Security
Posts touching on Security in various angles lives in this category.
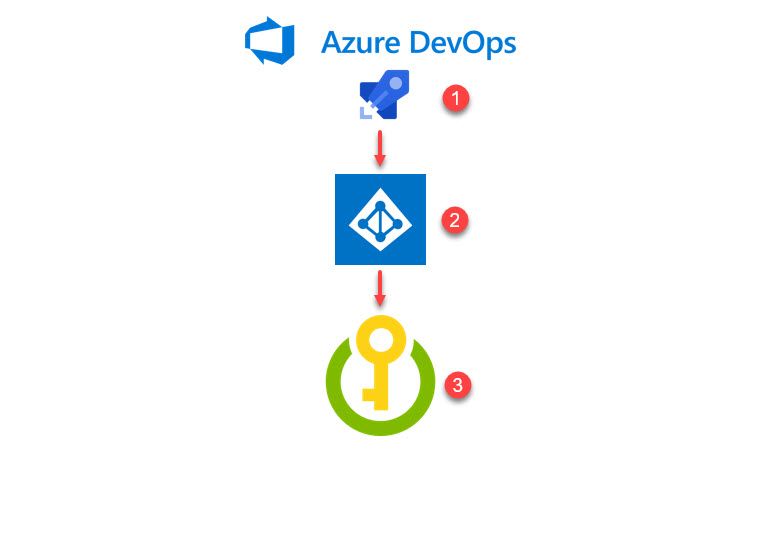
Using Azure Key Vault Secrets from your DevOps pipelines Paid Members Public
When working with Azure DevOps, there's a lot of options and configurations to tailor the service exactly to the needs of your organization. Part of the responsibilities that lie on the ones that managed these pipelines is to ensure that you don't spill the beans -
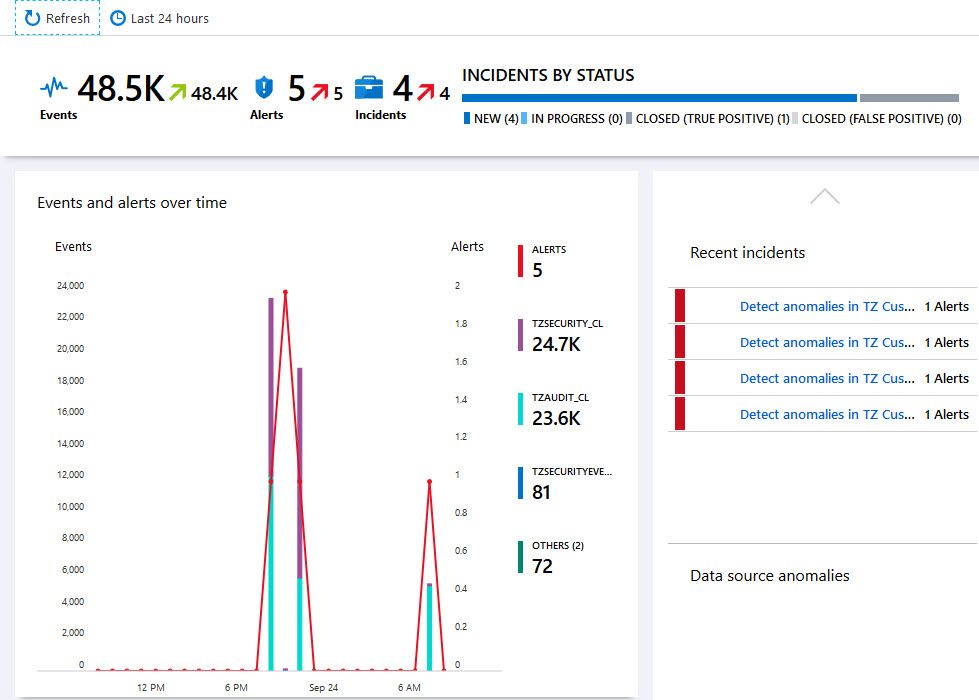
Log custom application security events in Azure Log Analytics which are ingested and used in Microsoft Sentinel Paid Members Public
A powerful capability of the Azure Sentinel [https://azure.microsoft.com/services/azure-sentinel/?WT.mc_id=ES-MVP-4021705] service is that you can ingest data from a wide variety of sources. Using Connectors [https://docs.microsoft.com/en-us/azure/sentinel/quickstart-onboard?WT.mc_id=ES-MVP-4021705#connect-data-sources] , you can even ingest data
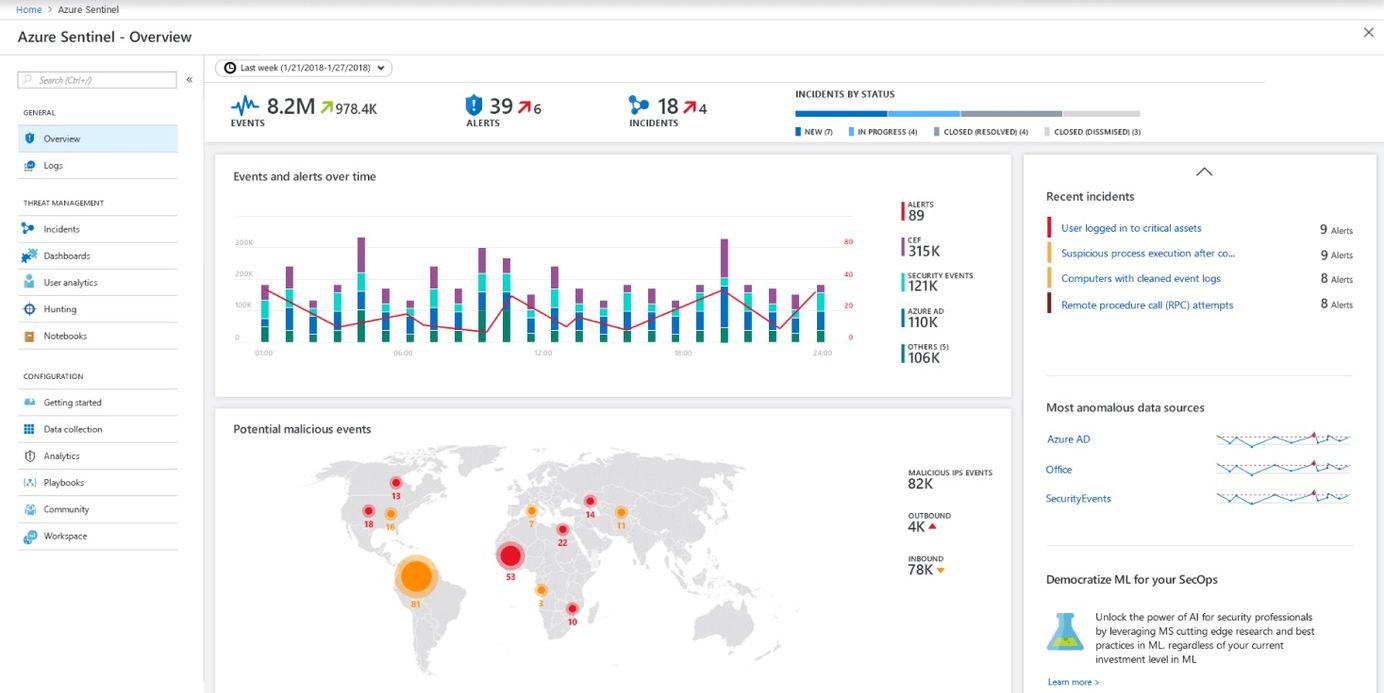
