Security
Posts touching on Security in various angles lives in this category.
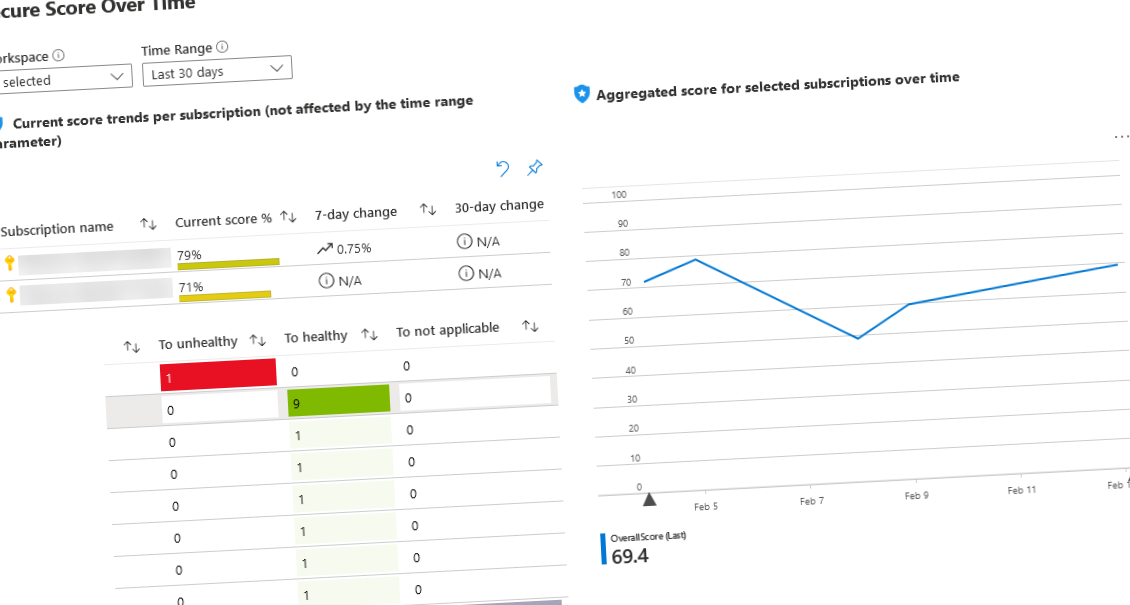
Track your Secure Score over time in Azure Paid Members Public
Use Microsoft Defender for Cloud continuous export to enable tracking of the historical Secure score in your Azure subscriptions.

Enforce authentication when sending Application Insights telemetry Paid Members Public
Microsoft recently announced the capability, and public preview, of authenticated requests to Application Insights. This is an important update for a wide range of reasons. In this post, we'll explore how to configure your Application Insights instance to reject requests that aren't authenticated and with the

Establish your organizational compliance readiness Paid Members Public
Wading through organizational change can be a challenge. Critical aspects of some of the challenges I've faced lately are security and compliance, and how to stay on top of sensible practices that can be applied across your organization. While there are great built-in capabilities and tools provided by
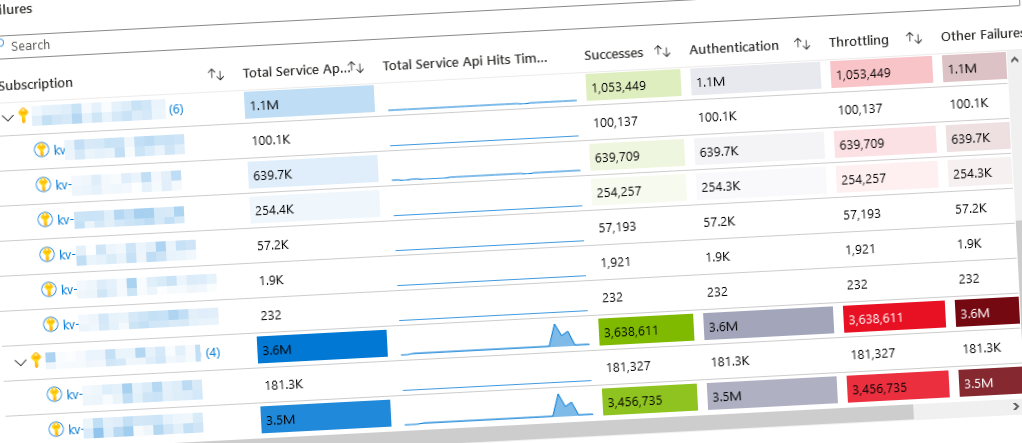
Discover sensitive Key Vault operations with Microsoft Sentinel Paid Members Public
Microsoft's Azure Key Vault Security workbook helps you structure the explorations of sensitive operations in your Azure Key Vaults. Using this workbook, we can cut the diagnostic and troubleshooting time down by a lot.

Securing Microsoft Teams Paid Members Public
Recently, Microsoft Teams adoption in organizations world-wide has skyrocketed. To keep up with this pace, here's a post about securing the Collaboration Experience, configuring Compliance, and a look at Security options!

Passing AZ-500: Microsoft Certified Azure Security Engineer Associate Paid Members Public
The AZ-500 is a great certification if you work with security and compliance. In this article I'm outlining my experiences in taking this exam online from my home office, as well as free official Microsoft documentation around the areas you'll be tested on.
GitHub Actions for Security Code Analysis Paid Members Public
Performing code analysis and security scans on your code is imperative to software craftsmanship. Over the years, I have had plenty of options for performing security scans, both with third-party vendors and open-source tools. I want to highlight some of my favorite GitHub Actions to run code analysis with a
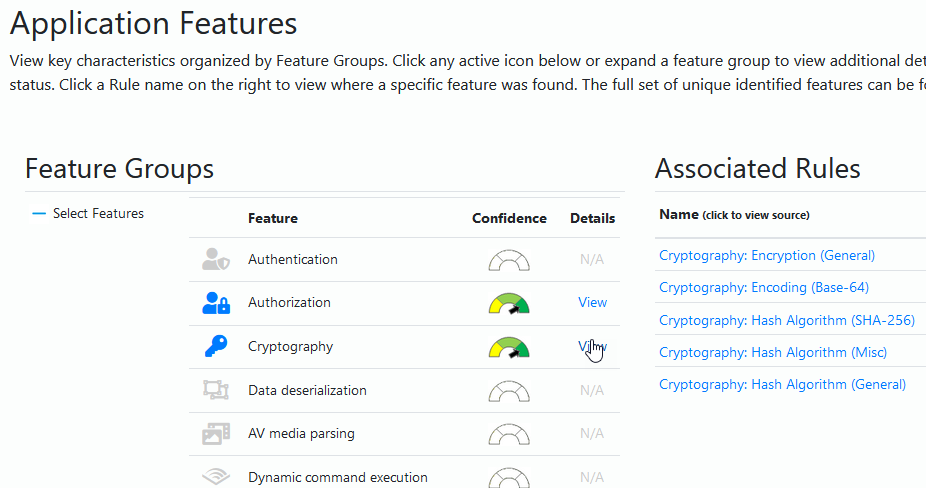
Use the Microsoft Application Inspector to analyze your source code Paid Members Public
Use the Microsoft Application Inspector to learn more about your code. Discover what types of algorithms, APIs, sensitive data and more that you make use of in the code base.





Recent comments