these four areas of insight, it offers important information about sensitive operations in our directory:
- Modified application and service principal credentials/authentication methods.
- New permissions were granted to service principals.
- Recent app permissions activity.
- Directory role and group membership updates to service principals.
- Modified federation settings.
Here's an example of what data the workbook pulls out of the logs.
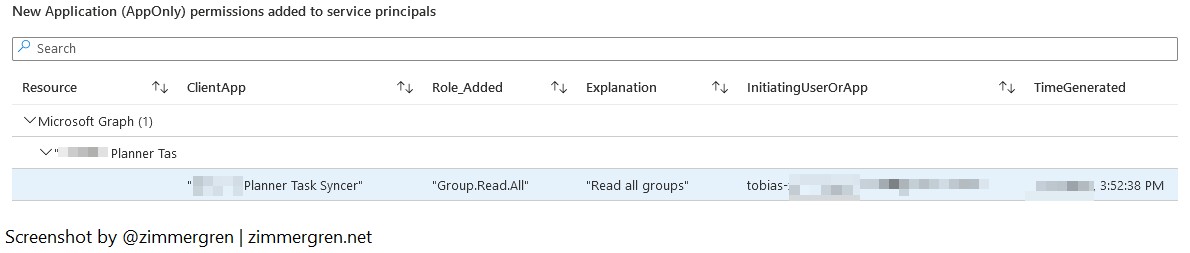
In my scenario, I have an app named "[XXXX] Planner Task Syncer", handling the syncing of Planner tasks across some of my M365 groups. The service principal has assigned the "Group.Read.All" permission, which you see in this workbook. Since this is a very permissive role assignment, it's even more important to stay on top of these inights.
Summary and links
There we have it. Running operations at scale in the cloud is both fun and challenging. I've done this a lot over the years, and every day has been a learning experience.
With proper tooling and insights, like Azure Monitor, Microsoft Sentinel, and open-source workbooks, we can better understand our cloud posture. If we have potential gaps, we need to address them.
Security and cloud posture improvement is a continuous journey, and we'll likely need to be fully taught. Keep learning, and keep sharing.
Check out these resources:






Recent comments