Monitoring Office 365 tenants with Azure Sentinel Paid Members Public
Azure Sentinel [https://azure.microsoft.com/en-in/services/azure-sentinel/?WT.mc_id=ES-MVP-4021705] is a product from Microsoft, offering a cloud-native SIEM service. Sentinel uses clever AI (Artificial Intelligence) to make your threat detection and responses faster and smarter. A key feature with Azure Sentinel is that you can connect

Who accessed my Azure Key Vault? Paid Members Public
In this post we'll discuss: * What is Key Vault, in case you landed here and you don't know. * Configure diagnostics logging for your vault * Querying the logs from your Azure Key Vault * Connecting Azure Monitor and Rules to set up Alerts * Get e-mails about any activity
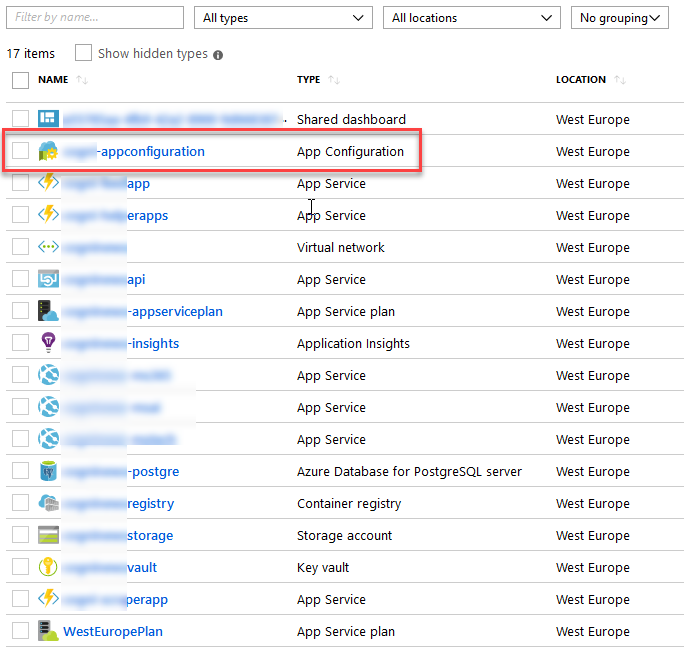
Introduction to Azure App Configuration for Developers with C# .NET Core Paid Members Public
Azure App Configuration helps us centralize configuration and makes it a lot easier to manage distributed apps, web sites, Functions, containers, your microservices and more.
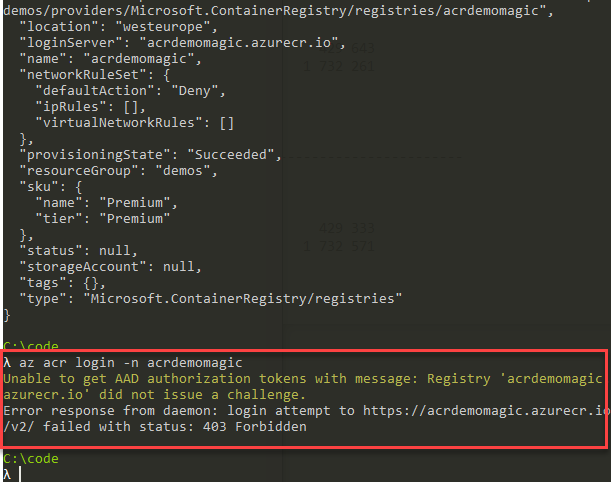
Protecting your Azure Container Registry by denying all requests except from allowed IP addresses Paid Members Public
With Azure Container Registry, or ACR, we get a lot of great capabilities to host our Docker images in the Azure cloud. With that, as with everything else, comes security concerns we should not overlook. In this post I'm exploring how we can lock down all access to
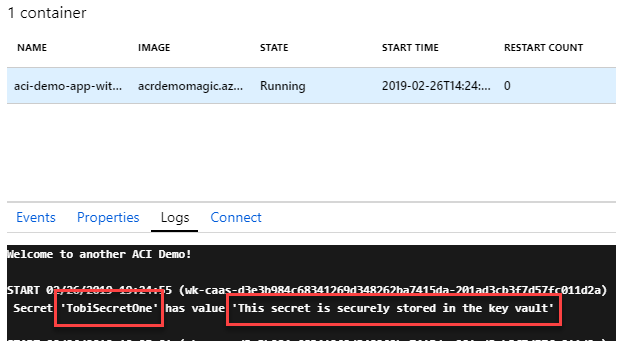
Azure Container Instances - Using Managed Identity to access Key Vault secrets with C# Paid Members Public
Azure Container Instances with Azure Managed Identity, accessing data in a Key Vault without using any stored credentials - all done in C# with .NET Core. Tag along!
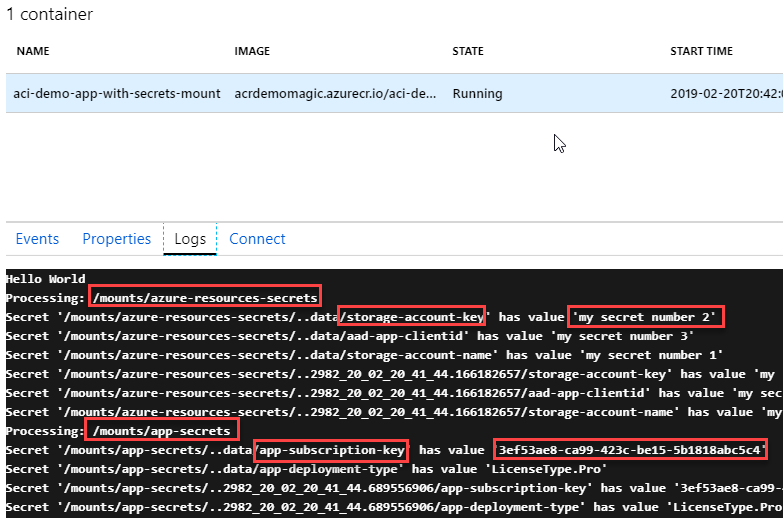
Azure Container Instances (ACI) and Secrets - Creating secret volumes and consume secrets using C# .NET Core Paid Members Public
A full guide to how you can define a Secret volume mount to your Azure Container Instances, and how you can read these secrets using C# with .NET Core. Stay secure out there!





Recent comments